Formbook Loader Distributed in Three “Extremely Aggressive” Email Attacks
Malicious actors launched three “extremely aggressive” email attacks in which they attempted to distribute samples of the Formbook loader.
Campaign #1: A Fake Wire Transfer Notice
Troy Gill, manager of security research at Zix | AppRiver, explained that Formbook has regularly made an appearance on the security firm’s systems since late 2021.
“Our malware filters have been capturing some extremely aggressive Formbook loader attacks over the past few months using multiple different ruses attempting to dupe recipients,” he said.
The firm detected the first attack email in mid-January. It arrived with the subject line “Wire request initiated,” and it used spoofing techniques to make the message appear as if it had originated from an American multinational financial services company.
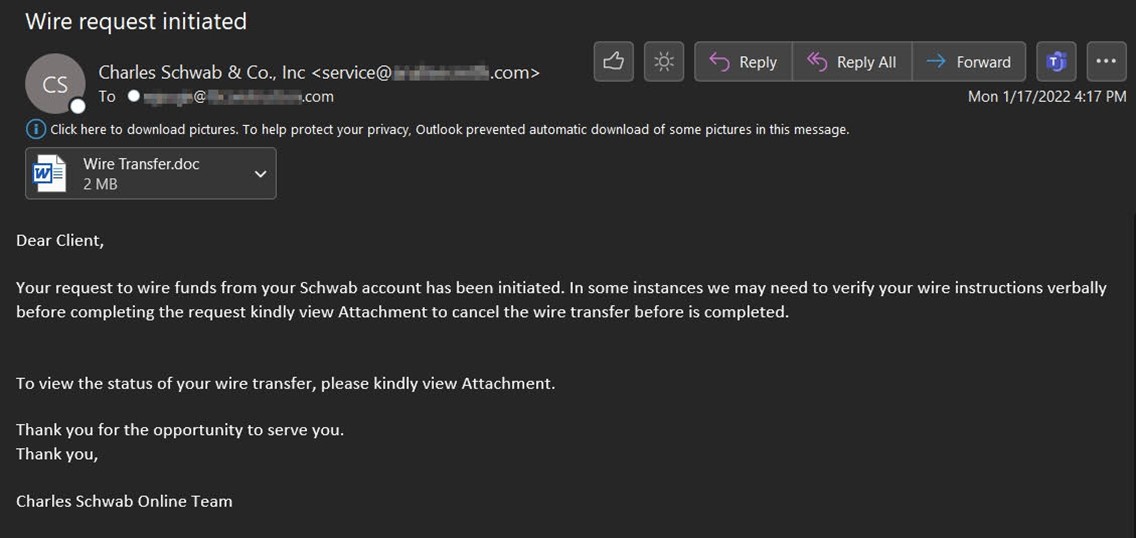
The email informed the recipient that the financial services company had begun processing a wire funds transfer request from their account. It went on to explain that the recipient could cancel the wire transfer by downloading a Word document. Once opened, the file downloaded a Formbook sample onto the recipient’s machine.
Campaign #2: A Bogus Letter of Dismissal
The Zix | AppRiver team came across the second Formbook attack campaign a few days later.
Using the subject line “Letter of Dismissal,” those who crafted the email claimed to be an unnamed “HR Manager” to try to convince the recipient that their employer was letting them go.
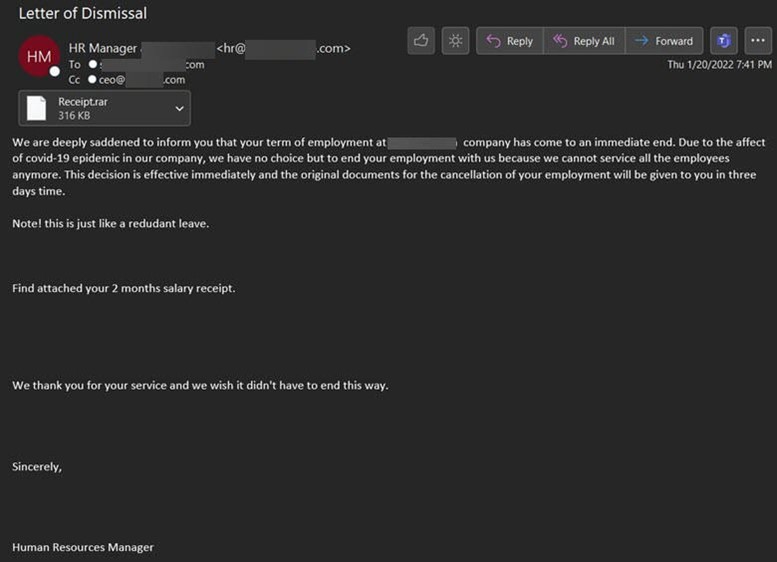
“Due to the affect of covid-19 epidemic in our company, we have no choice but to end your employment with us because we cannot service all the employees anymore,” the email stated.
