Attackers Targeting Mortgage Servicers to Steal Email Accounts Credentials
Digital attackers are targeting mortgage servicers and their clients to try to steal victims’ email account credentials.
Data Theft as a Final Payoff=
At the end of January, the Zix | AppRiver team flagged an email informing the recipient that they needed to submit a mortgage payment prior to the date contained in an attached payoff statement.
“Attached” is an odd choice of words here considering that the email didn’t arrive with an attached file. Instead, it arrived with an embedded hyperlinked button named, “Access Payoff Statement File Here.”
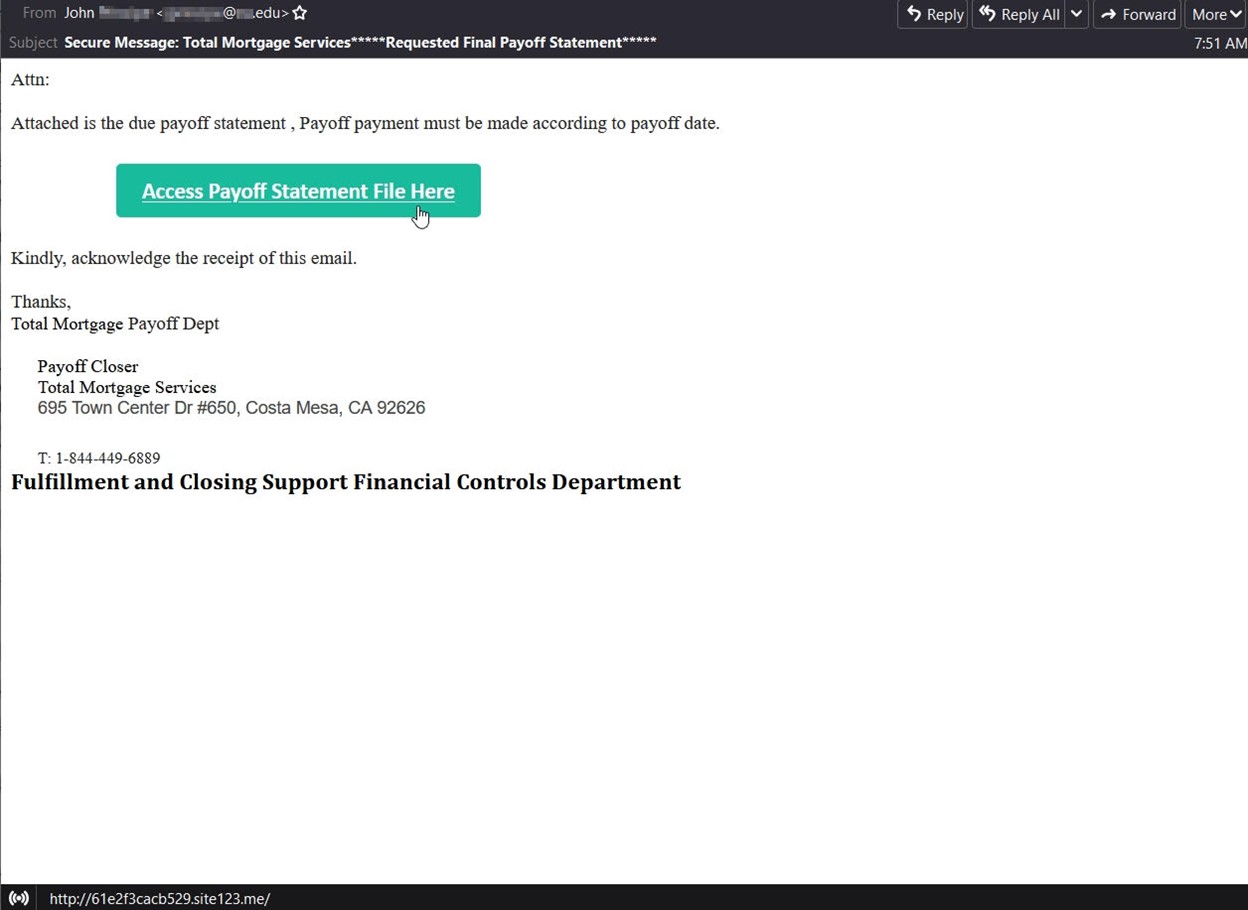
Misleading wording wasn’t the only element that gave the attack email away as a fake. As seen in the screenshot included above, the message came with a signature block indicating that it had originated from a nationwide mortgage lender service…with the exception of the physical address. That location pointed to another mortgage service entirely.
