Attackers Increasingly Using Customized Phishing Campaigns to Target Users

Email attackers are increasingly using customized phishing campaigns to target users.
Phishing Attack #1: Spoofed Microsoft 365 Messages
At the beginning of August, the Zix | AppRiver team flagged an email that spoofed a legitimate Microsoft 365 notification message.
The email informed the recipient that someone had added them to their employer’s group. To add a sense of legitimacy to this claim, the attackers crafted the fake message to include the specific details of the recipient’s employer within.
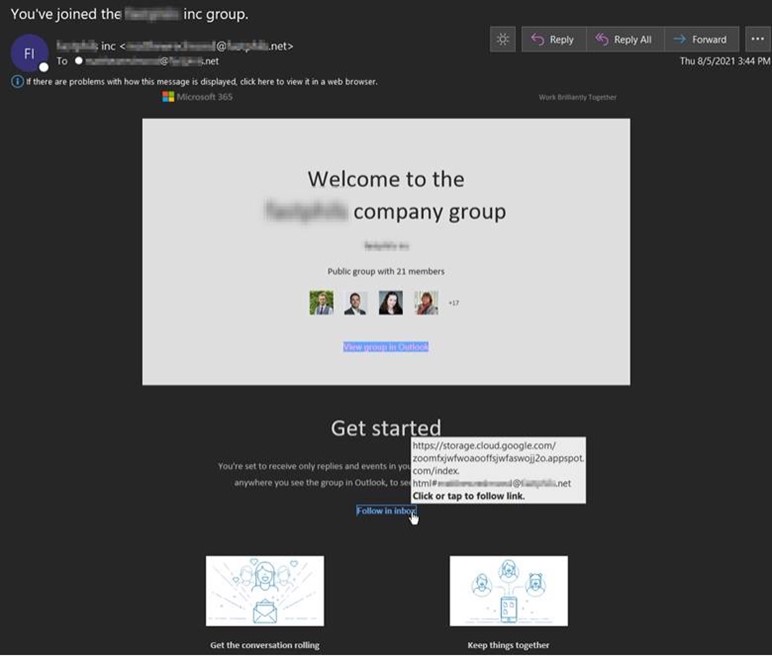
The purpose of the email was to trick the recipient into clicking hyperlinked text out of the assumption that they’d begin following the group’s activity in their inbox.
Once clicked, the campaign redirected the recipient to a web page designed to harvest their credentials for Appspot, a cloud computing platform for building and hosting web applications in data centers managed by Google.
Phishing Attack #2: Company Data Reflected on GoDaddy Sites
The Zix | AppRiver team detected another customized phishing campaign in mid-August.
It arrived as a message from a real estate specialist working at an insurance and real estate firm based in Watertown, Massachusetts. That individual’s name, email address, and contact information are removed in the screenshot below.
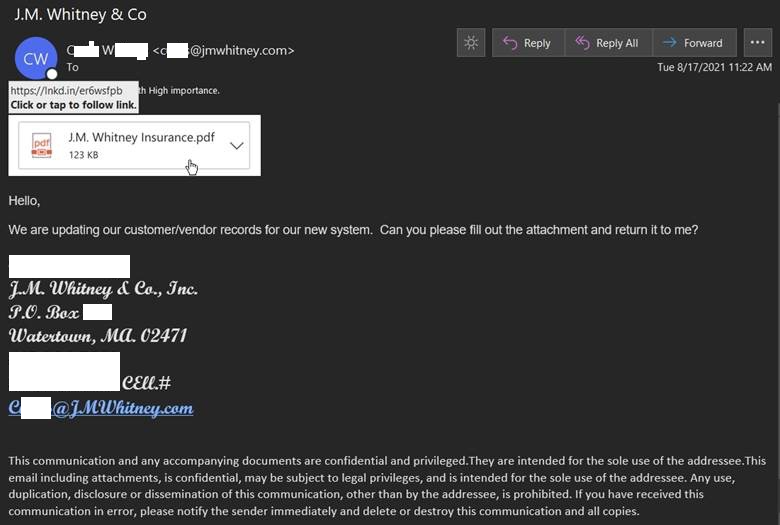
The message requested the recipient to download an attachment, fill out the document, and return it so that the spoofed company could update their records. But the attack email didn’t actually arrive with an attachment. Instead, the campaign came with a download image for a PDF document, Excel spreadsheet, or HTML file. It used this image to trick the recipient into clicking on an embedded Living Off the Land (LOtL) link designed for the operation.
The download image used a LinkedIn-shortened URL to mask the destination of the campaign and to provide click analytics to the group. (It’s important to note that phishing groups commonly rotate URL shortener services and/or use multiple tools for the same campaign.)
Troy Gill, senior manager of threat intelligence at Zix | AppRiver, explained what happened when someone clicked the download image.
“If the recipient clicks the shortener, are redirected to a site to the one pictured below,” he explained. “This group has recently increased the customization and realism to these credential harvesting portal jump sites. This is done with the compromised users company info reflected on GoDaddy sites page and a corresponding subdomain.”
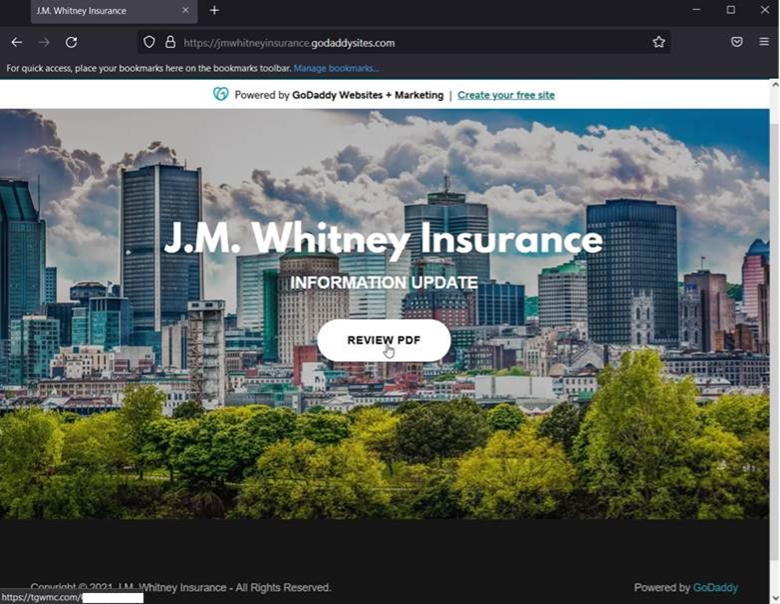
Visitors who clicked on the “Review PDF” button in the credential harvesting portal jump site found themselves redirected to a web page designed to harvest their Office 365 credentials.
That site included the compromised sender’s info in the URL to add another layer of personalization for the sake of tricking the recipient into believing it was legitimate. That data is removed in the screenshot above.
Defending Against Customized Phishing Campaigns
Phishing groups aren’t just spoofing Microsoft notification messages and reflecting company information on GoDaddy sites to customize their phishing campaigns. They’re also abusing website building services to create pages as payloads in their LOtL phishing efforts.
Acknowledging the variety of techniques at play, organizations need to defend themselves against phishing attacks using customization techniques. They can do this by investing in a tool that’s capable of scanning their incoming messages for malware signatures, campaign patterns, IP addresses, and other threat indicators. If conducted in real time, such analysis can allow legitimate correspondence to reach their intended destination.
Defend against sophisticated phishing attacks using Zix | AppRiver today.
