JavaScript Backdoor Delivered by Windows 11 Alpha-Themed Word Docs
Malicious actors used Word documents carrying “Windows 11 Alpha” as their theme to deliver a JavaScript backdoor.
Inside the Infection Chain
In the beginning of September, Anomali Threat Research revealed that it had discovered six Windows 11-themed Word documents.
The researchers analyzed the file names of those documents. Subsequently, they found evidence to suggest that those responsible for having crafted the documents did so in July 2021.
Their analysis also highlighted a phishing or spear phishing campaign as the most likely attack vector, though Anomali’s teams noted that they couldn’t say for sure.
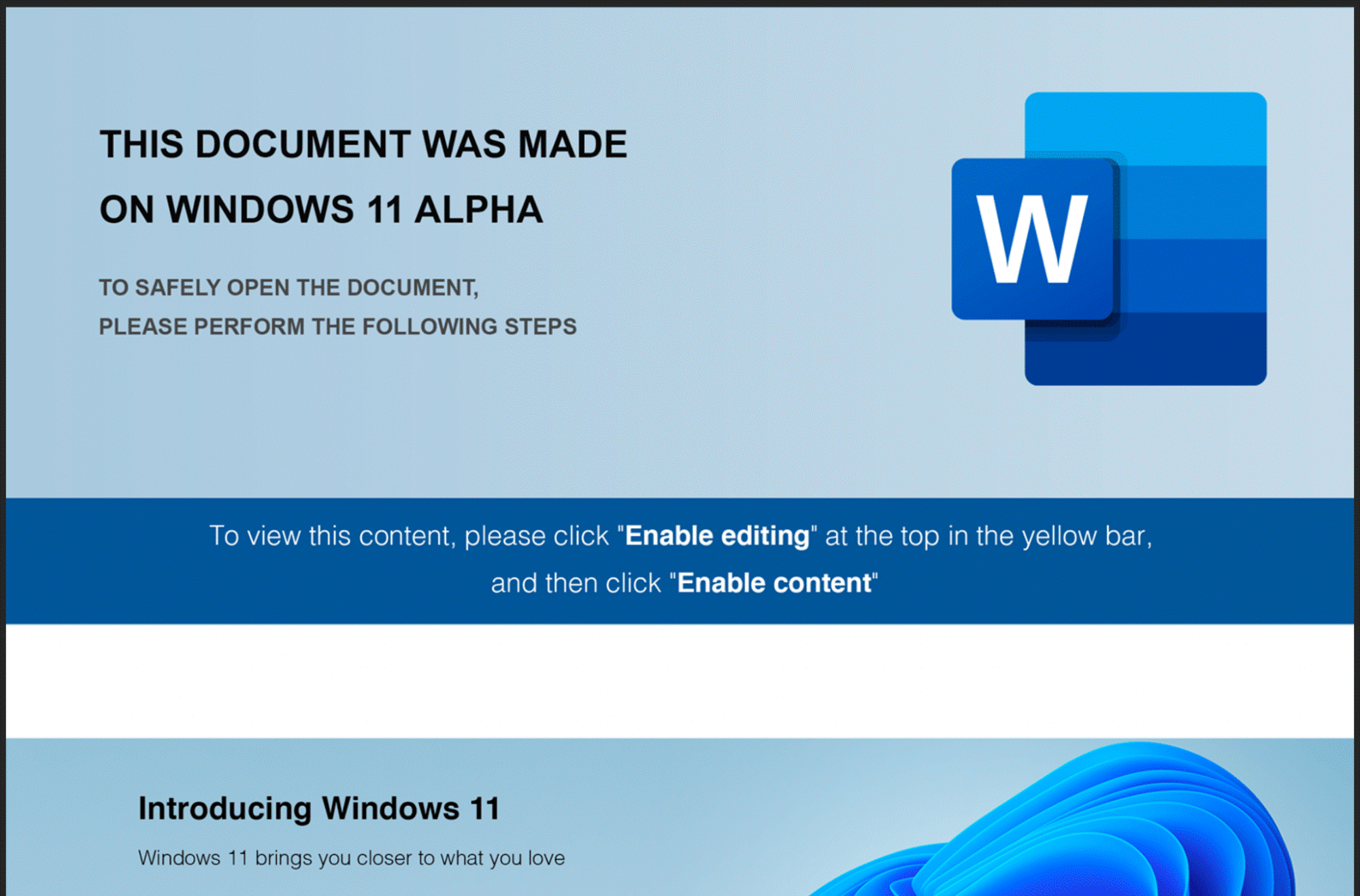
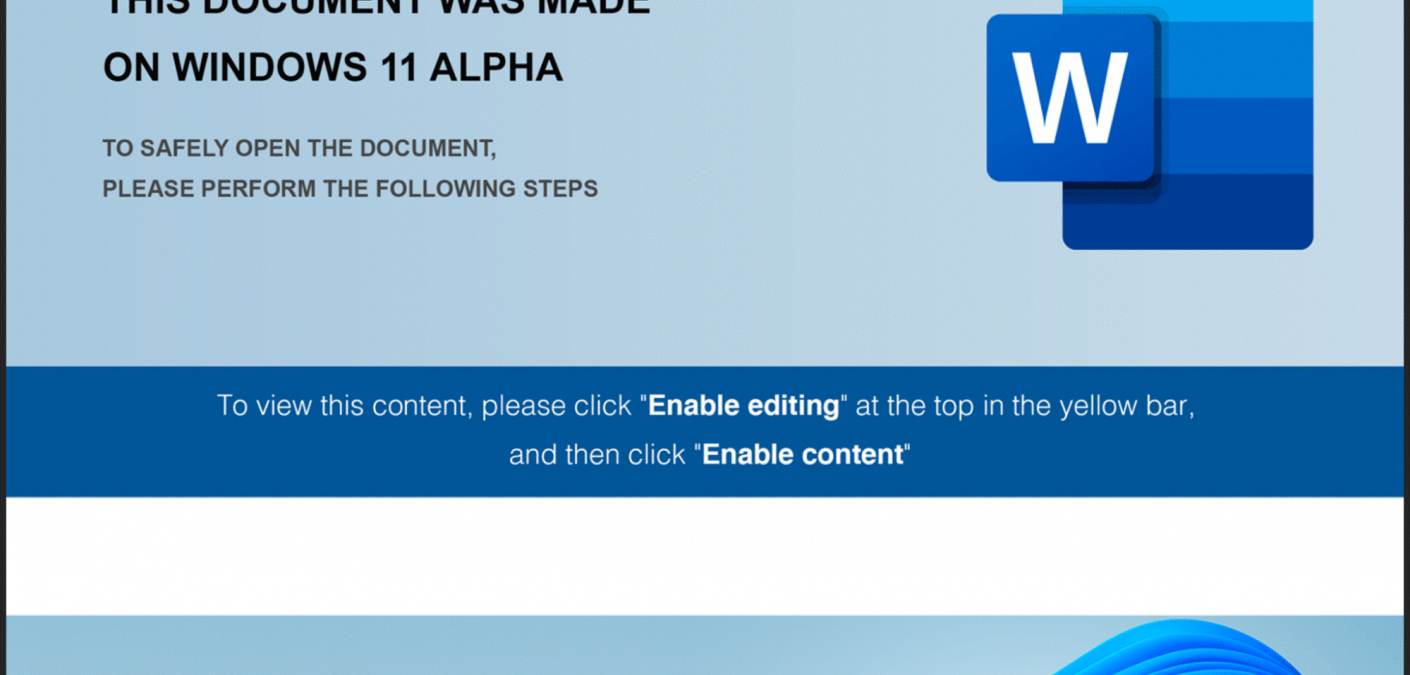
Anomali found that the infection chain began with a Windows 11-themed Word document.
As shown in the screenshot above, the document specifically mentioned “Windows 11 Alpha.” It’s important to note that Microsoft has announced no such version of its new OS.
Once opened, the Word document asked the user to click the “Enable Editing” or “Enable Content” button. Compliance caused the campaign to execute an Office Visual Basic for Applications (VBA) macro populated with junk data as comments.
That junk data helped to shield the macro—and the attack more broadly—from analysis.
Upon execution, the VBScript retrieved encoded values from a table hidden inside the malicious Word document. It used those values to check for virtual machines as well as “CLEARMIND,” the domain name of a Point-of-Sale (POS) service provider.
If its checks found no issue, the VBScript used a function to drop a JavaScript file called “word_data.js” into the infected machine’s TEMP folder. If it did, the VBScript stopped running, the hidden table deleted itself, and the campaign didn’t proceed to the JavaScript payload.
