Demonware Ransomware Distributed Using .EXE Email Attachments
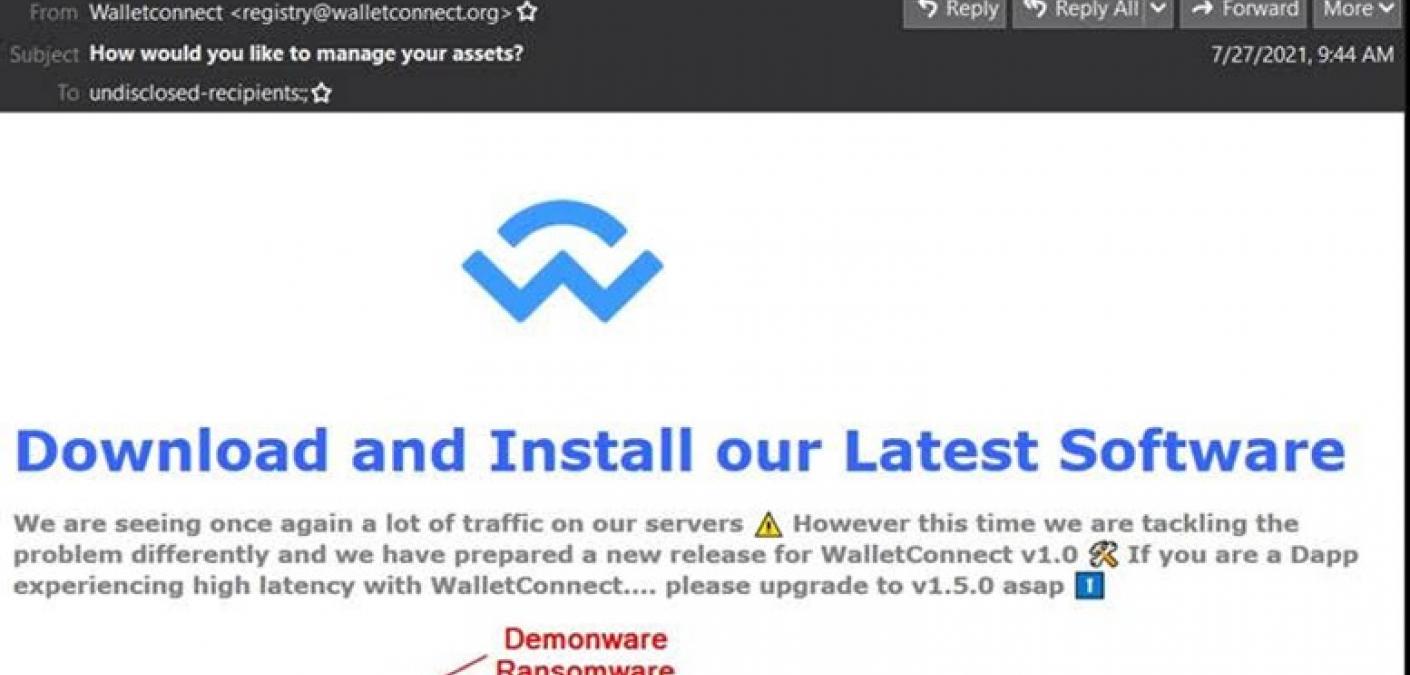
Malicious actors used emails carrying executable (.EXE) file attachments to target recipients with Demonware ransomware.
“How Would You Like to Suffer a Ransomware Infection?”
In mid-July, the Zix | AppRiver team detected an attack email that arrived with the subject line “How would you like to manage your assets?”
Those responsible for the campaign used spoofing techniques to disguise their attack email as a message from Wallet Connect, an open-source protocol for using QR codes or deep linking to connect decentralized apps with mobile wallets.
The sender email address appeared as “registry@walletconnect.org.” However, a Google search revealed no matches for that sender.
The message informed the recipient that Wallet Connect was “seeing once again a lot of traffic on our servers.” It went on to instruct the recipient to upgrade to v1.5.0 of the software.

As seen in the screenshot shared above, the email arrived with an executable file called “Walletconnect.exe.” Running that file eventually caused the campaign to load Demonware.
“It’s a rookie move for email attackers to distribute their malware payloads using .EXE files,” noted Troy Gill, manager of security research and senior security analyst at Zix | AppRiver. “Most email clients will block those files by default, Outlook being one of them. This attack is therefore likely the work of a smaller or amateur attack group that doesn’t know any better.”
This routine behavior among security products explains why so many email attackers now pack their executable files with miscellaneous content.
In one campaign detected by Zix | AppRiver in April 2021, malicious actors packed their executable file with a Dinosaur game in an effort to distribute the Snake keylogger.
It was several months later when the security firm spotted an operation that packed its executable file with a bingo game to distribute the AgentTesla infostealer.
A Look at the Demonware Payload
News of Demonware first emerged in February 2020, as reported by Bleeping Computer. It’s at that time when a security researcher first spotted Demonware, also known as “Black Kingdom” ransomware, encrypting users’ files and appending .DEMON to their affected files.
A few months after that, Heimdal Security wrote that the Black Kingdom ransomware gang had become the latest threat actors to join in on exploiting ProxyLogon, the set of four Microsoft Exchange Server vulnerabilities that the HAFNIUM threat actor first used to compromise 30,000 organizations in the United States.
Which brings us to the details of this attack campaign.
“Upon running the attached executable, the recipients’ files are locked with Demonware Ransomware, a 10-hour countdown timer begins, and the victims is urged to contact the ransomware actor via email with bitcoin ready for negotiations,” Gill noted.
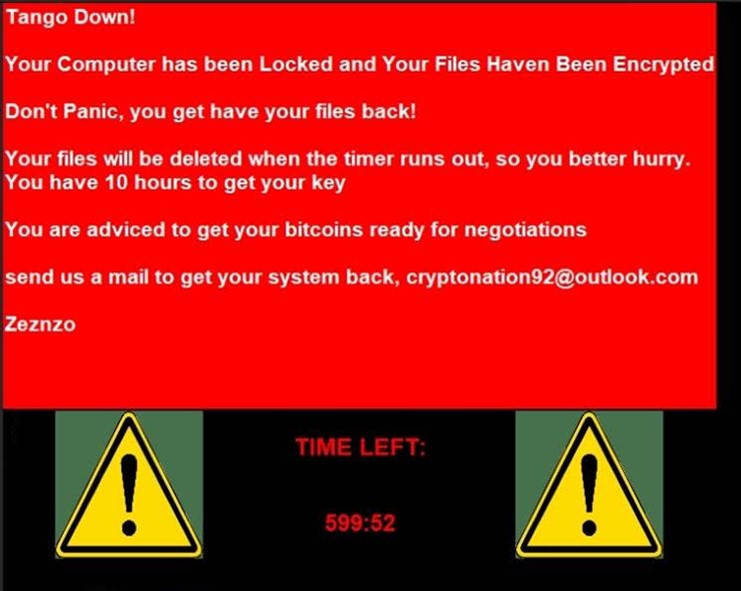
“Unfortunately, virtually anyone could conduct this attack as the PoC code is located on GitHub and would be easy to modify for a custom message and file extensions targeted by the software,” he went on to point out.
How to Defend Against Email-Borne Ransomware
The attack campaign discussed above highlights the need for organizations to defend themselves against email campaigns delivering Demonware and other ransomware. One of the ways they can do that is by investing in a security solution that can scan their incoming email messages for malware signatures, campaign patterns, and other threat indicators. This tool should conduct its analysis in real time, all while allowing legitimate correspondence to reach its intended destination.
