XSS Flaw in UPS Website Used by Phishers to Distribute Malware
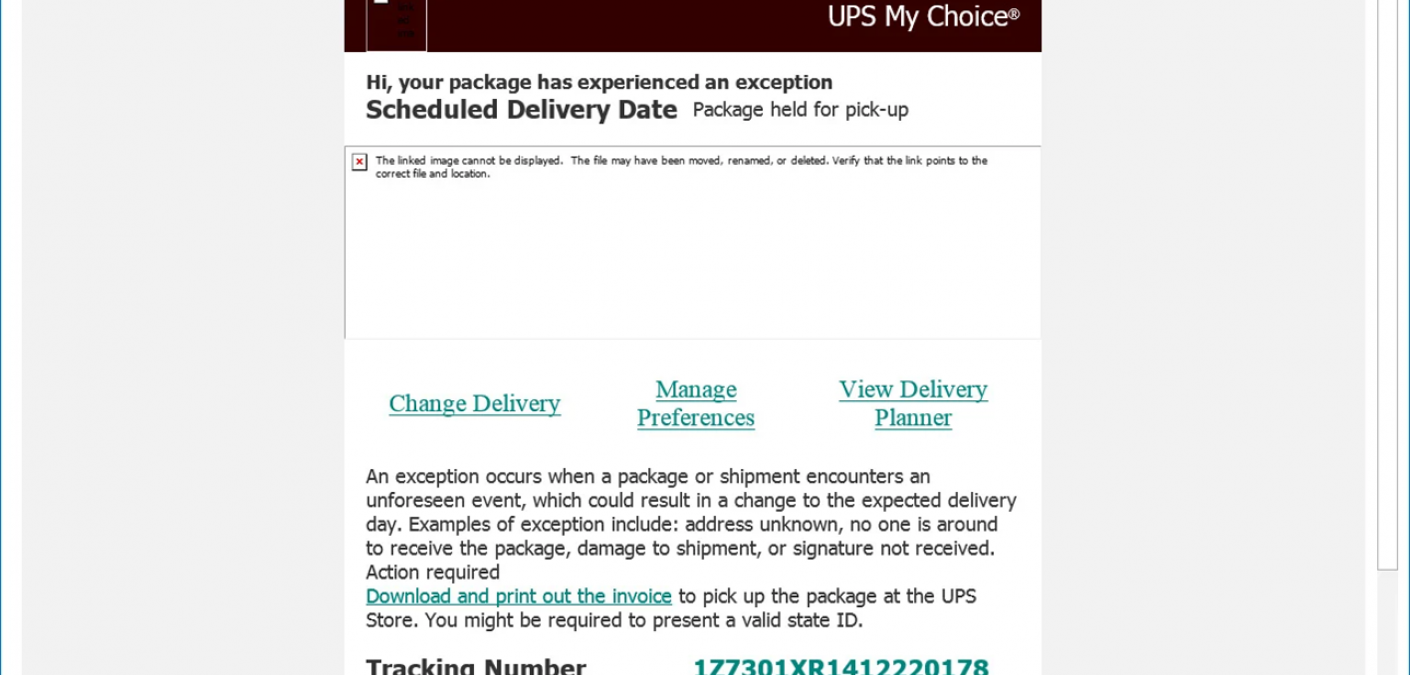
Phishers used a cross-site scripting (XSS) flaw in the UPS website to distribute malware.
Concealing an XSS Exploit Query Parameter in an Embedded URL
Near the end of August, Bleeping Computer revealed that a security researcher had discovered an email pretending to be from UPS.
The email arrived with the subject line “UPS Delivery Exception: Action Required,” and it claimed to have originated from “UPS My Choice.”
A closer look revealed that the email didn’t come from a UPS email address. Indeed, the domain of the sender email address pointed to resource for booking vacation experiences in Spain.
