Blog
 Attackers Increasingly Using Customized Phishing Campaigns to Target Users
Attackers Increasingly Using Customized Phishing Campaigns to Target Users
Email attackers are increasingly using customized phishing campaigns to target users. Read more about these highly targeted attacks here.
Read more Double Encryption – A Pain in the Side of Your Ransomware Recovery Efforts
Double Encryption – A Pain in the Side of Your Ransomware Recovery Efforts
Ransomware actors use double encryption to complicate the recovery process for victims so they will be more inclined to pay. Read to learn more about it here.
Read more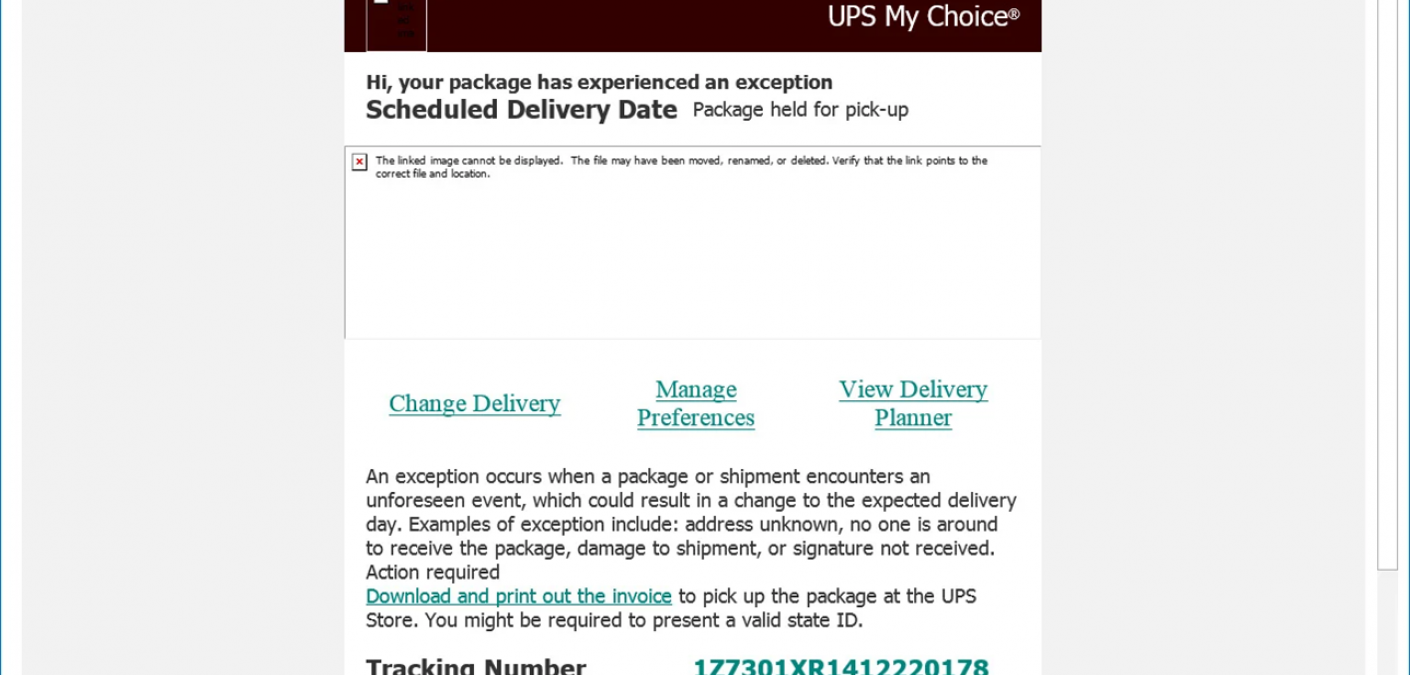 XSS Flaw in UPS Website Used by Phishers to Distribute Malware
XSS Flaw in UPS Website Used by Phishers to Distribute Malware
Phishers used a cross-site scripting (XSS) flaw in the UPS website to distribute malware using email subject line “UPS Delivery Exception: Action Required”.
Read more Defending Against Ransomware Means Preventing It
Defending Against Ransomware Means Preventing It
Organizations need to be prepared to defend against ransomware. But what does “ransomware defense” mean and how does it look in practice? One word: prevention.
