Blog
 BulletProofLink Phishing-as-a-Service Came with 100+ Built-in Templates
BulletProofLink Phishing-as-a-Service Came with 100+ Built-in Templates
A new phishing-as-a-service (PhaaS) operation called “BulletProofLink” provides customers with over 100 templates mimicking popular brands and services.
Read more Should you backup your cloud communications and apps? The answer is yes, and here’s why.
Should you backup your cloud communications and apps? The answer is yes, and here’s why.
Do you really need to backup 'the cloud'? In this article, we talk about why cloud storage isn't 100% reliable and why SaaS (cloud-to-cloud) backup is needed.
Read more 6 Proven Tactics to Improve Work from Home Security
6 Proven Tactics to Improve Work from Home Security
Many businesses had no choice but to figure out how to go remote - some at the expense of sustainable security. Read a CIO's top security tips for remote work.
Read more Phishers Impersonate U.S. Transportation Department to Steal Victims’ Microsoft Credentials
Phishers Impersonate U.S. Transportation Department to Steal Victims’ Microsoft Credentials
Digital attackers launched a phishing campaign where they impersonated the U.S. Department of Transportation (USDOT) to steal victims’ Microsoft credentials.
Read more Griffon Backdoor Spread by FIN7 Using Multiple Lures
Griffon Backdoor Spread by FIN7 Using Multiple Lures
The cybercriminal group FIN7 has launched several email campaigns that use multiple lures to distribute its Griffon backdoor.
Read more Cryptocurrency Exchange SUEX Sanctioned by U.S. Treasury Department for Facilitating Ransomware Transactions
Cryptocurrency Exchange SUEX Sanctioned by U.S. Treasury Department for Facilitating Ransomware Transactions
The U.S. Department of the Treasury sanctions a cryptocurrency exchange for helping to facilitate the financial transactions of ransomware actors.
Read more Understanding the Threat Posed by an AI-Powered Spear Phishing Attack
Understanding the Threat Posed by an AI-Powered Spear Phishing Attack
Artificial intelligence is reshaping threats like spear phishing. Just as organizations use “defensive AI” to protect, attackers use “offensive AI” to automate.
Read more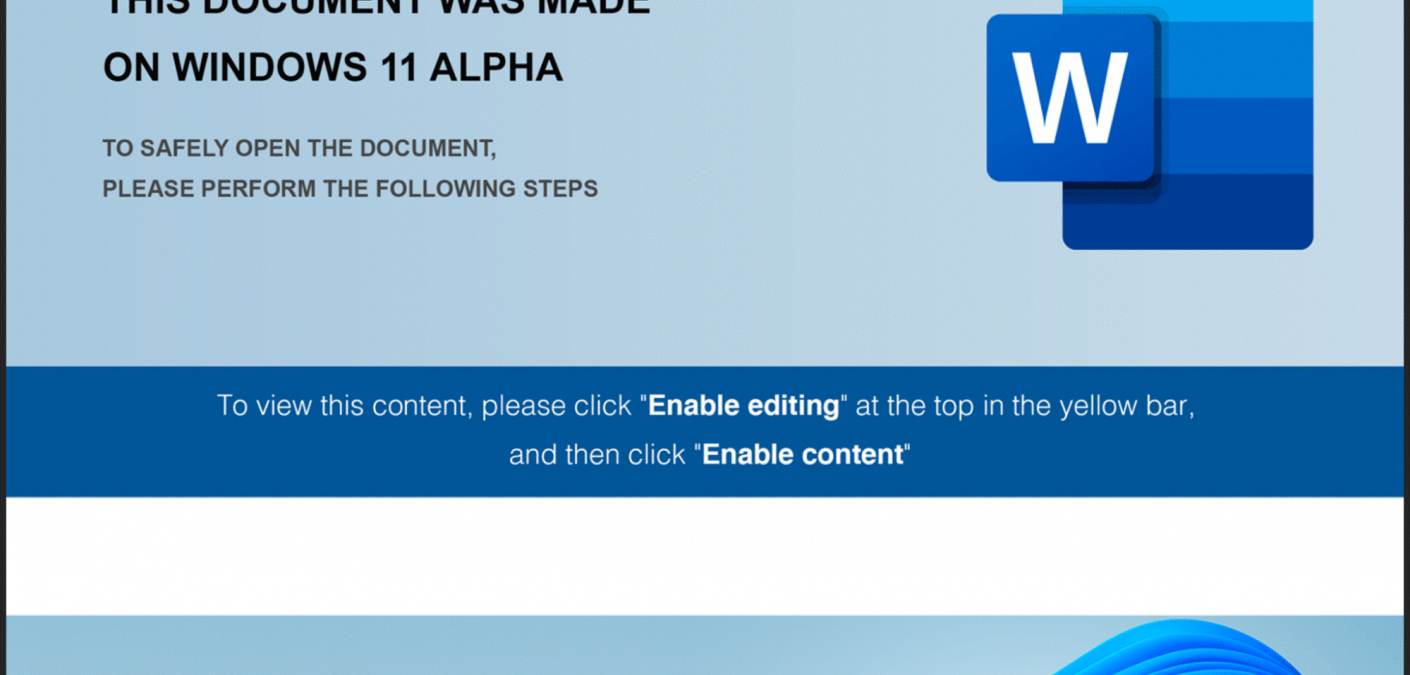 JavaScript Backdoor Delivered by Windows 11 Alpha-Themed Word Docs
JavaScript Backdoor Delivered by Windows 11 Alpha-Themed Word Docs
Malicious actors used Word documents carrying “Windows 11 Alpha” as their theme to deliver a JavaScript backdoor.
Read more 7 Attacks Where Phishers Abused Legitimate Microsoft Services
7 Attacks Where Phishers Abused Legitimate Microsoft Services
In a recent blog post, I discussed two email campaigns where attackers used Microsoft to steal recipients’ credentials.
Read more Microsoft-Themed Email Campaigns Using CodeSandbox, IBM Cloud to Host Phishing Sites
Microsoft-Themed Email Campaigns Using CodeSandbox, IBM Cloud to Host Phishing Sites
Digital attackers are using Microsoft-themed attacks emails to redirect victims to phishing sites hosted on CodeSandbox and IBM Cloud.
Read more Breaking Down Microsoft’s Updates: New Commerce Experience and Price Changes
Breaking Down Microsoft’s Updates: New Commerce Experience and Price Changes
Those of you in the Zix/AppRiver partner family know we pride ourselves on having your back and being Phenomenal everyday. This is one time that we feel you’ll really want to lean on our partnership as we guide you through the changes and the corresponding effect on your business.
Read more Why Ransomware Groups Are Rebranding Their Operations
Why Ransomware Groups Are Rebranding Their Operations
New penalties and attention from the Colonial Pipeline attack has caused difficulty for ransomware operations to continue, forcing them to change their names.
Read more



