Microsoft Exchange Servers Hacked to Distribute SquirrelWaffle

Digital attackers hacked organizations’ vulnerable Microsoft Exchange Servers to distribute SquirrelWaffle malware.
Details of the Attack Campaign
In mid-November 2021, Trend Micro examined the initial access vector for several digital intrusions that occurred in the Middle East.
The security firm’s incident response team determined that all the attacks originated from on-premises Microsoft Exchange Servers. A closer look uncovered evidence of malicious actors having exploited ProxyLogon and ProxyShell on those resources.
One of those campaigns leveraged conversation hijacking, a tactic executed by the Emotet gang more than once, to inject themselves into existing email threats. Those responsible for the attack also used true account names from the victim’s domain for the sender and the recipient. In doing so, they increased the chances that someone would follow the email’s instructions.
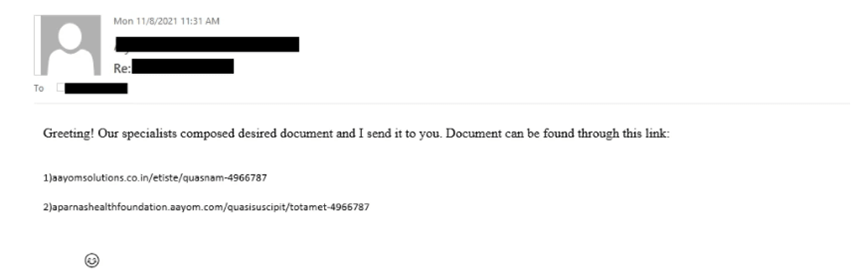
As is evident in the above screenshot, the email didn’t exactly relay its instructions eloquently.
“Our specialists composed desired document and I send it to you,” it informed the recipient. “Document can be found through this link.”
Trend Micro went on to inspect the headers for the attack emails. They discovered that the mail path was internal between three Exchange Servers’ mailboxes. The threat actor didn’t drop any tools for moving laterally. They also didn’t execute malware on the Exchange servers that would have triggered alerts before the emails spread across the environment.
“The attacker exploited the Exchange servers to deliver internal mails,” Trend Micro explained. “This was all done to catch users off-guard, making them more likely to click the link and open the dropped Microsoft Excel or Word file.”
Both links embedded in the malicious emails dropped a .ZIP file containing a Microsoft Excel sheet or Word document. Once downloaded, the documents used malicious Excel 4.0 macros to download and execute a malicious DLL related to Qbot (otherwise known as “QakBot”). This infection ultimately led the campaign to infect the machine with “SquirrelWaffle.”
Squirrel-What?
SquirrelWaffle first made news in late October when Cisco Talos spotted some spam campaigns infecting systems with the new malware loader. Upon successful infection, SquirrelWaffle granted threat actors the foothold they needed to infiltrate organizations’ systems and network environments as well as to conduct additional compromise attempts and malware infections.
The Zix | AppRiver team observed this exact behavior in a SquirrelWaffle campaign that took place in mid-November.
Like the operation detected by Trend Micro, the malicious actors behind this attack attempt used conversating hijacking techniques to inject themselves into an existing email thread with the subject line “Re: S.A.M. Newark Lay out.”
The attackers said that they had “uploaded some additional info regarding the recent contract and payslip.” They went on to instruct the recipient that they could resolve a previously mentioned problem if they chose to “follow steps via the link lower.”
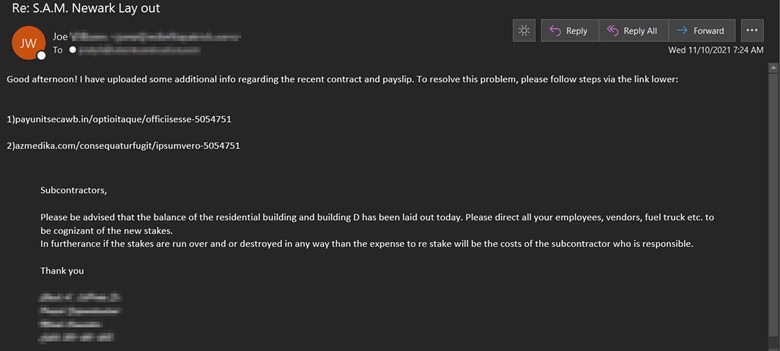
Clicking on either of the links led victims to a SquirrelWaffle payload. At that point, the malware followed up by dropping either QakBot or Cobalt Strike onto the infected machine.
Defending Against Email-Borne SquirrelWaffle Attacks
The attack instances discussed above highlight the need for organizations to defend themselves against SquirreWaffle. One of the ways they can do that is by reviewing their vulnerability management programs to make sure they’re prioritizing and implementing software patches on a timely basis. Regarding the campaign detected by Trend Micro, for example, Microsoft released a patch for ProxyLogon in March and similar fixes for ProxyShell a few months later. Organizations can then go on to pair their vulnerability management efforts with a multi-layered email security solution that scans incoming messages for potential threats.