Other signs gave away this discrepancy. For instance, the sender email address ended with .EDU—an unusual domain for an established mortgage service company. Zix | AppRiver reasoned that those responsible for this attack likely compromised the account of someone working at an educational institution to conduct their campaign.
Not only that, but the phone number included in the signature block didn’t belong to the mortgage lender specifically mentioned in the message or the other company whose address appeared in the email. A Google search of the number didn’t yield any meaningful results.
Following the Button
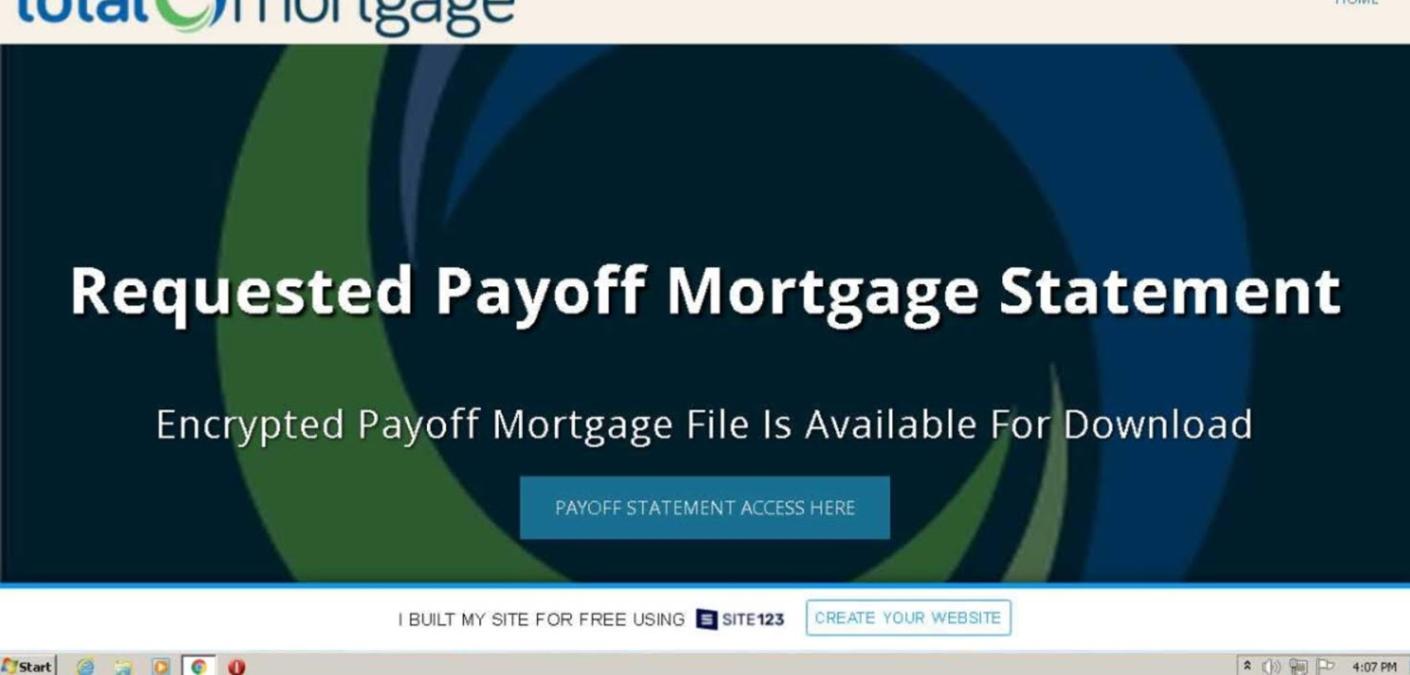
Clicking on the embedded button redirected the recipient to a website that appeared to be a page operated by the named mortgage lender service. The page used stolen branding to convince the recipient to click on an “Payoff Statement Access Here” button so that they could view an “encrypted payoff mortgage file.”
Once again, however, the jump page gave itself away as a fake. How? By the inclusion of a statement indicating that whoever built the website did so using site123[.]me, a service for building free websites.
