Emotet’s at It Again!
Emotet has resumed operations nearly 10 months after an international coordinated action took control of the botnet’s infrastructure.
A Familiar Tactic
On November 15, the Zix | AppRiver team detected 221 email attack attempts from a revived Emotet botnet.
Some of the instances scraped entire conversations, while others scraped the subject and sender. With those techniques, attackers granted themselves the ability to inject themselves into conversations involving individuals with whom the sender had already spoken. This increased the likelihood of the sender (now the recipient) following the attackers’ instructions.
The commands themselves weren’t flashy. In one of their emails, the attackers asked the recipient to “please open the attached document.”
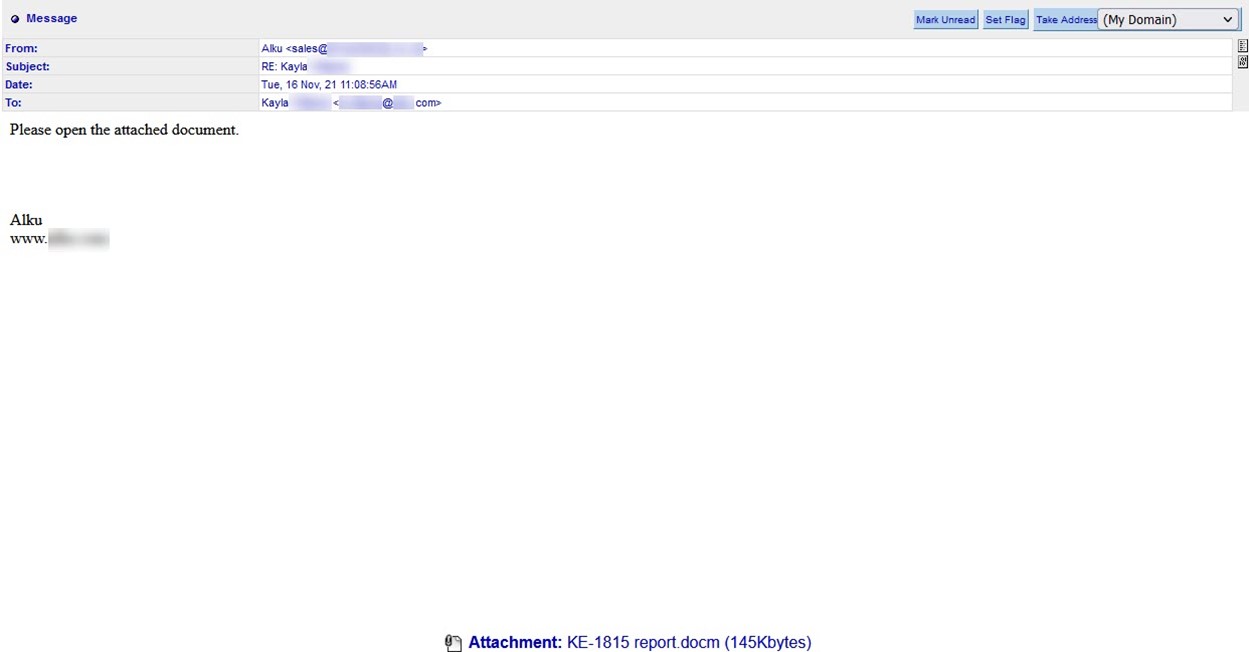
Another instance came with the instruction to “Please see attached” as well as the offer of assistance should the recipient need anything more.