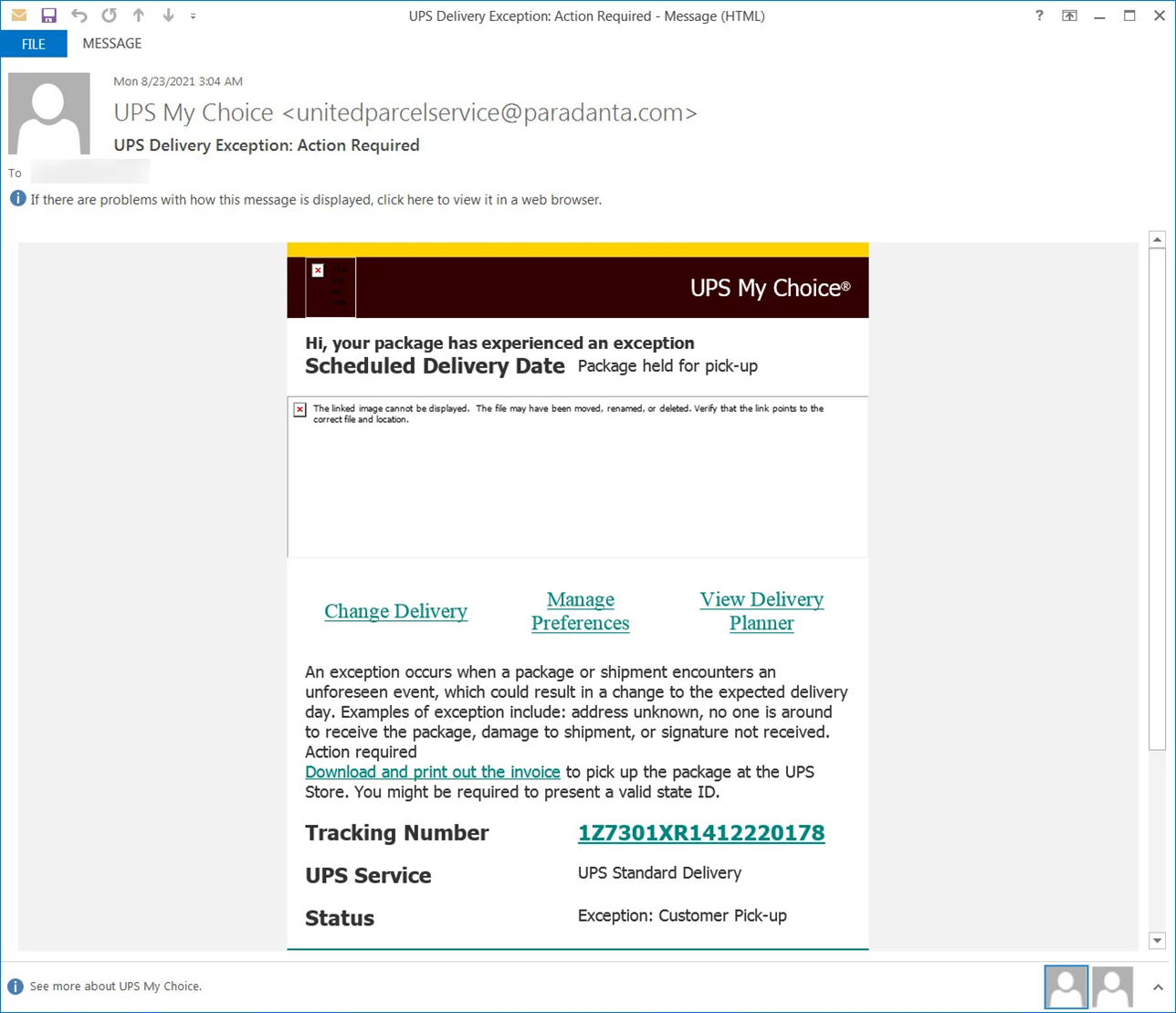
The body of the attack email informed the recipient that there was “an exception” with a package being held by UPS for pickup.
It included links through which the recipient could supposedly change the delivery date for the package, manage their preferences, view a delivery planner, and/or print out an invoice. None of those links arrived with malicious functionality.
The same can’t be said about the hyperlinked tracking number, however.
After cleaning up the link, the security researcher found two interesting components. The first was a base64 encoded string with a comment explaining that the phisher had made the link longer to conceal an XSS exploit query parameter. The second was a JavaScript XSS exploit injected into UPS.com.
The attack used a Cloudflare worker script to display a message indicating that the website was downloading a file. The message also came with a link that visitors could click on if the download didn’t complete on its own.
