Microsoft Password Expiration Scam Uses Customized Image to Steal Victims’ Account Details
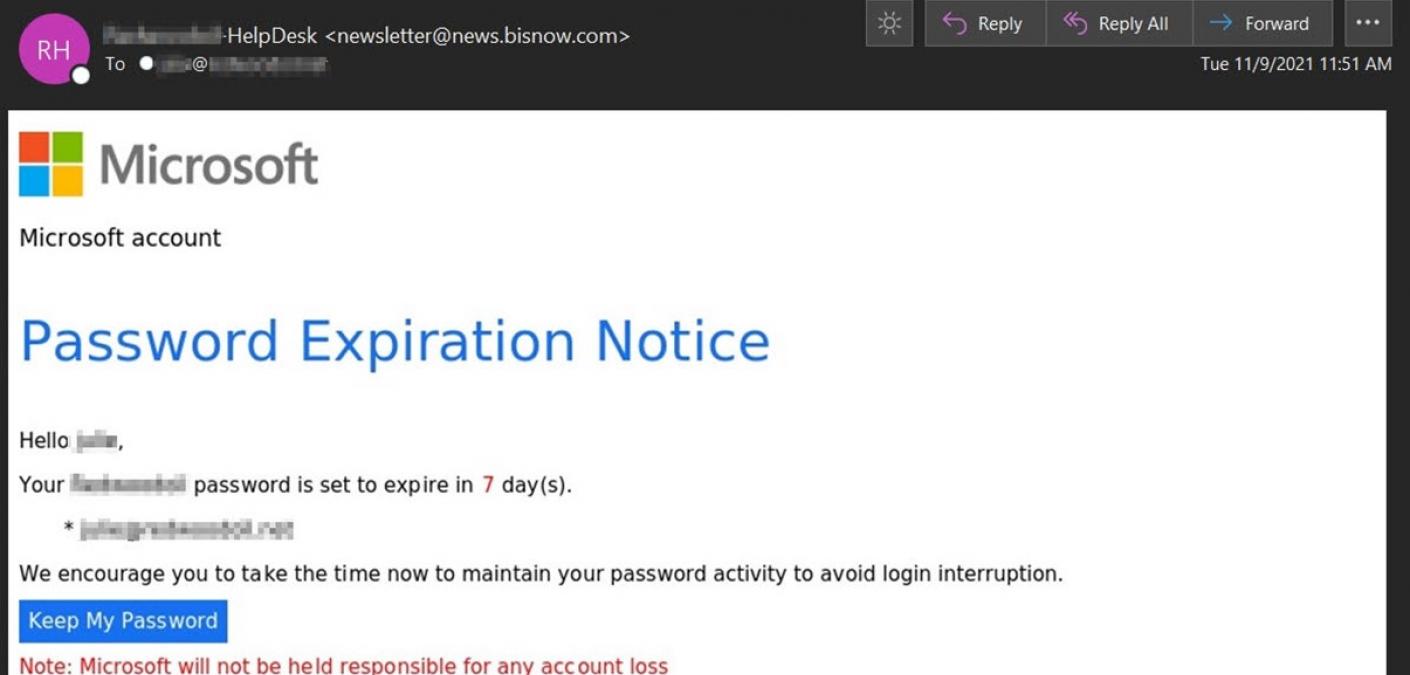
A Microsoft password expiration scam used an image customized with a recipient’s email address and domain to steal their account credentials.
“Request (for Data Theft) Received”
In early November, Zix | AppRiver flagged an email that appeared to originate from the helpdesk at a recipient’s company. (The attackers included “HelpDesk” in their email’s subject line to support this ruse.)
But the email didn’t originate from a helpdesk team. Its sender line indicated that it came from a B2B platform serving the commercial real estate industry.
Using branding stolen from Microsoft, the attack email impersonated a password expiration notice and informed the recipient that their password was set to expire in seven days. It included the recipient’s name, domain, and email address to add a sense of legitimacy.
From there, the attack email instructed the recipient to “take the time now to maintain your password activity to avoid login interruption” by clicking on a “Keep My Password” button.
