Phishers Misuse Email Marketing Service to Compromise Outlook Accounts

Digital attackers are misusing an email marketing service to trick recipients into handing over their Outlook account credentials.
There Once Was an Outlook Syncing Error…
In mid-July, researchers at Zix | AppRiver flagged an attack email that warned the recipient of an “Outlook Sync Error.”
Those who behind the campaign listed “IT-Sys Support” as the email’s sender to reassure the recipient that the message was a legitimate warning from their organization’s IT department.
But a closer look revealed that the sender address did not belong to any IT department. That’s because it used a Philadelphia-based creator of beer, spirits, and wine-based libations as its domain name.
It’s unclear from the attack email whether someone compromised the email account of an employee at that company and used it to send out malicious emails or whether they simply used spoofing techniques as part of their campaign.
The body of the email informed the recipient that there was an error syncing their mailbox with their employer’s Microsoft Exchange Server. It went on to tell the recipient that they would experience some trouble receiving new emails unless they agreed to click on the “Fix Error” button embedded in the email.
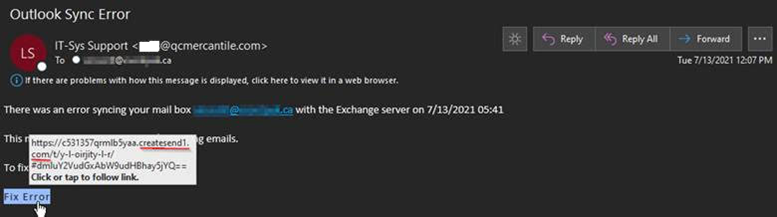
As shown in the screenshot above, the “Fix Error’ button did not redirect the recipient to a legitimate page where they could sync their Outlook account. It instead used a link for createsend1.com, a service owned by email marketing and automation company Campaign Monitor, to shield the campaign’s destination from traditional email security solutions.
By use of this evasion-based tactic, the phishing operation ultimately directed the recipient to a landing page designed to steal their Outlook account credentials.
Not the First Phish to Leverage an Email Marketing Service
The operation described above wasn’t the first time that malicious actors used an email marketing service as part of their attack chain
Back in October 2020, for instance, Zix | AppRiver spotted a phishing campaign that notified victims of a new login location associated with their Amazon account. It then instructed them that they could review their account activity and cancel any unauthorized purchases made on their account by clicking on an embedded “Update Now” button. Hovering over the asset revealed a URL consisting of a SendGrid domain and unique subdomain that delivered the recipient to a phishing landing page designed to steal their Amazon account details.
It was a similar story in June 2021 when Zix | AppRiver came across some attack emails disguised as official correspondence from the U.S. Agency for International Development (USAID). The email instructed the recipient to click on a button for the purpose of viewing documents allegedly published by President Donald Trump. The campaign then redirected the recipient to a legitimate Constant Contact service before infecting them with a malicious .ISO file distributed by the infrastructure of NOBELIUM, the threat actor behind the SolarWinds supply chain attack. It was later determined that NOBELIUM had compromised a Constant Contact account used by USAID.
How to Defend Against Evasive Phishing Attacks
The attacks discussed above underscore how phishers continue to misuse legitimate services such as email marketing platforms to help their campaigns evade detection. Traditional email security solutions will not protect them against these sophisticated attacks. In response, organizations need to upgrade their email security posture with a solution that’s capable of scanning incoming correspondence for campaign patterns, malware signatures, IP addresses, and other threat behaviors. This analysis should occur in real time so that legitimate correspondence can reach its intended destination without delay.
Harden your security posture against evasive email attacks with Zix | AppRiver.