The JavaScript file also arrived with junk data for the purpose of installing a backdoor.
Connection to a Well-Known Threat Actor
In its analysis, the Anomali Threat Research team found several threat indicators that tied the campaign to the financially motivated threat group FIN7.
One piece of supporting evidence was the decision by the attack operators to target a POS technology provider like Clearmind. If successful, malicious actors could steal customers’ payment details, leverage them to commit credit card fraud, and monetize them on the dark web.
There’s also the fact that the phishers used a JavaScript backdoor. This campaign pattern is commonly associated with FIN7.
For its part, the Zix | AppRiver team detected a JavaScript backdoor back in June after it flagged a malicious email that appeared to have arrived from a spirits and wine company.
The attack email used spoofing techniques and stolen branding to trick recipients into interacting with a hyperlinked button. If clicked, the button redirected the recipient to a malicious website that dropped JSSLoader.
Morphisec analyzed a sample of JSSLoader back in December. Its researchers found that FIN7 is the primary operator of the .NET RAT backdoor. They also discovered that the group’s members have periodically updated their malware with minimal anti-debugging features, exfiltration capabilities, persistence techniques, and the ability to conduct remote code execution.
Defending Against Email-Borne Backdoors
The Windows 11 Alpha campaign described above underscores the need for organizations to defend themselves against email attacks. They can do this by investing in an email security solution that’s capable of scanning incoming messages for campaign patterns, malware signatures, IP addresses, and other threat indicators. This tool should conduct its analysis in real time so that legitimate correspondence can reach its intended destination unimpeded.