The message went on to inform the recipient that the company had sent along a two-month salary receipt as an attachment. When opened, however, the attached .RAR file dropped Formbook as a payload on the victim’s computer.
Campaign #3: A Counterfeit Purchase Order
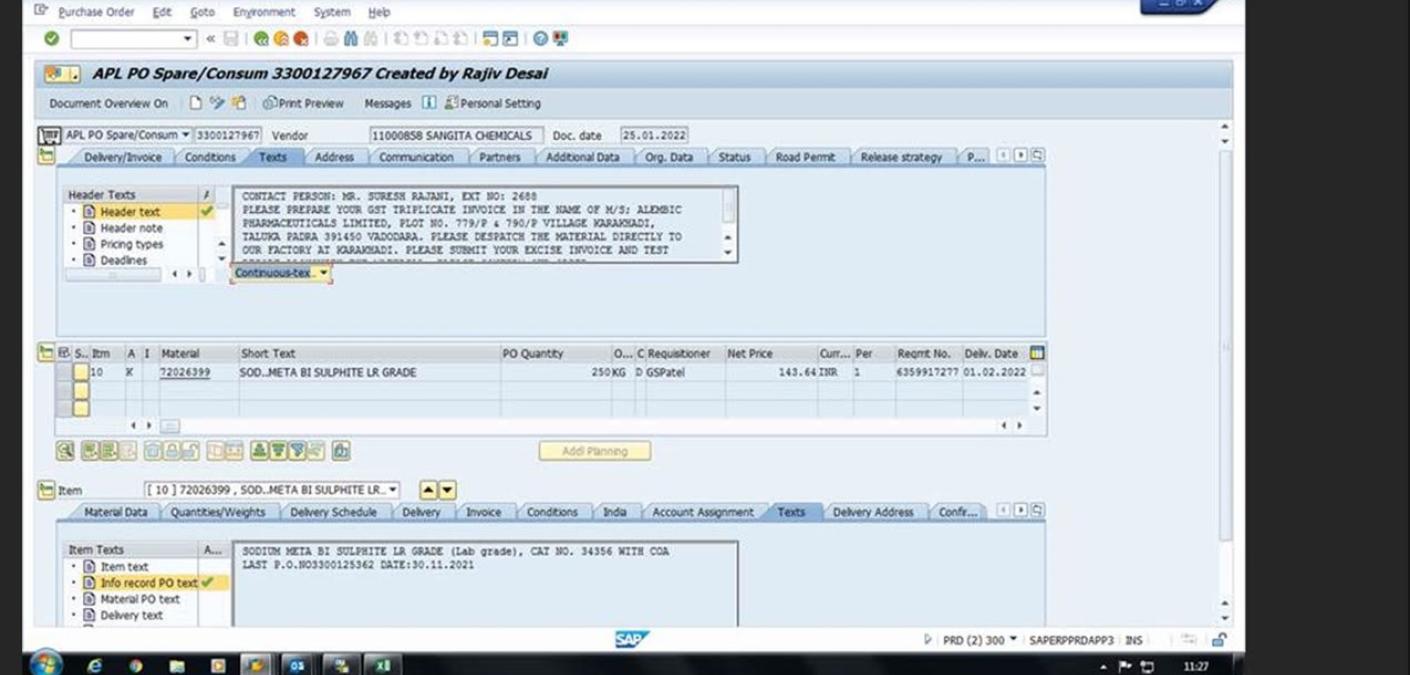
The final Formbook campaign came in the form of a minimalist attack email. It instructed the recipient to view a screenshot of a made-up purchase order embedded in the message.
