Digital Attackers Abusing SendGrid to Steal Account Credentials

Malicious actors are launching digital attack campaigns that abuse SendGrid in an effort to steal victims’ account credentials.
A Look Inside Three Attack Attempts
Zix | AppRiver spotted three attack attempts abusing SendGrid that arrived between the end of August and the end of September 2020.
Amazon
The first attack email arrived on August 25 with the subject line “New login location detected,” and it stole branding from Amazon.com to trick the recipient into thinking they were receiving a message from the e-commerce platform about a new login attempt on their account.
To support this ruse, the malicious actors behind this campaign used spoofing techniques to make their attack email appear as though it were coming from AMZ.SUPPORT@amazon.com—a fake support email which convincingly referenced Amazon’s official domain.
In reality, the email originated from an email account associated with parentcircle.in, an online community for individuals living in India to find and share parenting tips.
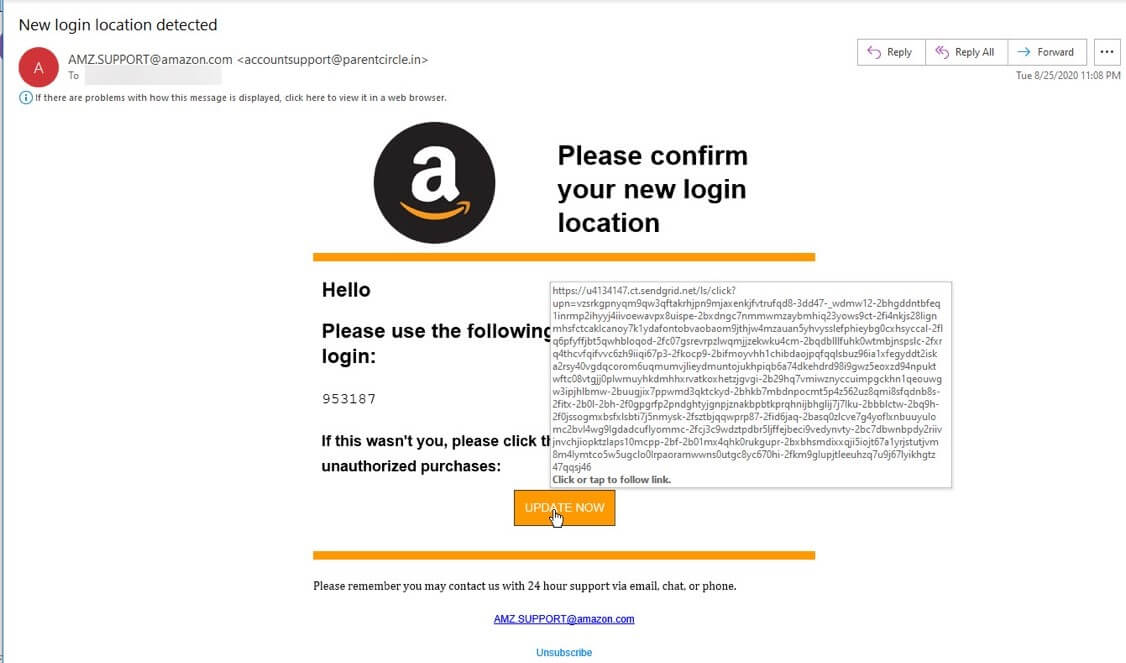
The attack email prompted the recipient to review the login attempt by clicking on an “Update Now” button embedded in their message.
Hovering over this button revealed a URL consisting of a SendGrid domain and a unique subdomain. Together, these elements culminated in the campaign redirecting the recipient to a phishing landing page designed to steal their Amazon account credentials.
PayPal
Just a day after it detected the fake Amazon email, Zix | AppRiver came across a similar imposter message from PayPal.
Those responsible for this campaign followed the same formula as the operation described above. They used spoofing techniques to trick the recipient into thinking that the attack email had originated from services@intl.paypal.com—just one character away from PayPal’s genuine email address service@intl.paypal.com. However, this email also originated from an email account affiliated with parentcircle.in.