Read more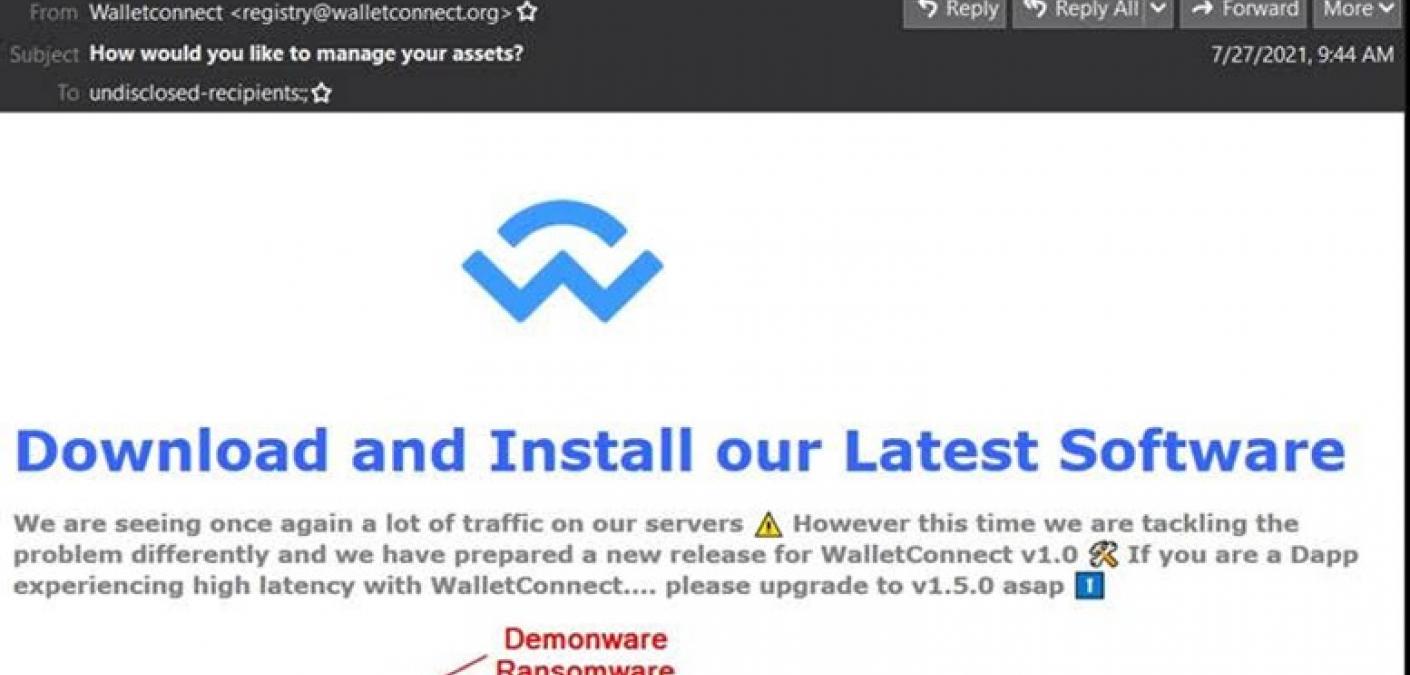 Demonware Ransomware Distributed Using .EXE Email Attachments
Demonware Ransomware Distributed Using .EXE Email Attachments
Malicious actors used emails carrying executable (.EXE) file attachments to target recipients with Demonware ransomware.
Read more What a Robust Data Backup Strategy Looks Like in Practice
What a Robust Data Backup Strategy Looks Like in Practice
Data backups are a top security measure used for ransomware attack recovery, but having a robust data backup strategy is just as important. Here are some tips.
Read more Oski Infostealer Delivered by Fake Payment Slip Emails
Oski Infostealer Delivered by Fake Payment Slip Emails
Phishers leveraged emails with the subject line “Payment Slip” to target unsuspecting users with samples of the Oski infostealer to steal bank data.
Read more Where does Ransomware come from? Here are 3 common attack origins.
Where does Ransomware come from? Here are 3 common attack origins.
Knowing the common origins of new ransomware strains can help organizations defend their networks. From state-sponsored to RaaS, three origins are worth noting.
Read more Phishing-Driven Data Breaches Cost $4.65M on Average, Finds IBM
Phishing-Driven Data Breaches Cost $4.65M on Average, Finds IBM
Data breaches that used email phishing as their initial attack vector cost organizations an average of $4.65 million, according to 2021 IBM report.
Read more Phishers Misuse Email Marketing Service to Compromise Outlook Accounts
Phishers Misuse Email Marketing Service to Compromise Outlook Accounts
Digital attackers are misusing an email marketing service to trick recipients into handing over their Outlook account credentials.
Read more Double Extortion Means You Need More than Backups
Double Extortion Means You Need More than Backups
Combined crypto-ransomware and double-extortion attacks empower greedy attackers to demand two ransoms: one for data decryption and one to delete stolen data.
Read more Making the Leap from Consultancy to MSP
Making the Leap from Consultancy to MSP
Many consultancies see the MSP model as a natural next step to grow into a mature company. Yes, the MSP model can be more profitable, but where do you start?
Read more