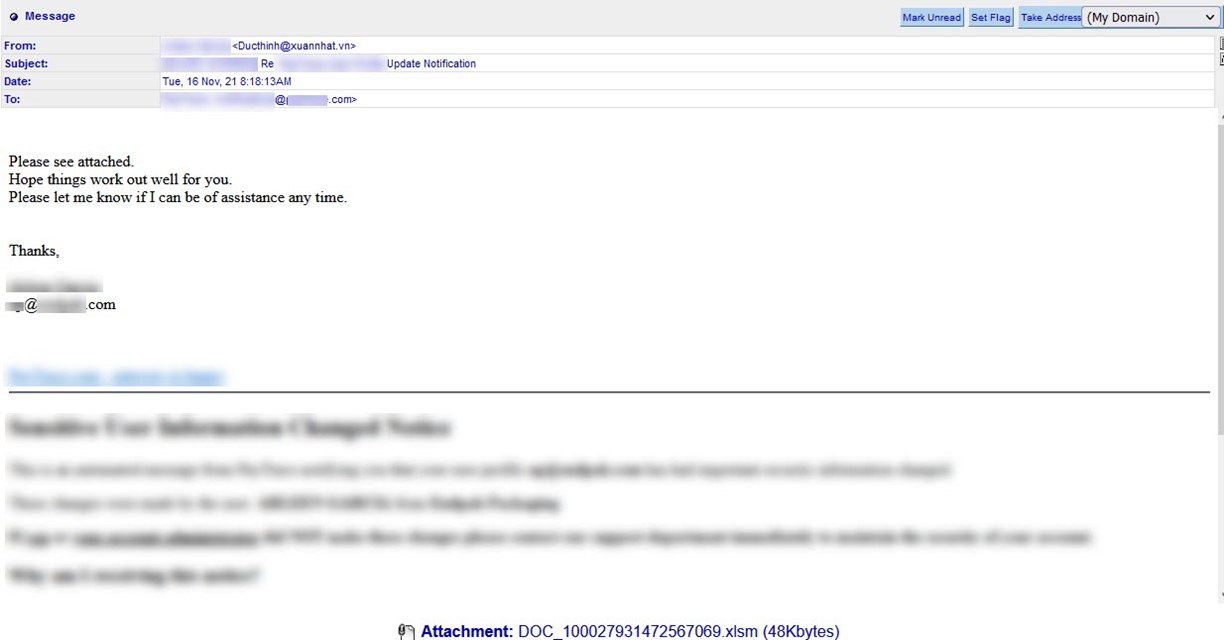
This isn’t the first time that malicious actors have used this tactic to distribute Emotet. Back in May 2020, for instance, Zix | AppRiver flagged an email as part of a conversation hijacking attack involving a request for a trade reference and bank reference. Ultimately, the email used a .ZIP archive to deliver Qakbot, a common payload of Emotet.
All the attack attempts detected by Zix | AppRiver arrived with Microsoft Excel spreadsheets, Microsoft Word documents, or password-protected .ZIP archives containing Word documents. Those files contained malicious macros that, when enabled, dropped Emotet.
Upon execution, Brad Dunction at the SANS Internet Storm Center spotted something familiar.
“Infection traffic for Emotet is similar to what we saw before the takedown in January 2021,” explained in a blog post. “The only real difference is Emotet post-infection C2 is now encrypted HTTPS instead of unencrypted HTTP. My infected lab host turned into a spambot trying to push out more Emotet malspam.”
Things didn’t slow down with Emotet after November 15. The following day, Zix | AppRiver detected 1,819 attack attempts involving the botnet. Those instances then fell to 665 on November 17.
A Familiar Friend Lent Some Help
Just as a bit of recap, law enforcement agencies in the Netherlands, Germany, the United States, the United Kingdom, France, Lithuania, Canada, and Ukraine with international activity coordinated by Europol and Eurojust announced the seizure of Emotet’s infrastructure in January 2021. The botnet went quiet for 10 months after that.
So, how did the botnet come back online?
Per Bleeping Computer, “active Trickbot infections began dropping the Emotet loader on already infected devices, rebuilding the botnet for spamming activity” in mid-November.
Trickbot has an established history with Emotet. Back in April 2019, security researchers spotted the trojan families working together to infect unsuspecting users with Ryuk ransomware.
Emotet’s takedown didn’t slow down Trickbot, however. On the contrary, Check Point Research wrote in October 2021 that Trickbot had remained at the top of its most wanted malware list for five months straight.
How to Respond to Emotet’s Return
Emotet’s reemergence highlights the need for organizations to strengthen their security against email-based attacks. One of the ways they can do that is by investing in their email security awareness training program. Through regular education modules, organizations can inform their employees about conversation hijacking and other attack techniques used by spammers.
Organizations need to balance those human controls with technical security measures. Hence the need for a multi-layered email security solution. By scanning emails for malicious IPs and other threat indicators, organizations can automatically protect themselves against many email-based attacks—all while allowing legitimate correspondence to reach its intended destination.