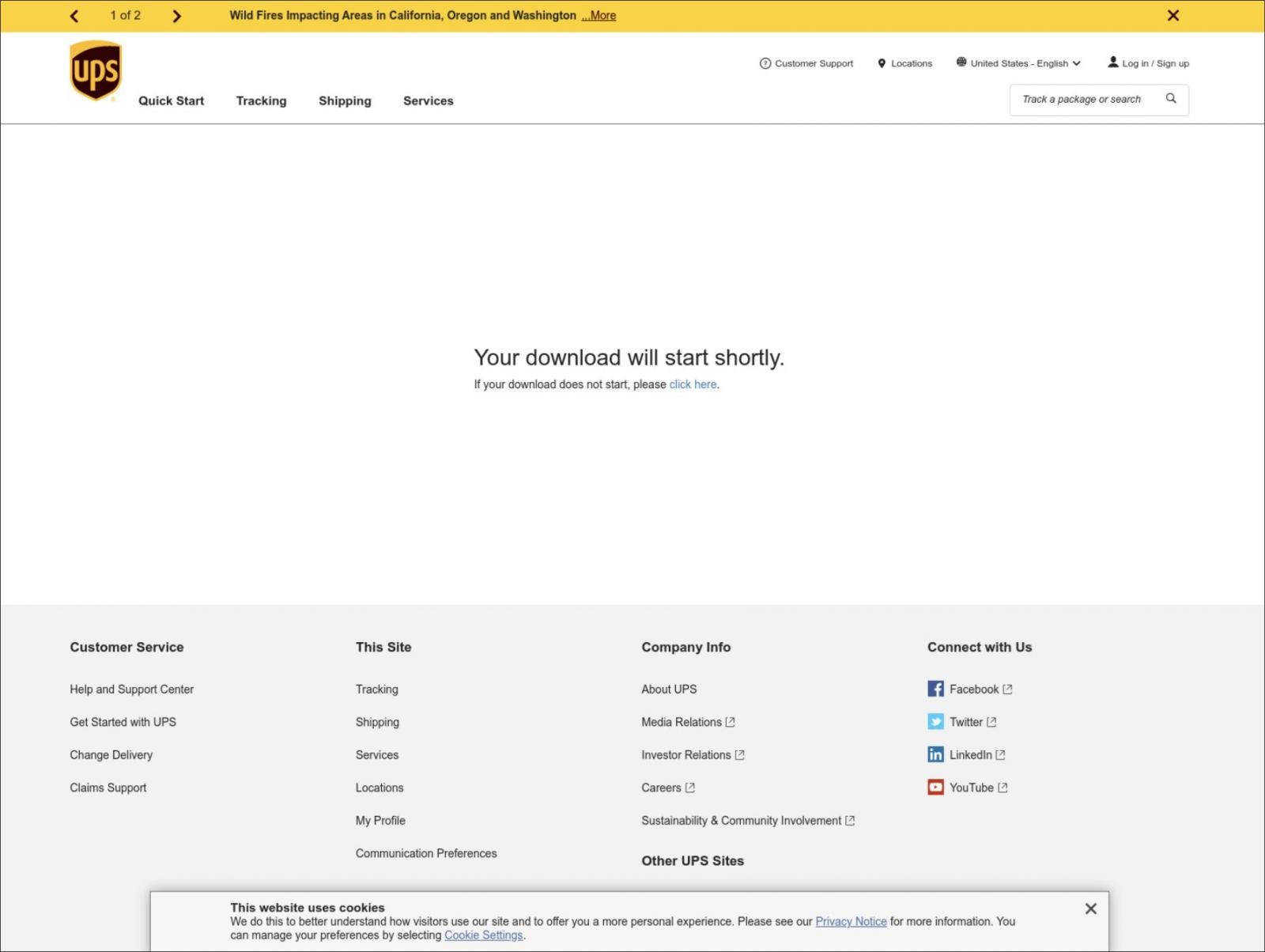
Clicking on a link caused campaign to download a malicious Microsoft Word document from the attacker’s Cloudflare project—all while users saw a legitimate UPS page in their address bar.
Bleeping Computer confirmed that UPS has since fixed the vulnerability.
Inside the Malicious Word Document
The malicious Microsoft Word document pretended to be a shipping invoice from UPS, and it arrived with the name “invoice_1Z7301XR1412220178.”
All the text in the shipping invoice appeared unreadable to trick recipients into clicking the “Enable Content” button.