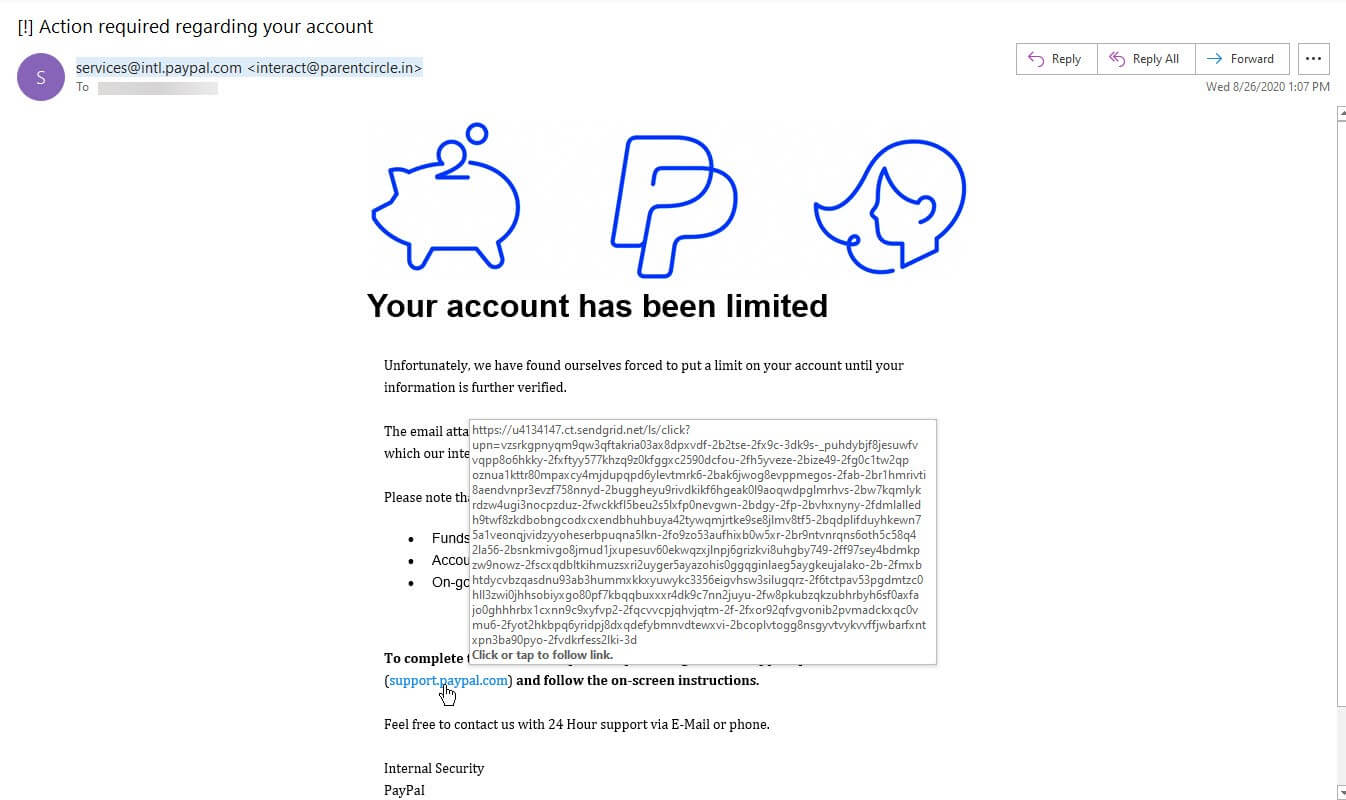
In this case, the attack email informed the recipient that they would have limited access of their PayPal account until they signed in and verified their information.
The message claimed that the recipient could rectify the issue by clicking on a URL that would redirect them to support.paypal.com. But the link didn’t send them to an official PayPal page. Instead, it sent them to a phishing landing page that used a SendGrid domain along with a unique subdomain to avoid detection by email filters.
WorldPac
At the end of September 2020, Zix | AppRiver came across the third and final attack email of its kind. The message used personalization tactics, including a subject line which read “Re: David, office meeting,” to lull the recipient into a false sense of security. It also addressed the recipient by their first name in the actual body of the email.
