The SolarWinds Threat Actor Returns with a New Phishing Campaign
The threat actor responsible for the SolarWinds supply chain attack is making headlines once again with a new email phishing operation.
How Far ATO Can Carry a Malicious Actor
On May 27, Microsoft Threat Intelligence Center (MSTIC) revealed it had uncovered a new wave of a spear-phishing email campaign that it had begun tracking in late-January.
This phase leveraged Constant Contact, a legitimate mass email service, to target 3,000 individuals at over 150 organizations.
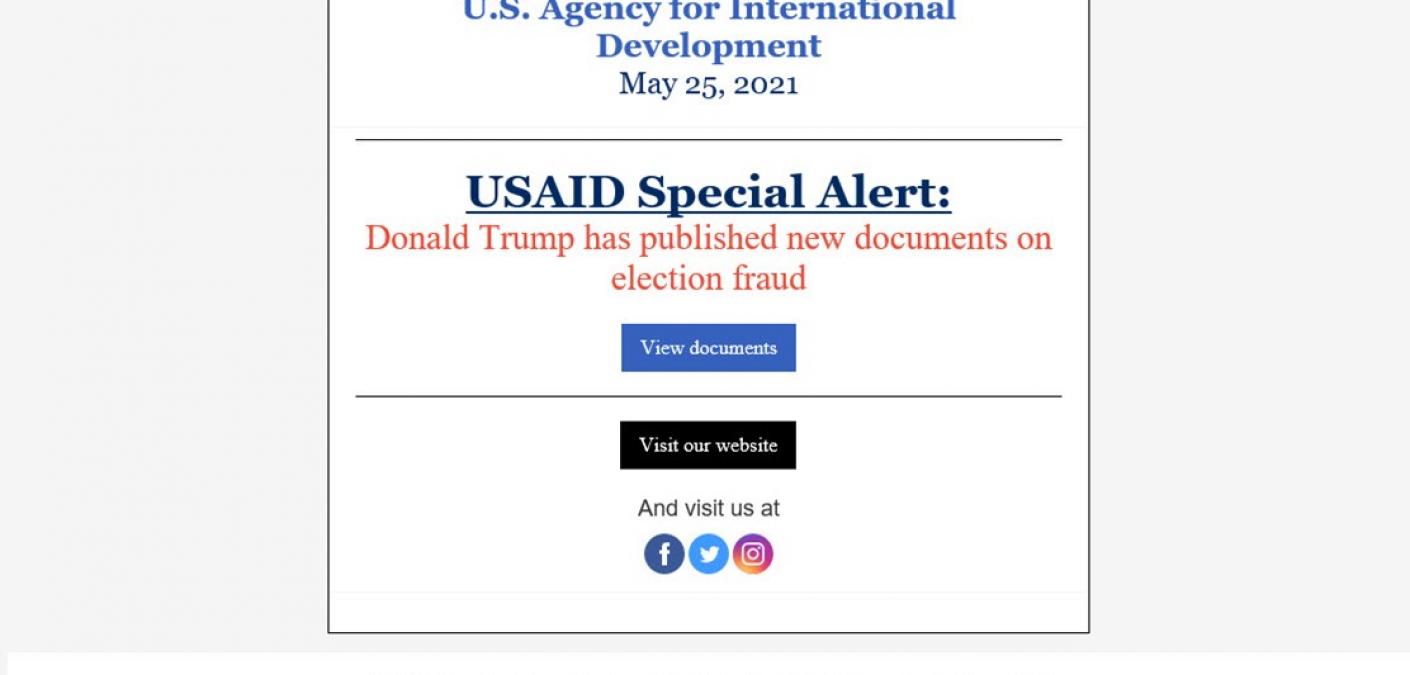
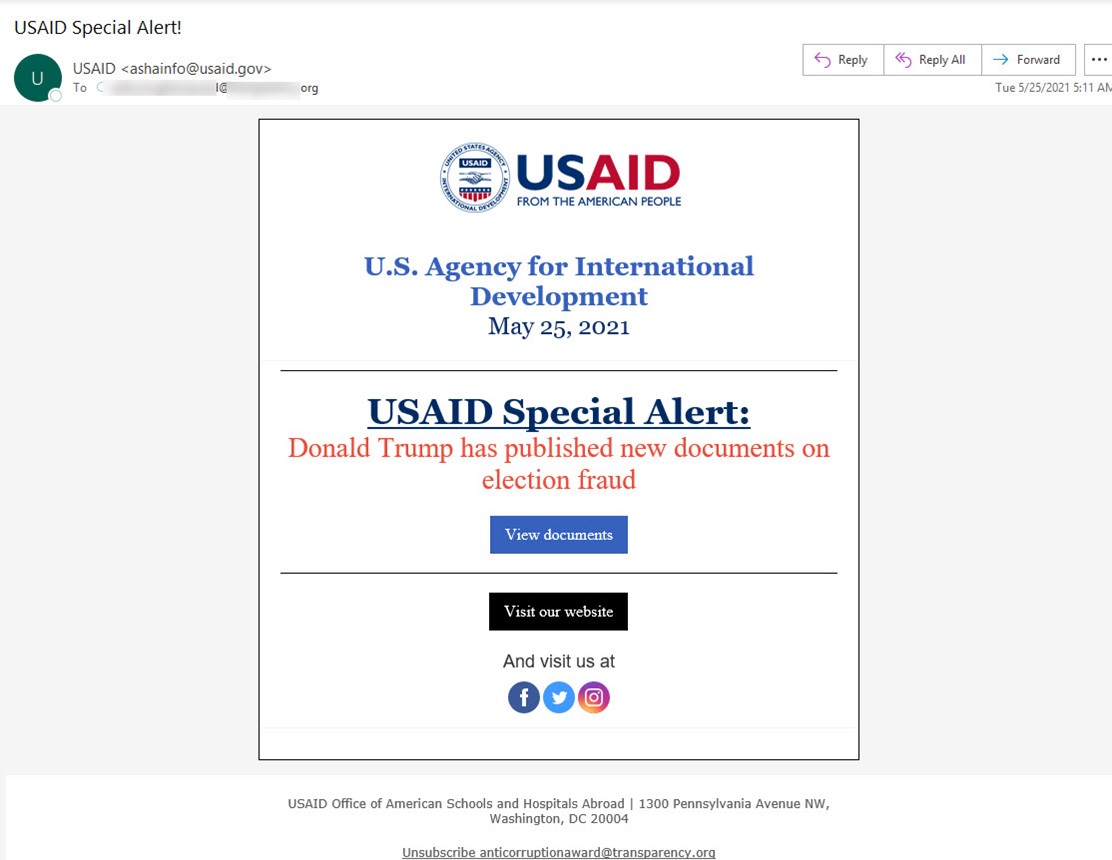
Microsoft’s researchers analyzed several instances of the attack. One of the iterations appeared to use “ASHAinfo@usaid.gov,” an email address employed by the Office of American Schools and Hospitals (ASHA) at the U.S. Agency for International Development (USAID).
The email masqueraded as a message from USAID warning of election fraud. In support of this disguise, the message used the subject line “USAID Special Alert!”
It also came with an authentic sender email address that matched Constant Contact.
After a recipient clicked on the “View documents” button, the campaign directed the recipient to the legitimate Constant Contact service.
The operation then redirected the recipient to infrastructure controlled by NOBELIUM, the malicious actors responsible for the SolarWinds supply chain attack.
This infrastructure subsequently infected the recipient’s system with a malicious ISO file. The file displayed a decoy document to the target to convince them that nothing was wrong.
In the background, however, the ISO file used a shortcut to run a custom Cobalt Strike Beacon loader dubbed “NativeZone.” Doing so enabled the NOBELIUM to achieve persistence on a compromised system so that they could move laterally, exfiltrate sensitive information and/or deliver additional malware payloads onto a victim’s compromised asset.
A spokesperson for USAID later confirmed that the Agency was “aware of potentially malicious email activity from a compromised Constant Contact email marketing account.” It went on to say that a forensic investigation into the attack was ongoing at USAID, as quoted by CNN.
Defending Against NOBELIUM’s Latest Attack
The team at Zix | AppRiver quarantined several of the campaign’s attack emails disguised as official USAID correspondence.
Those messages all used official USAID branding to lull recipients into a false sense of security.
Acknowledging those techniques, Microsoft noted that organizations could protect themselves by enabling cloud-delivered protection and EDR in block mode for Microsoft Defender. It also warned organizations to be on the lookout for alerts regarding the creation of uncommon files and/or the opening of link files with unusual characteristics.
Troy Gill, manager of security research and senior security analyst for Zix | AppRiver, explained that organizations need to do more, as well.
