Blog
 Record-Setting DDoS Attack Highlights Malicious Actors’ Strategic Thinking
Record-Setting DDoS Attack Highlights Malicious Actors’ Strategic Thinking
In mid-October, Microsoft revealed that it had succeeded in mitigating a 2.4 Tbps distributed denial-of-service (DDoS) attack against its own infrastructure.
Read more Your IT Project Cheat Sheet
Your IT Project Cheat Sheet
What does it take for an IT project to be successful? In this blog a program director answers questions like who should be involved and which plan model to use.
Read more 3 Recent Attacks Where Phishers Abused Google’s Services
3 Recent Attacks Where Phishers Abused Google’s Services
Read about 3 recent cyber attacks where Google was leveraged and abused - and get prepared for upcoming threats around new Google 2FA requirement.
Read more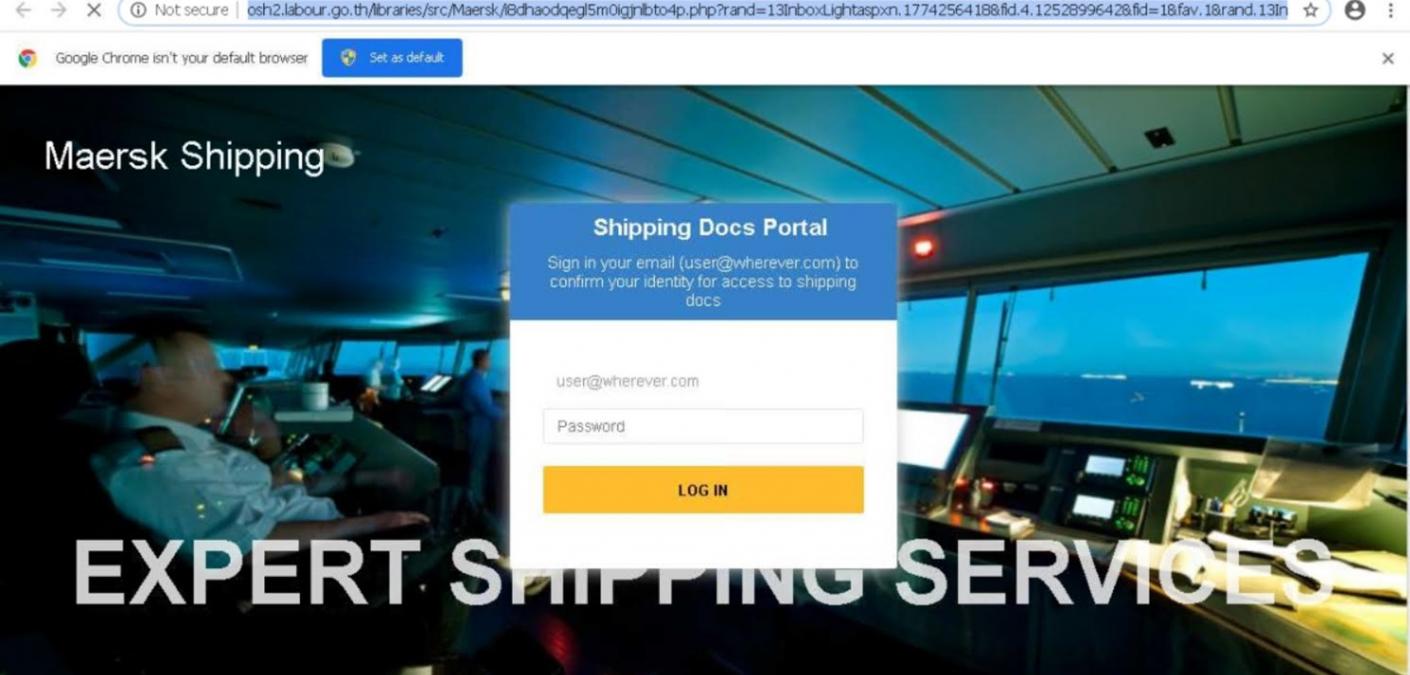 Phishers Impersonating Maersk Line to Steal Victims’ Email Credentials
Phishers Impersonating Maersk Line to Steal Victims’ Email Credentials
Phishers launched an attack campaign impersonating Danish international container shipping company Maersk Line to steal victims’ email account credentials.
Read more 5 Types of Phishing and How To Spot Them A Mile Away
5 Types of Phishing and How To Spot Them A Mile Away
Learn what different types of phishing attacks can look like and how to help your team avoid falling for them.
Read more What Does Encrypted Email Really Mean?
What Does Encrypted Email Really Mean?
If you want your email to be secure, then adopting encrypted email practices is critical.
Read more What Is Spoofing and Does My Team Need To Be Concerned?
