BulletProofLink Phishing-as-a-Service Came with 100+ Built-in Templates

A new phishing-as-a-service (PhaaS) operation called “BulletProofLink” provides customers with over 100 templates mimicking popular brands and services.
An Overview of How PhaaS Works
PhaaS functions like Ransomware-as-a-Service in that it follows the software-as-a-service model. Per Microsoft, PhaaS groups provide template creation, hosting, and orchestration capabilities to their customers. These offerings lower the barrier of entry for someone looking to launch their own phishing campaigns.
Not all digital crime services are the same, however. RaaS operations enable attackers to access victims’ devices, but PhaaS schemes don’t. The latter only provide customers with untested credentials stolen from their victims.
Analyzing BulletProofLink’s Functionality
Microsoft reviewed the templates, services, and pricing structure offered by the BulletProofLink group. In the process, it found that the operation’s infrastructure included multiple sites maintained under several aliases such as “BulletProftLink.” Those sites included YouTube and Vimeo pages offering instructional ads. The groups infrastructure also included an online store that customers could use to register an account and sign up for a monthly subscription.
As you can see below, BulletProofLink went so far as to offer a 10% discount to new customers.
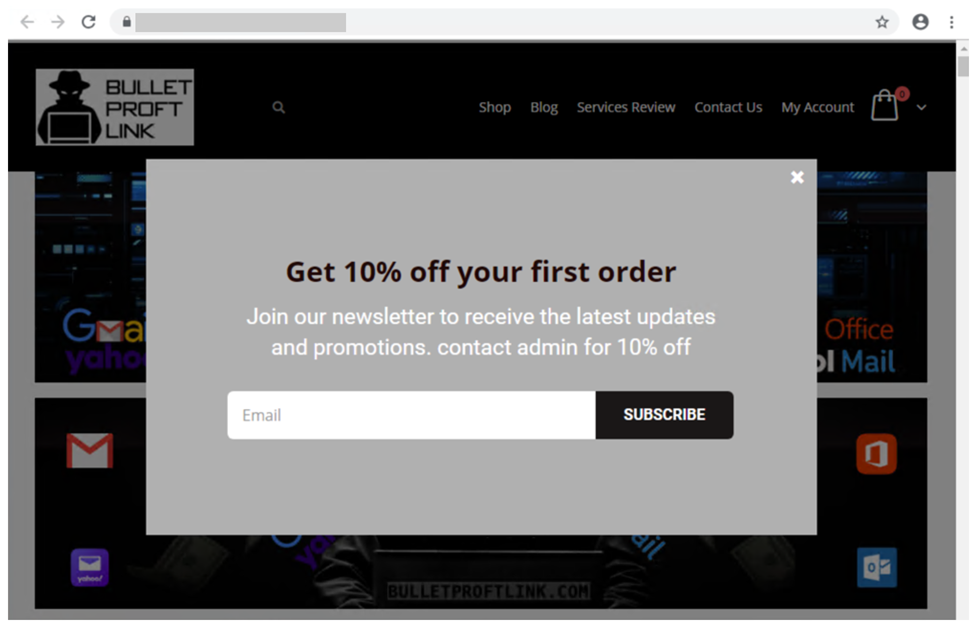
In its analysis of the operation, Microsoft found that BulletProofLink came with over 100 phishing templates for mimicking trusted entities such as mobile service providers, bank holding companies, international shipping organizations, electronic document services, and tech giants.
Whoever designed the operation’s templates did so to help them to evade detection from traditional security tools. Even so, they weren’t completely undetectable.
“… [T]he campaigns themselves can be identified with a mixture of phishing page source code, combined with the PHP password processing sites referenced therein, as well as the hosting infrastructure used in their larger-scale campaigns,” Microsoft clarified in its analysis. “These password-processing domains correlate back to the operator through hosting, registration, email, and other metadata similarities during domain registration.”
The Redmond-based company also found that BulletProofLink offered various hosting and support options to their customers…not to mention tiers of support. The PhaaS setup cost customers as much as $800 a month, for instance, while a one-time hosting link cost customers approximately $50. In the event one of their customers had a question, BulletProofLink’s handlers made it possible for them to get in contact using various methods including Skype, ICQ, forums, and chat rooms.
Analyzing a Campaign Created Using BulletProofLink
Microsoft examined one campaign that used the BulletProofLink phishing kit. It found that the attack impersonated its own logo and branding to convince the recipient that their password had expired. It then informed the recipient that they could change their password or continue using their current password by clicking on a hyperlinked “Keep Active Password” button.
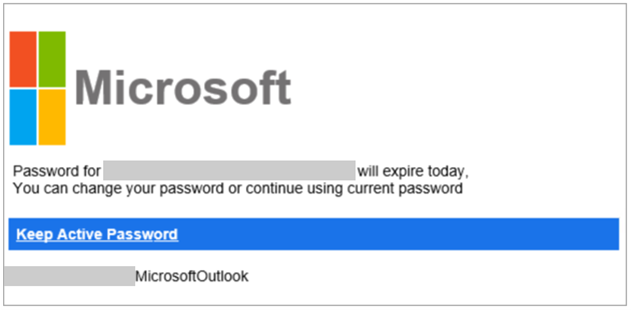
If clicked, the campaign redirected the recipient to an attacker-owned site that subsequently sent them to another site hosting the phishing page. That location contained a fake Outlook sign-in form. With the help of user-specific URLs and other tactics, the page stole the victim’s details.
How to Defend Against BulletProofLink-Enabled Campaigns
PhaaS operations such as BulletProofLink highlight the need for organizations to strengthen their email security posture. One of the ways that organizations can do that is by investing in an email security solution that’s capable of looking at multiple elements of an incoming email message such as campaign patterns, malicious IP addresses, and malware signatures. Such a tool should operate in real time so that regular business correspondence is unimpeded.
Defend against the rise of PhaaS groups like BulletProofLink with Zix | AppRiver.
