DocuSign Abused by Phishers to Target Victims’ Email Account Credentials
Digital attackers launched a phishing campaign in which they abused DocuSign to steal victims’ email account credentials.
The Latest Living Off the Land Phishing Example
At the end of September, the Zix | AppRiver team flagged an email that arrived with the subject line “Please DocuSign: Proposal Shared Document Online.pdf.”
The screenshot below reveals that the attack email originated from DocuSign. Like other notifications sent out by the service, the email listed one of DocuSign’s North American Services (“DocuSign NA4 System”) as the sender. It also came from the legitimate sender email address “dse_NA4@docusign.net” used by DocuSign for official correspondence.
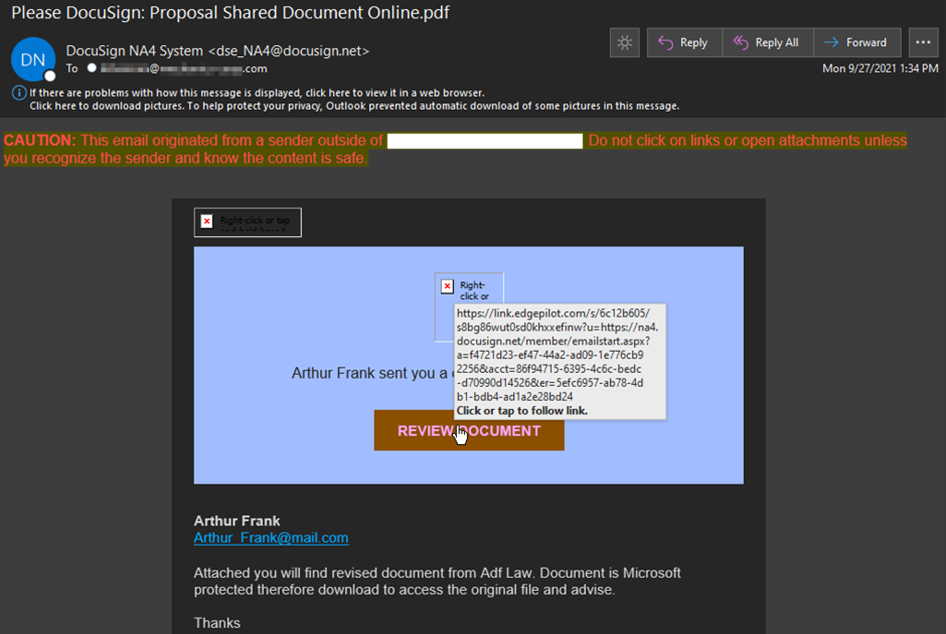
The body of the email appeared to be an invitation from one Arthur Frank of “Adf Law” for the recipient to review a document. As you can see from the broken grammar used by Arthur in his note to the recipient, something phishy was going on with this email.
“Attached you will find revised document from Adf Law,” the attackers said in the email. “Document is Microsoft protected therefore download to access the original file and advise.”
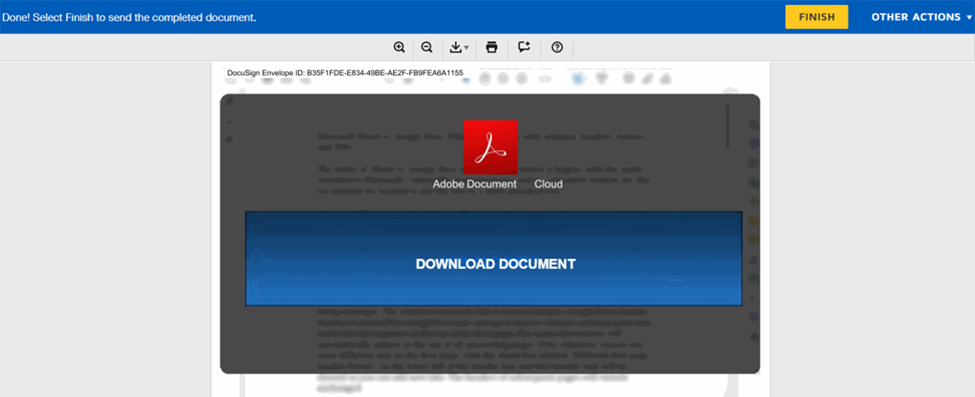
Clicking on the “Review Document” button redirected the victim to an HTML file hosted on DocuSign’s servers.