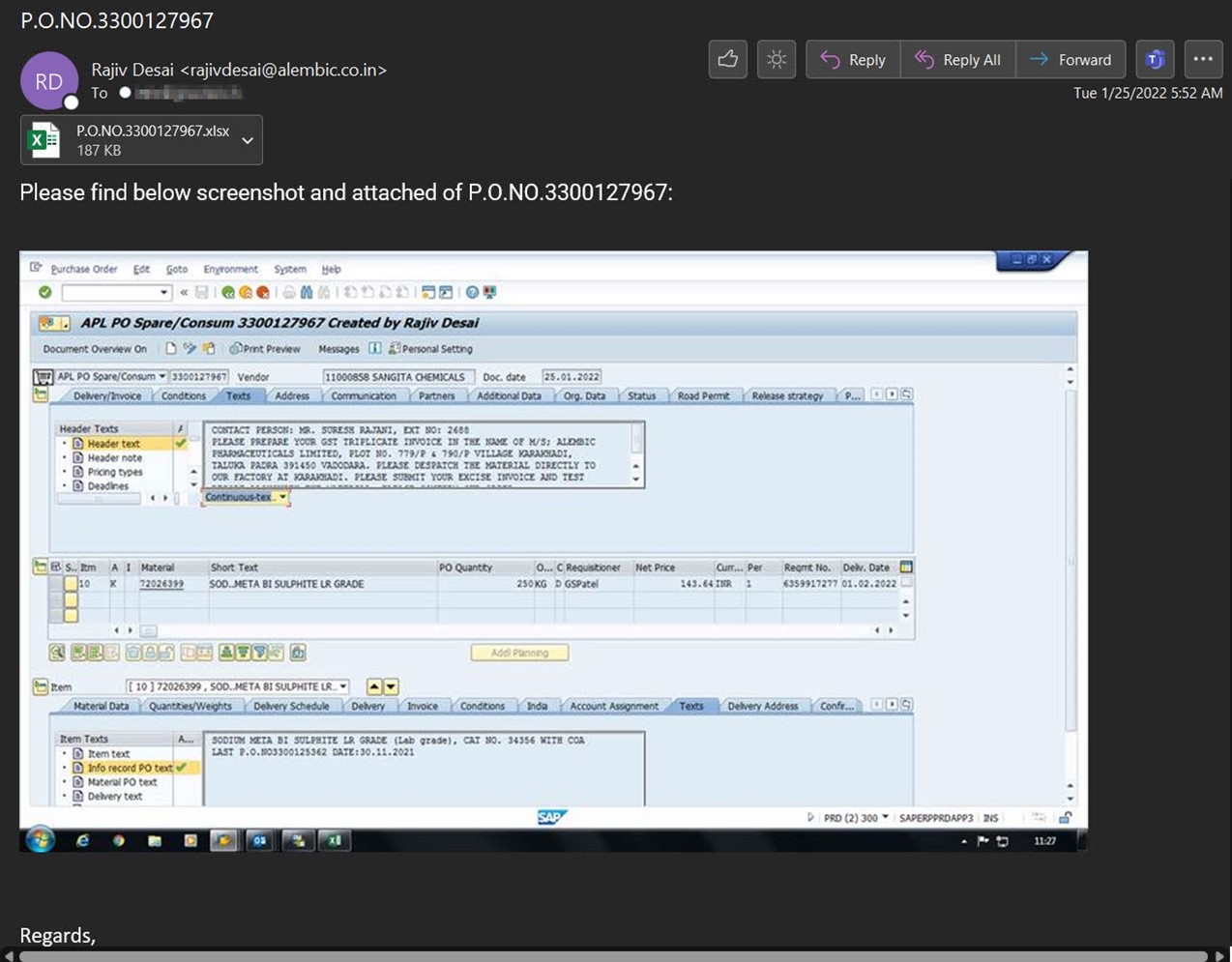
Those responsible for the campaign included the screenshot in their email to try to trick the recipient into opening a Formbook-laden Excel spreadsheet.
An Ongoing Relationship with Formbook
The attacks discussed above aren’t the first Formbook operations detected by Zix | AppRiver in the past couple of years.
Back in April 2020, for instance, the Zix | AppRiver team witnessed email attackers impersonating the U.S. Small Business Association (SMA). The malicious actors used that guise to trick the recipient into thinking they had received an SBA grant so that they would open an attachment. If the recipient complied, the campaign initially delivered the Remcos remote access trojan before eventually dropping Formbook.
It was about a year later when Zix | AppRiver flagged two additional Formbook operations. The first delivered the threat using malicious macros inside a deed-themed Word document. The other leveraged an “approved order” as a lure to deliver an executable file that began the Formbook infection process upon execution.
Defending Against Formbook Attacks
The attack campaigns discussed above highlight how organizations need to strengthen their email security postures against digital threats like Formbook. One of the ways they can do that is by investing in an email security solution that can scan incoming messages for malware signatures and other threat indicators. This type of solution, when combined with regular security awareness training, will help to prevent threats from gaining a foothold in employees’ inboxes, all while allowing legitimate messages to reach their intended destination.