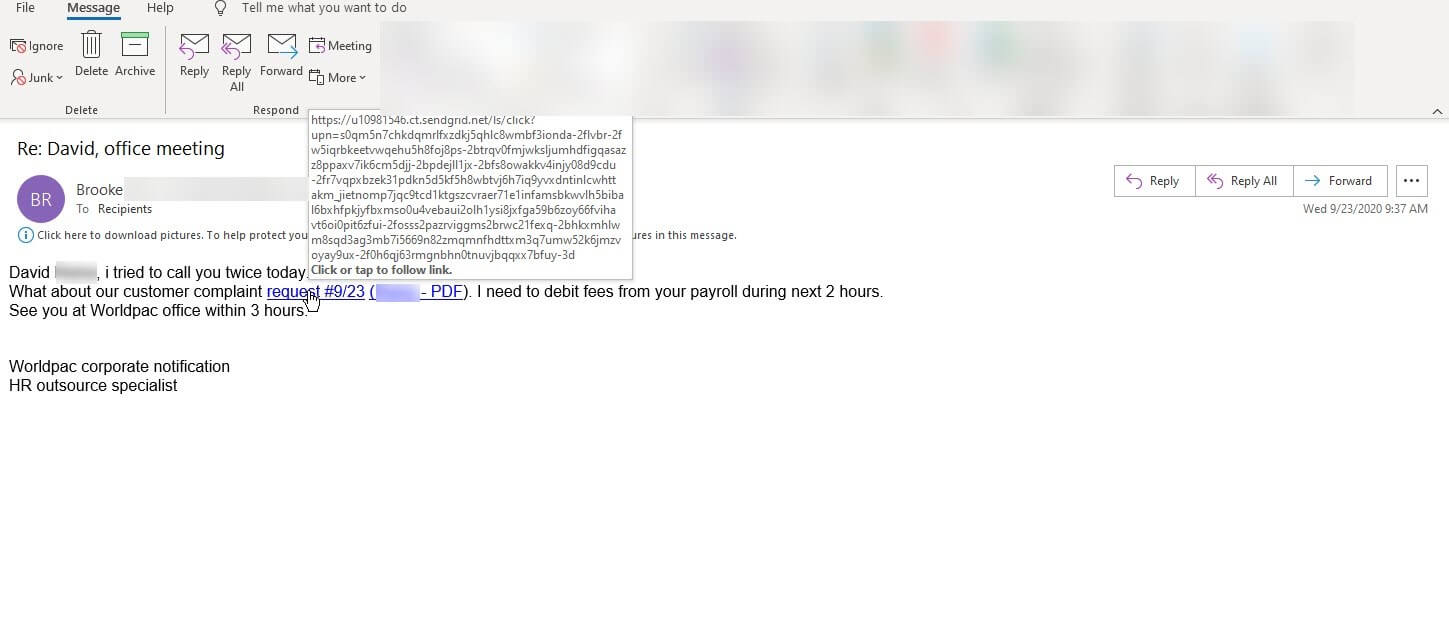
A screenshot of the fake WorldPac email. (Source: Zix | AppRiver)
For this attack, the malicious actors masqueraded as an HR outsource specialist named “Brooke” working at WorldPac, a wholesale distributor of OE parts for import and domestic vehicles. Brooke claimed that she had attempted to call David twice in the same day and stated that she needed to debit his payroll in the next few hours. She then directed him to view a customer complaint by clicking a link.
Like the other two attacks described above, this attack’s URL contained a SendGrid domain and a unique subdomain for the purpose of stealing the recipient’s account credentials.
Defending against Attacks Leveraging SendGrid
The three attack attempts described above highlight the need for organizations to defend themselves against email-based attacks. They can do so by investing in an email solution that scans incoming messages for malicious IP addresses, attack campaign patterns and other indicators of threat behavior. This analysis should occur in real time so that legitimate pieces of correspondence can reach their intended destination.
Learn how the email threat protection solution from Zix | AppRiver can help.