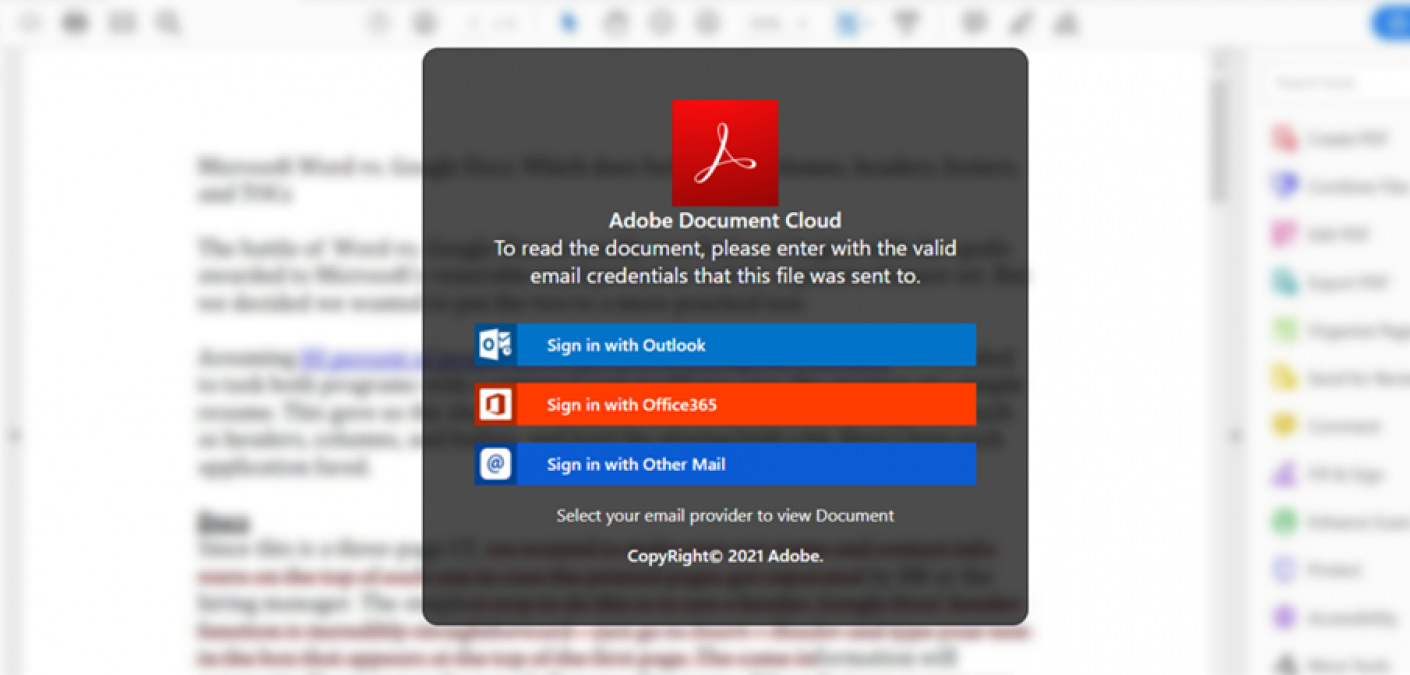
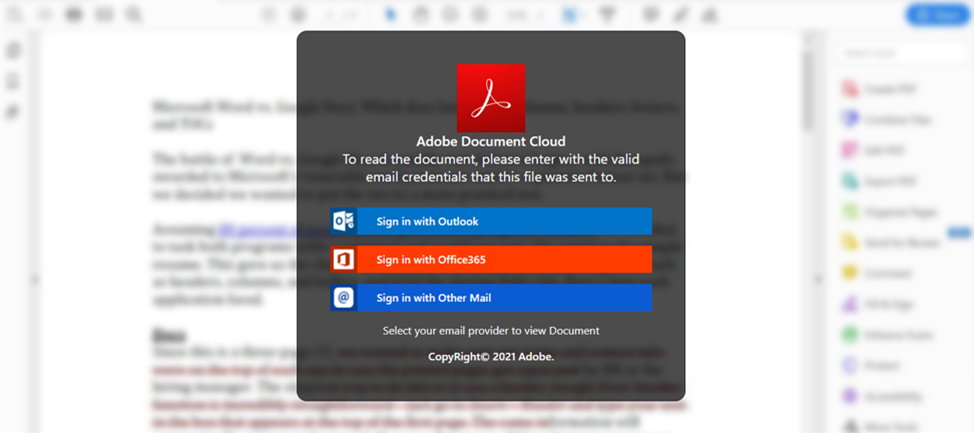
Once downloaded, the HTML file brought up a credential harvesting page. It prompted the victim to sign in with Outlook, Office365, or another mail client for the purpose of reading a document hosted in Adobe Document Cloud.
Other Phishing Attempts Involving DocuSign
This isn’t the first time that digital attackers have abused DocuSign to conduct a phishing campaign. Back in August, for instance, news emerged of a campaign in which phishers leveraged DocuSign to host malicious links despite the service’s ongoing efforts to prevent such instances of abuse. TechRadar pointed out that digital attackers could specifically use steganography within a hosted file to deliver threats like malware or ransomware to evade those preventative measures, for instance. They could also use specific documents like PDFs to preserve embedded hyperlinks’ clickability—all while evading security checks employed by DocuSign and third-party email security solutions.
It was a few weeks later when DocuSign itself revealed it had observed a “new phishing campaign in which malicious URLs are being hidden in legitimate DocuSign envelopes.” That campaign used various senders and email addresses to send out the attack emails, and they arrived with subject lines such as “Important: Microsoft Email Maintenance Request,” “Bank Confirmation,” and “INVOICE.pdf."
How to Defend Against Phishers Abusing DocuSign
The attack campaigns described above highlight the need for organizations to defend against phishers using Living off the Land (LOTL) tactics to prey on DocuSign and other legitimate services. One of the ways they can do that is by using security awareness training to cultivate their employees’ level of suspicion for unexpected emails containing unknown attachments. With that said, they need to foster a culture where reporting these types of emails is encouraged and not overlooked or dismissed.
Simultaneously, organizations need to augment their technical capacity to defend against these types of emails. They can do so by investing in an email security solution that analyzes incoming messages on multiple levels including IP addresses, campaign patterns, and malware signatures. This analysis should occur in real time so that legitimate correspondence can reach its intended business destination without delay.