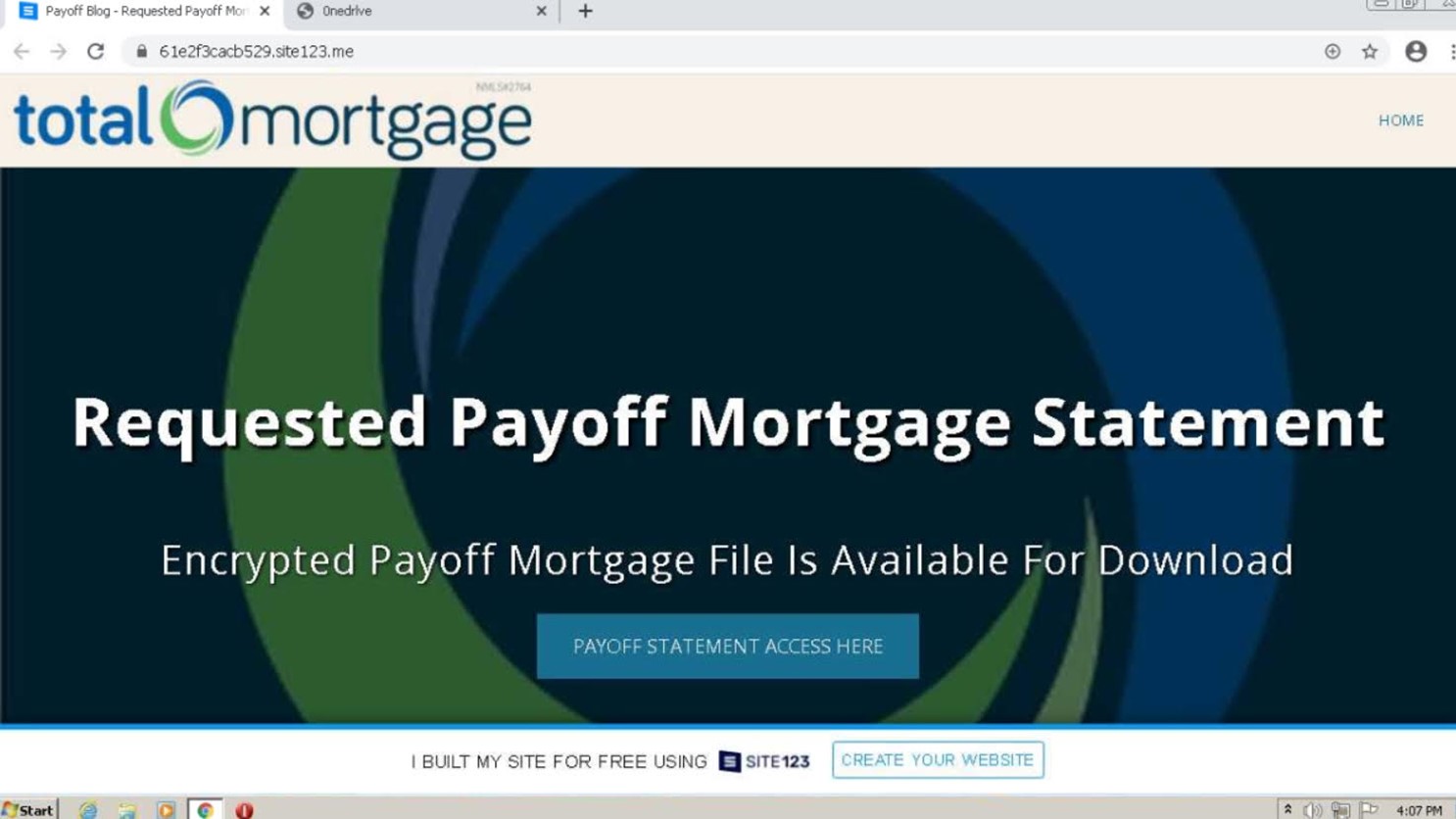
Given its profile in the mortgage lending field, the targeted service likely relies on its own web team—not a free website builder—to maintain its digital presence.
