Microsoft-Themed Email Campaigns Using CodeSandbox, IBM Cloud to Host Phishing Sites

Digital attackers are using Microsoft-themed attacks emails to redirect victims to phishing sites hosted on CodeSandbox and IBM Cloud.
Email Campaign #1: A Phishing “Proposal”
Near the end of August, the Zix | AppRiver team flagged a OneDrive-themed attack email that had originated from Russia.
How do we know this? The email used spoofing techniques to trick the recipient into thinking the email had originated from Microsoft. In actuality, the sender address included the domain name of a restaurant holding based in Russia.
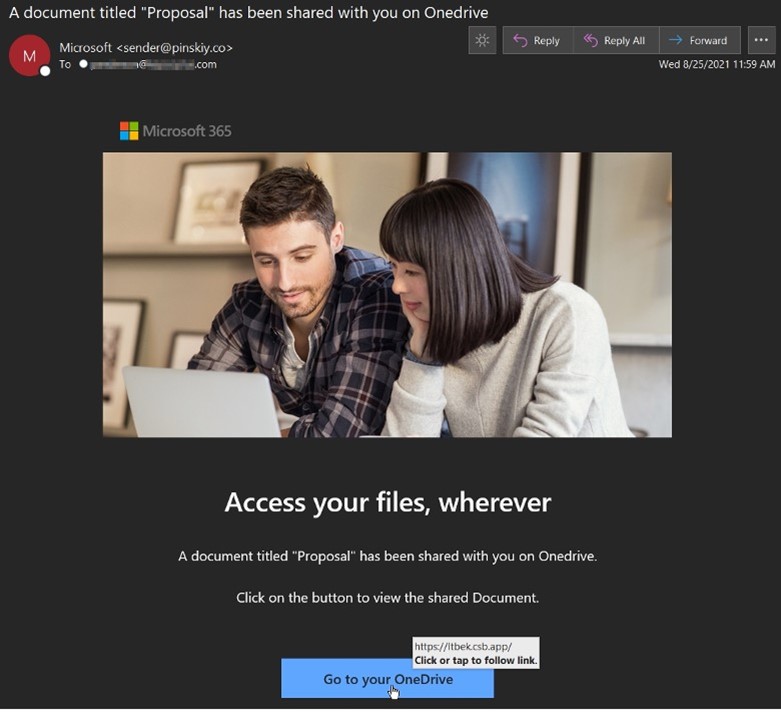
As shown above in the screenshot, the attack email informed the recipient that someone had shared a document entitled “Proposal” with them on “Onedrive.”
(That’s another red flag. Why would Microsoft misspell the name of its own file sharing service by not capitalizing the “d” in “Drive”?)
The attack email then prompted the recipient to download the document by clicking on a hyperlinked “Go to your OneDrive” button. (Ah, it’s spelled correctly there.)
Troy Gill, senior manager of threat intelligence at Zix | AppRiver, explained what happened when someone clicked on the embedded button.
“Once the recipient clicks the email link, they are directed to the phishing site on Code Sandbox below,” he explained. “It appears this attacker was using the free personal plan on Code Sandbox’s platform since the phishing page still contains the ‘Open Sandbox’ option on the bottom right. Paid plans offer the private sandboxes.”

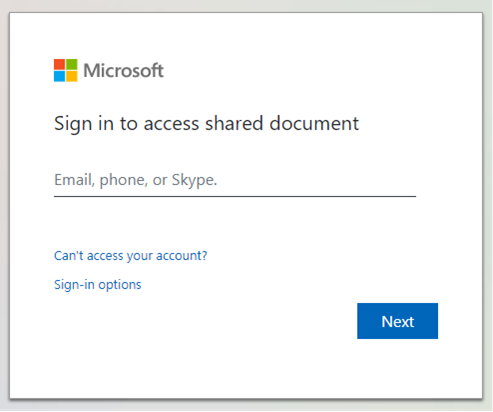
The phishing site then prompted the visitor to access the alleged “Proposal” by signing in with their Gmail, Outlook, AOL, or other email credentials.
Email Campaign #2: Abuse of Milanote
Around that same time, the Zix | AppRiver team detected an attack that had originated from the compromised email account of someone with the first name “Maxwell.”
The email used the subject line “Outstanding invoice” to trick the recipient into thinking that Maxwell had sent them an invoice using “Nimbusweb,” which is the misspelled name of a software company based in Cleveland, Ohio.
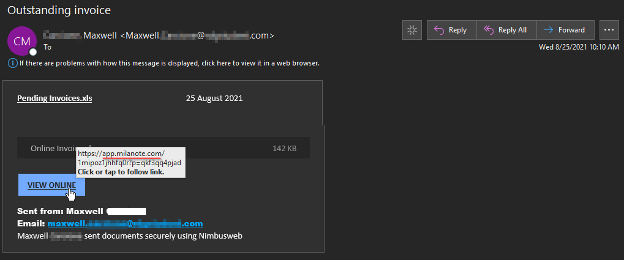
At that point, the attack email instructed the recipient to click an embedded “View Online” button. The button contained a link for Milanote, a tool which users can leverage to organize boards and projects into visual boards.
The Zix | AppRiver team examined the Milanote destination and found that it contained an image lure pointed to a link hosted on appdomain[.]cloud, an IBM Cloud service commonly abused by malicious actors.
In July 2020, for example, Bleeping Computer analyzed a phishing campaign that pretended to come from a help desk. The attack operation ultimately leveraged three cloud services including IBM Cloud in an attempt to steal a recipient’s credentials.
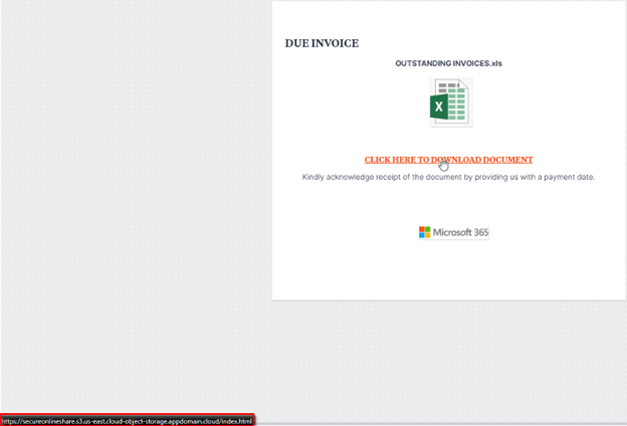
The lure prompted the user to download what appeared to be an Excel spreadsheet. When a visitor clicked the link, they found themselves redirected to the Microsoft-branded credential harvesting page shown below.
Defending Against Microsoft-Themed Email Attacks
Organizations can defend themselves against Microsoft-themed email attacks such as those discussed above by augmenting their email security posture. Towards that end, they can invest in an email security solution that’s capable of analyzing incoming email messages in real time for malware signatures, campaign patterns, IP addresses, and other threat behaviors—all while allowing legitimate correspondence to reach its intended destination.
Learn how Zix | AppRiver can help to defend against email attacks that spoof Microsoft.