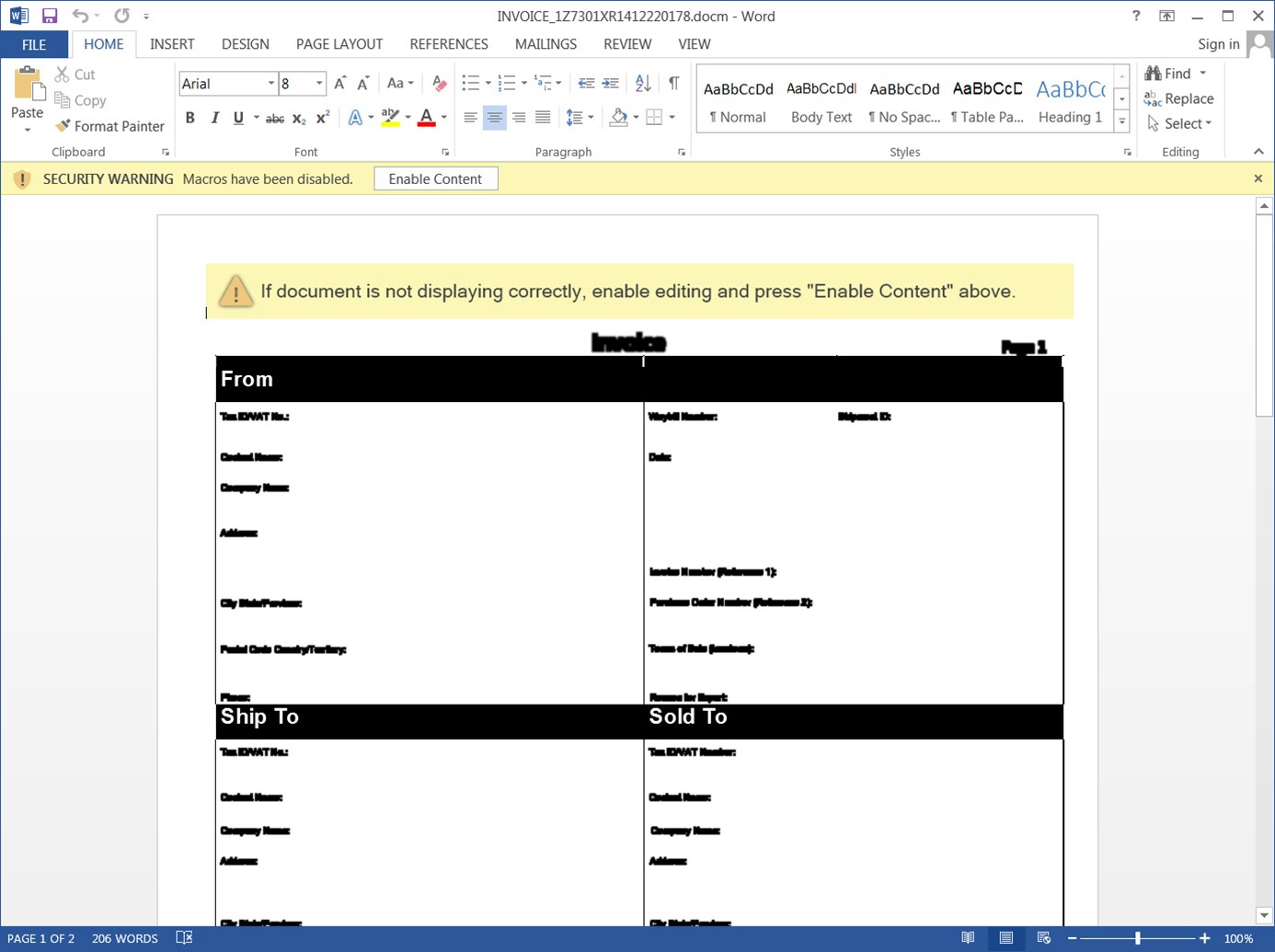
Once approved, the document used malicious macros to try to download an additional file from a web location. That URL wasn’t working at the time of Bleeping Computer’s reporting, however, thus preventing security researchers from viewing the payload.
Troy Gill, manager of security researcher at Zix | AppRiver, said that this isn’t the first time he’s seen a campaign like this.
“The type of phishing attack that targeted UPS customers is one we refer to as Living off the Land (LotL) phishing, which occurs when cybercriminals abuse otherwise legitimate services to ‘blend in with the crowd’ and mask the true nature of their message,” he explained.
“The attacks vary greatly in theme and brand being impersonated. However, more attackers have begun posing as a shipping service since the pandemic began, given that consumers are spending less time in stores and shopping more online.”
Defending Against Similarly Sophisticated Phishing Campaigns
This campaign highlights the need for organizations to defend themselves against sophisticated phishing attacks. One of the ways they can do that is by investing in an email security solution that’s capable of scanning incoming messages for campaign patterns, malware signatures, IP addresses, and other threat indicators. This analysis should occur in real time so that legitimate business correspondence can reach its intended destination.
Learn how Zix | AppRiver can help your organization defend against email-based attacks.