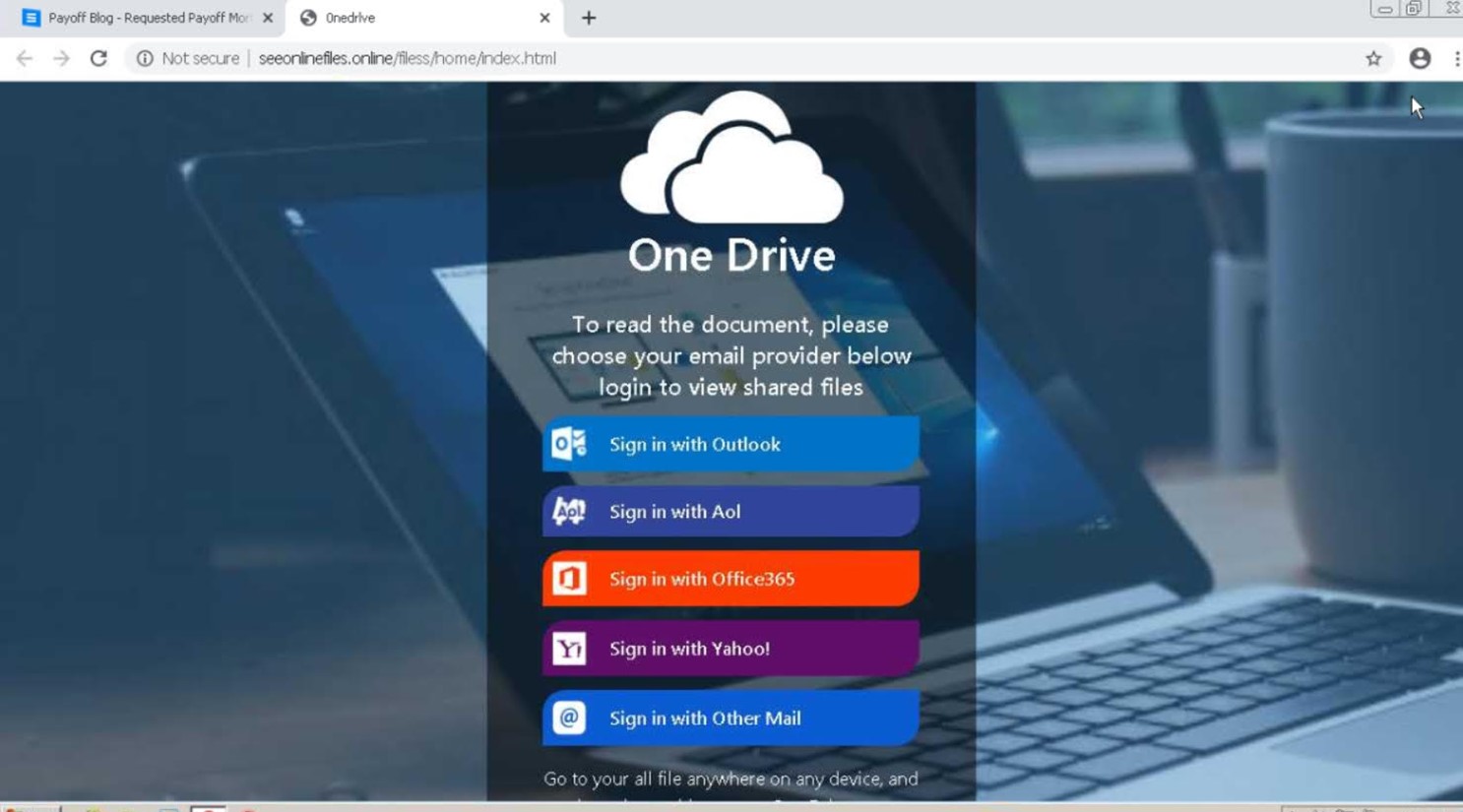
It’s therefore not surprising that the jump page didn’t present a mortgage payoff statement to the user. Instead, it redirected them to a phishing landing page with an even more suspicious domain name to try to steal their email account credentials.
Keeping a Fixed Email Security Focus for the Long Term
Troy Gill, manager of security research at Zix | AppRiver, doesn’t think that email attackers will refrain from using mortgages as a lure anytime soon.
“Business email compromise attacks targeting mortgage servicers and their clients continue to be an ongoing threat to customers,” he said. “The simplicity of the attack along with the low barrier to entry with a quick payoff keeps it an enticing vector for attackers.”
That’s especially not the case with mortgages haven’t just leapt up to nearly 4% in recent weeks—the highest they’ve been since October 2019, reported Mortgage News Daily.
Acknowledging that reality, organizations need to take action to defend themselves against mortgage-themed campaigns. They can do so by using security awareness training to educate their employees about common tactics and slip-ups committed by email attackers. They can then complement those measures with an email security solution that can scan incoming messages for malware signatures and other threat indicators, blocking suspicious messages before they reach an employee’s inbox while allowing legitimate messages to reach their intended destination.