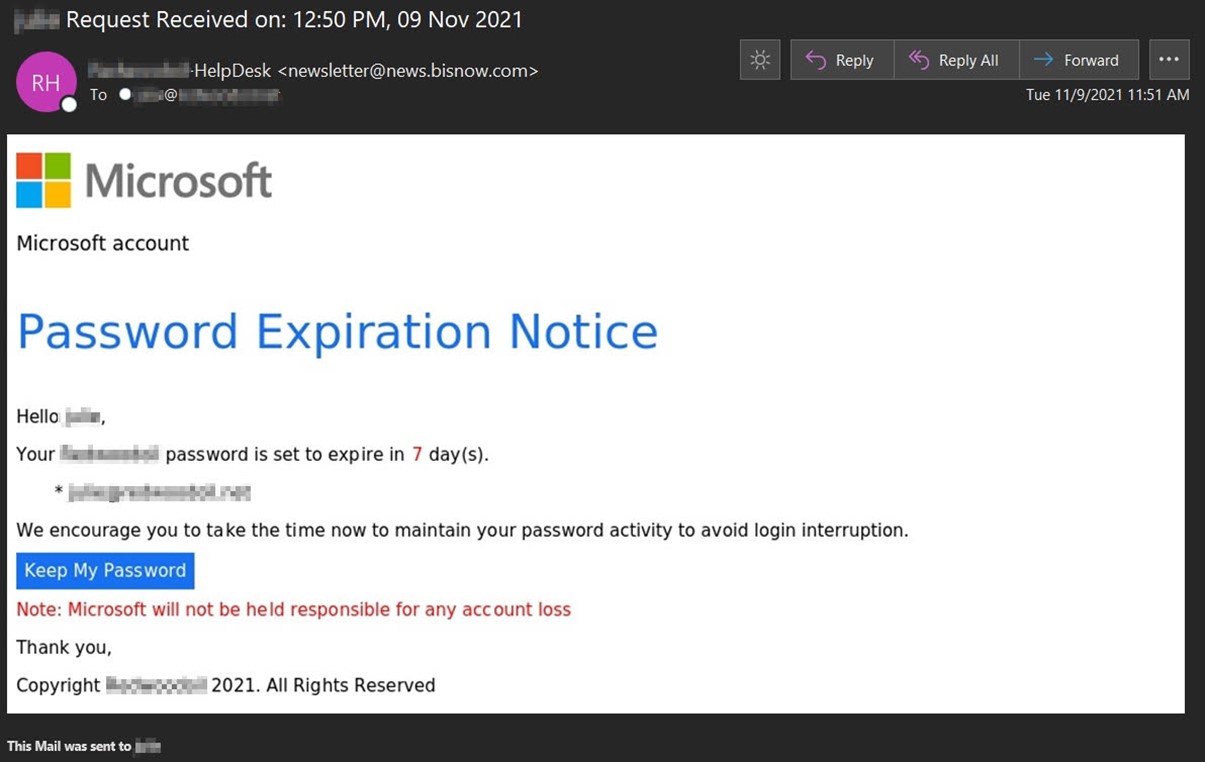
As you can see from the screenshot above, the email included the warning that “Microsoft will not be held responsible for any account loss.”
That’s an imperfect replication of Microsoft’s terms of service. These read as follows: “Microsoft will not be liable for any loss that you may incur as a result of someone else using your password or account, either with or without your knowledge. However, you could be held liable for losses incurred by Microsoft or another party due to someone else using your account or password.”
Now, this isn’t the first time Zix | AppRiver came across a Microsoft-themed password expiration scam. Not by a long shot. But it is the first instance where the security firm observed a specific tactic in play.
Here’s Troy Gill, manager of threat intelligence at Zix | AppRiver, with more.
“Instead of the normal text, it utilized an image link for the lure but the image itself was customized to contain the recipients email address and domain,” he explained. “It was also an automated attack being sent in large volumes indicating the attacker had an automated setup for these and not manually changing each image for the recipients.”
