Fake Complaint Letter from American Spirts Company Leads to JSSLoader

Digital attackers used a fake letter of complaint from an American-owned spirits company to target recipients with JSSLoader malware.
A Look at the Phishing Email
In the beginning of June, the Zix | AppRiver team flagged a malicious email that appeared to come from the Brown-Forman Corporation.
The email arrived with the subject line “Letter of complaint – Brown-Forman Corporation.” The creators of the campaign also used spoofing techniques to disguise the email sender as Charlie Scholtz, vice president and associate general counsel at the spirits and wine company.
To add an additional sense of legitimacy to their email, the attackers used branding stolen from the company and included Brown-Forman’s contact information. They got everything right—even the corporation’s main telephone number and fax line.
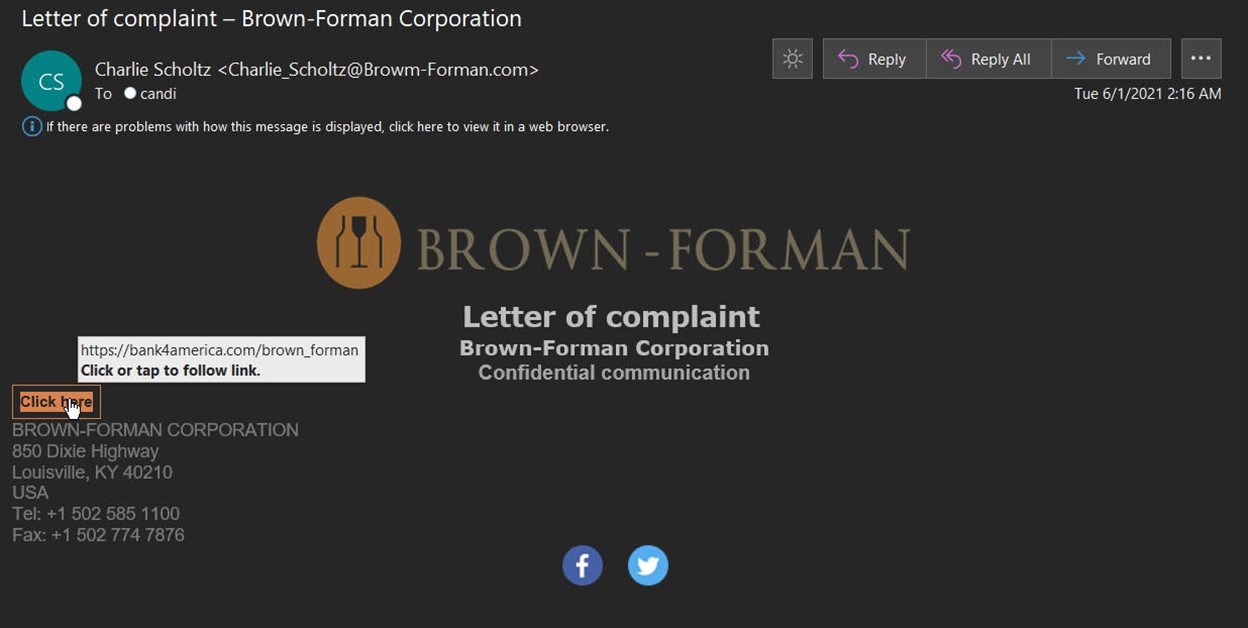
The “letter of complaint” didn’t come with any actual message text. It arrived only with a button that invited the recipient to view “confidential communication.”