What Is Spoofing and Does My Team Need To Be Concerned?
Spoofing is the insidious act of disguising a communication from an unknown source as being from a known, trusted source.
Read more Understanding Digital Attackers’ Appropriation of the “As a Service” Model
Understanding Digital Attackers’ Appropriation of the “As a Service” Model
Recently, I wrote about Microsoft’s discovery of a new phishing-as-a-service (PhaaS) offering called “BulletProofLink.” PhaaS functions similarly to
Read more What is Ransomware, How to Prevent It, and How to Respond If You're Attacked
What is Ransomware, How to Prevent It, and How to Respond If You're Attacked
What is ransomware? This blog tells you what it looks like, how to avoid it, and ways to recover.
Read more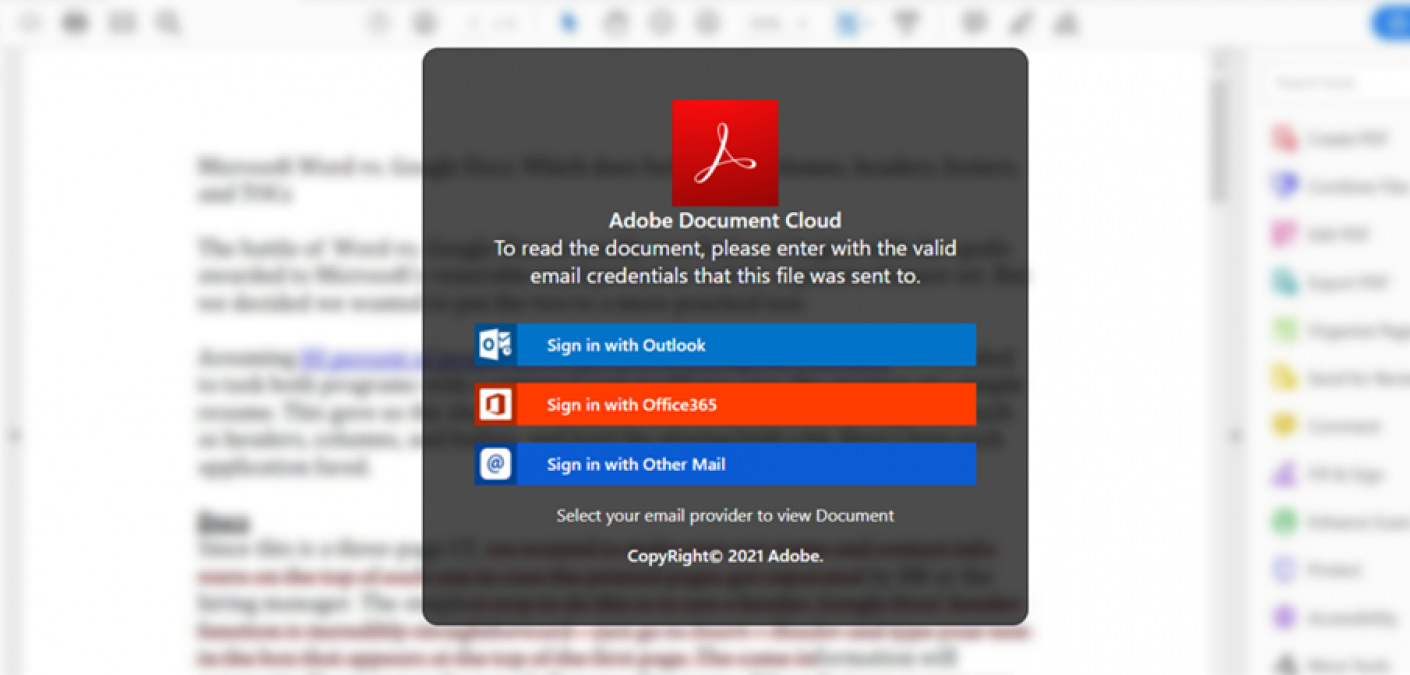 DocuSign Abused by Phishers to Target Victims’ Email Account Credentials
DocuSign Abused by Phishers to Target Victims’ Email Account Credentials
Digital attackers launched a phishing campaign in which they abused DocuSign to steal victims’ email account credentials.
Read more Bill Would Require Victims to Disclose Ransomware Payments in 48 Hours
Bill Would Require Victims to Disclose Ransomware Payments in 48 Hours
A proposed bill would require victims of ransomware to disclose that they had paid a ransom within a 48-hour window.
Read more Is Verticalization the Right Strategy for MSP Growth?
Is Verticalization the Right Strategy for MSP Growth?
Is choosing to specify in a specific vertical the best strategy for MSPs to grow their business? We spoke with a MSP leader to learn about the pros and cons.
Read more



