Griffon Backdoor Spread by FIN7 Using Multiple Lures
The cybercriminal group FIN7 has launched several email campaigns that use multiple lures to distribute its Griffon backdoor.
Inside Four Lures of the Email Attack Operation
FIN7, which has stolen over a billion dollars since 2014, popped up on the radar of Zix | AppRiver in recent weeks when it witnessed the group sending out malspam emails leveraging various themes to its targets.
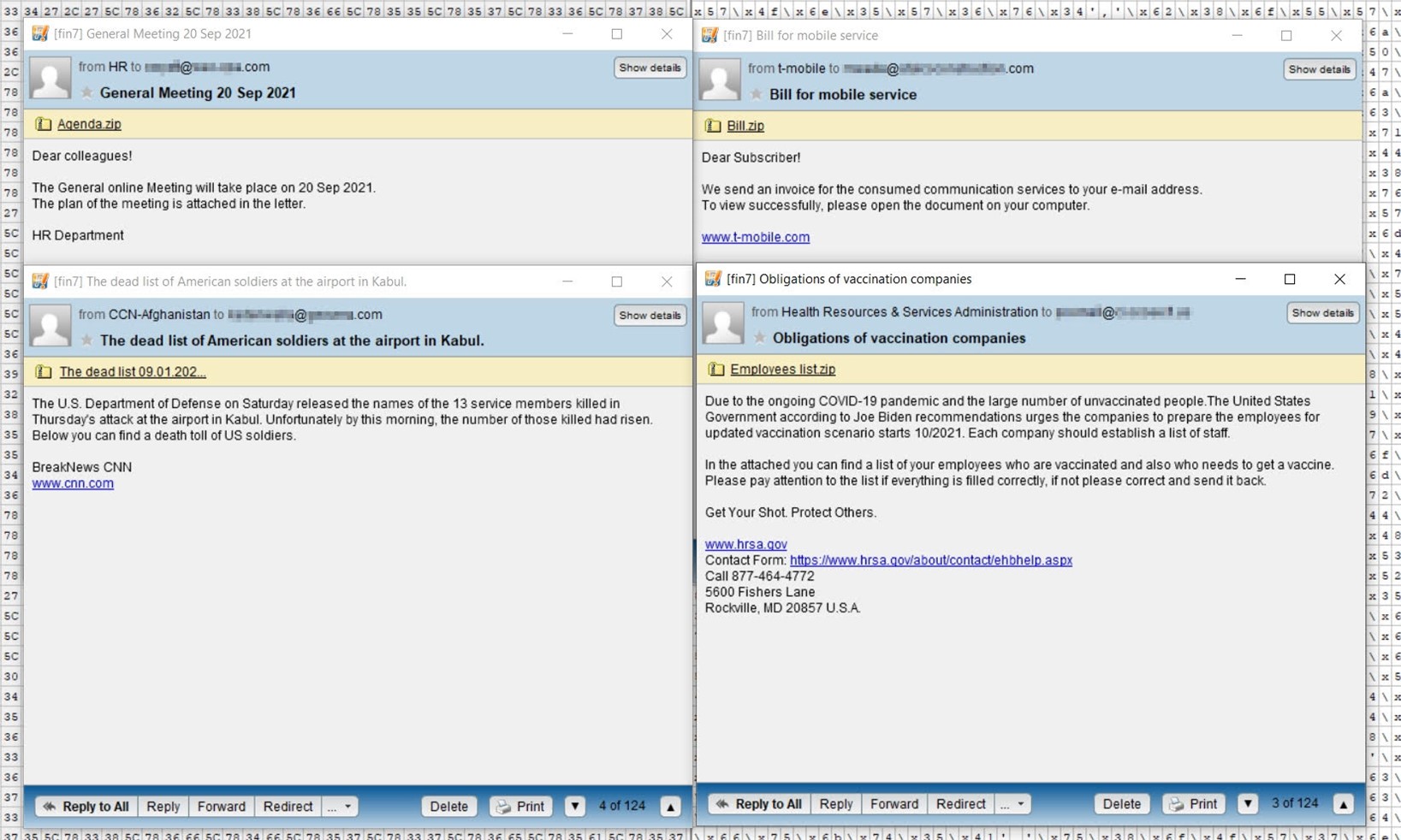
One of the emails appeared to come from an organization’s HR department. It arrived with the subject line “General Meeting 20 Sep 2021,” and it used a fake online meeting as a lure to trick the recipient into opening what they thought was an attachment containing the meeting agenda.
The attackers masqueraded as T-Mobile in another wave of attack emails containing the subject line, “Bill for mobile service.” In their messages, the malicious actors informed the recipient that the mobile service provider had sent “an invoice for the consumed communication services.” They then prompted the recipient to open a .ZIP archive named, “Bill.zip.”
In its third attack campaign, FIN7 used spoofing techniques to disguise their emails as having originated from the Health Resources & Services Administration, an agency which is part of the U.S. Department of Health and Human Services (HHS). The group used that lure to send out what they claimed was a list of the recipient’s vaccinated employees. It asked the recipient to review this information in an attachment named, “Obligations of vaccination companies.”
The final wave of emails detected by the Zix | AppRiver team used an attack that killed 13 U.S. service members at the airport in Kabul as a lure. Those who crafted the messages claimed that the number of those killed had grown. From there, they invited the recipient to open an attachment for more information.
Each of the messages sent out FIN7’s JavaScript-based Griffon backdoor inside the .ZIP archives. Those files used hex obfuscation to obscure their functions, thereby helping the campaigns to evade detection from traditional email security solutions.
FIN7’s Recent Threat Activity
This isn’t the only time that Zix | AppRiver has come across FIN7’s handiwork. Back in late June, for instance, the security firm flagged an email that appeared to come from a spirits and wine company. The message used the company’s branding and contact information to trick the recipient into clicking on a hyperlinked button. Once clicked, the button redirected the recipient to a lookalike website hosting JSSLoader, a remote access tool (RAT) used by FIN7.
Zix | AppRiver detected that attack email approximately two months before the spirits and wine company suffered a REvil ransomware attack. It’s unclear whether FIN7 cooperated with REvil in that case. But Troy Gill, senior manager of threat intelligence at Zix | AppRiver, clarified that “FIN7 has been linked to working with the REvil ransomware group after access was gained for follow-up big game ransomware deployments.”
As reported by The Record, REvil resumed operations in early September after going offline in July following the Kaseya supply chain attack.
How to Defend Against Emails Carrying FIN7’s Malware
The attack emails discussed above highlight the need for organizations to defend themselves against FIN7’s evolving operations. One of the ways they can do that is by investing in an email security solution that scans for campaign patterns, malware signatures, IP addresses, and other threat indicators in real time. This will ensure that legitimate business correspondence can reach its intended destination.
Learn how Zix | AppRiver can help to keep you safe against FIN7.