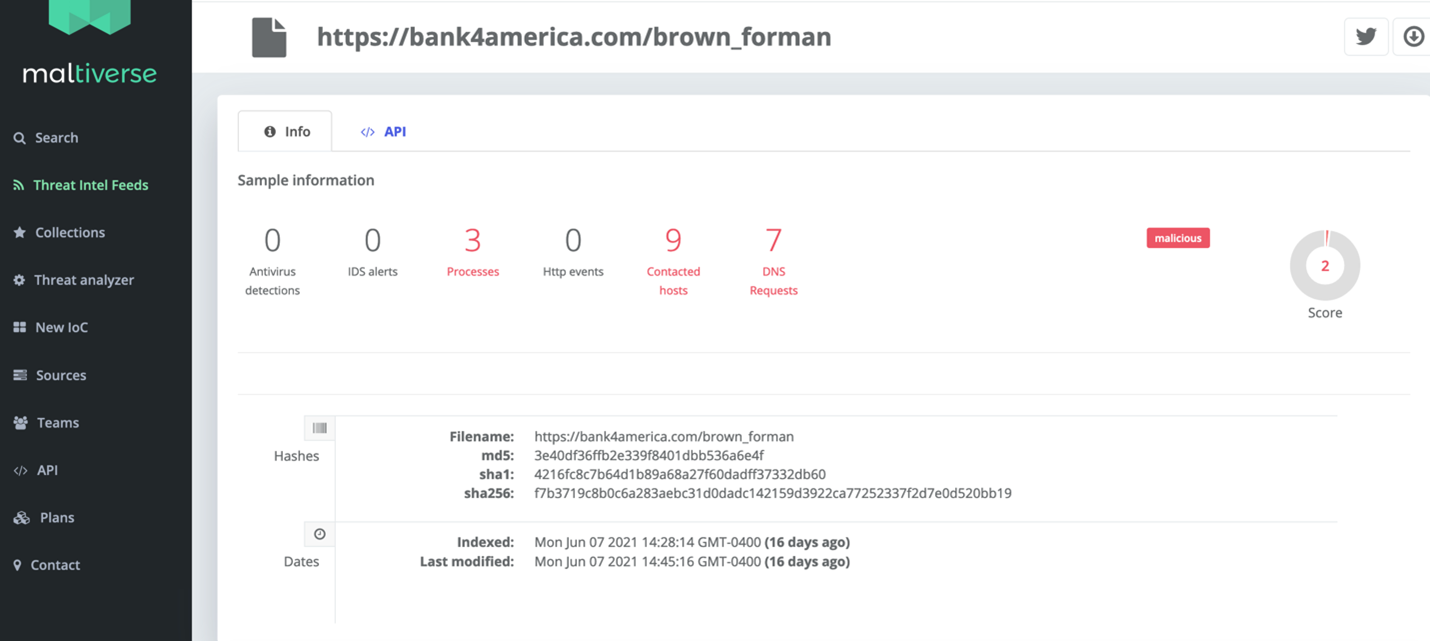
Hovering over the button revealed the domain “https://bank4america[dot]com/brown_forman.” According to thesiteRank, someone first registered the domain “bank4america[dot]com” back on March 12, 2021. It was about three months later when the IOC analysis service Maltiverse flagged “https://bank4america[dot]com/brown_forman” as malicious.
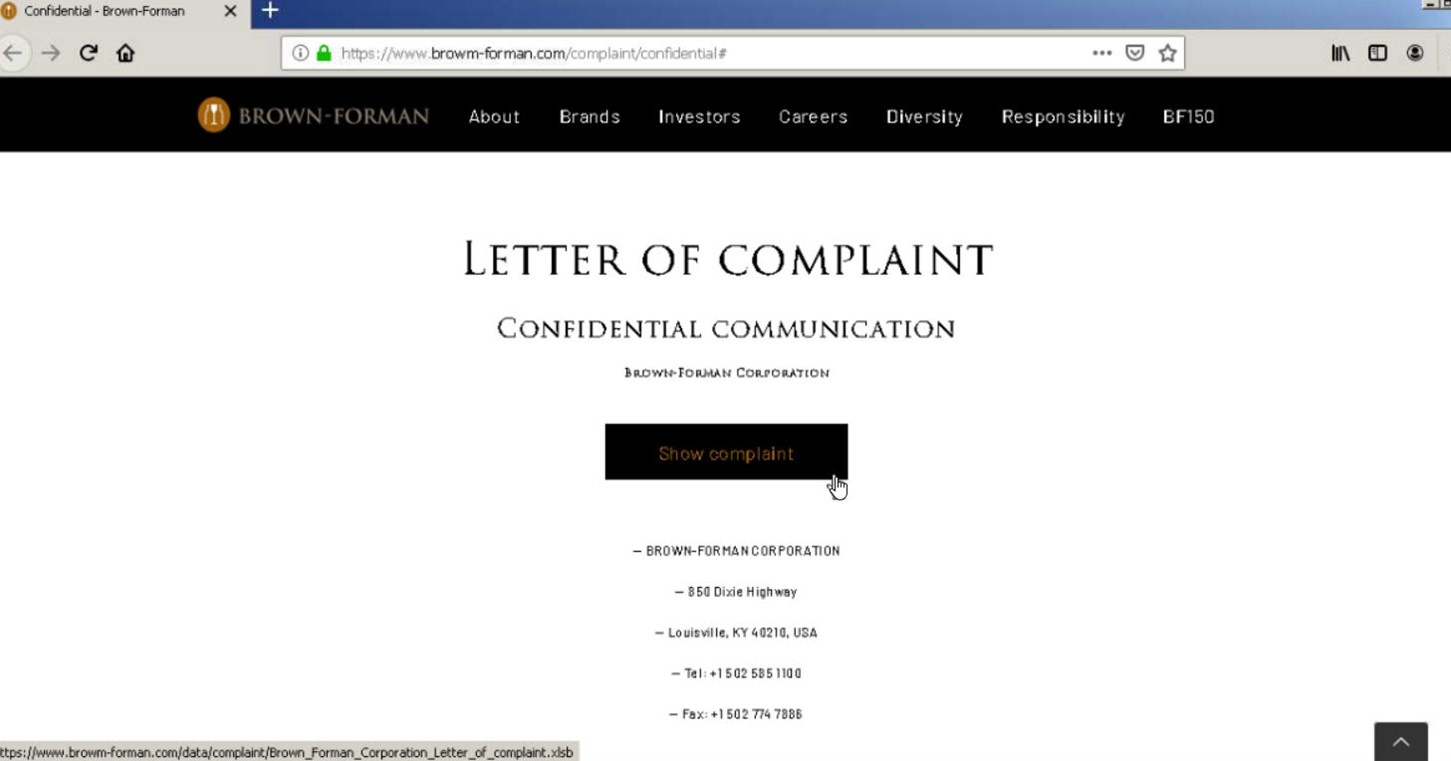
Troy Gill, manager of security research and senior security researcher at Zix | AppRiver, explained what happened if the recipient decided to click on the link.
“If the user proceeds, they were redirected from the original payload link to a site that was typo squatting Brown-Forman (Browm-Forman[.]com),” he said. “This site contained a page with a ‘Show complaint’ button linked to a .xlsb file (Excel with binary workbook) which drops their JSSLoader remote access trojan.”
An Overview of JSSLoader’s Evolution
Morphisec analyzed a JSSLoader sample that it discovered as part of an investigation in mid-December 2020. The variant of the remote access tool (RAT) began by creating a unique ID of the victim based on the serial name, domain name, and computer name. This identifier ultimately helped the threat to engage in other forms of malicious activity. These included the following:
- Anti-debugging: JSSLoader leveraged an anti-debugging feature called “TickCount” to perform timing checks on the infected machine.
- Exfiltration: The RAT gathered the username, Active Directory Information, and seven other pieces of information. It then base64 encoded the data before sending it off to its command & control (C&C) server located at a preconfigured URL.
- Persistency: To achieve persistence, the malware created a shortcut shell LNK via com IShellLink in the startup directory that pointed to the executable.
- Execution: After achieving persistence, JSSLoader waited for a base64-encoded command string delivered by a ‘Get’ command from the same domain that it sent to the exfiltrated data. The command might have contained instructions to execute a PowerShell command in memory, write and execute a DLL or to update the threat, as examples.
Defending Against Spirited Email Scams
The scam discussed above highlights the need for organizations to defend themselves against email-borne malware attacks. One of the ways that organizations can do this is by investing in an email security solution that’s capable of scanning incoming email messages for campaign patterns, malware signatures, IP addresses, and other threat behaviors. This solution should perform this analysis in real time so that legitimate correspondence can reach its intended destination within the business.