“Keep My Password”…Literally, You Can Take It
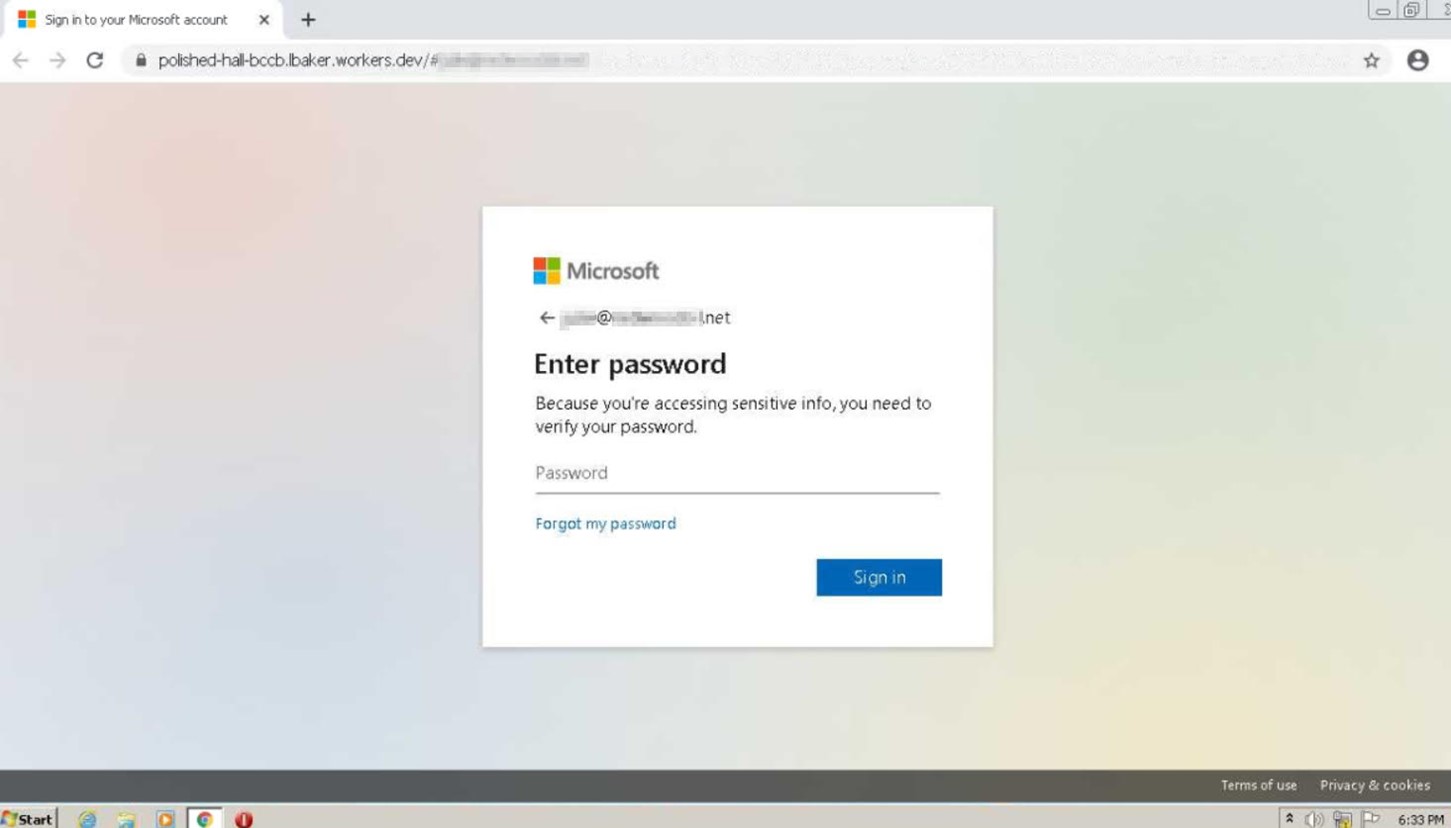
If a user complied with the attackers’ instructions and clicked on a customized image, the campaign redirected them to a phishing page that abused workers.dev as a means of living off the land (LotL) of Cloudflare’s reputation.
Malicious actors continue to resort to LotL techniques as a way of evading detection. Back in September 2021, for instance, Zix | AppRiver came across an operation that abused DocuSign to trick victims into handing over their credentials for Outlook, Office365, or another email client.
This campaign doesn’t even include all the times where email attackers abused Azure, Sway, and other legitimate Microsoft services to phish victims’ details in recent years.
For this attack attempt, the phishing site impersonated a Microsoft login page that also included the victim’s domain and email address. The purpose of this personalization was to convince the victim that nothing was wrong.
Defending against a Fake Microsoft Password Expiration Email
The attack campaign described above highlights the need for organizations to defend themselves against Microsoft-themed email attacks. One of the ways they can do that is by familiarizing their employees with what an email from their helpdesk will actually look like. They can complement that security awareness with a multi-layered email security platform.
