Phishers Impersonating Maersk Line to Steal Victims’ Email Credentials
Phishers launched an attack campaign in which they impersonated Danish international container shipping company Maersk Line to steal victims’ email account credentials.
“Confirmation of Shipping Invoice” Scam
At the end of October, the Zix | AppRiver team flagged an email that appeared to have originated from Maersk Line
Those responsible for the campaign used stolen branding to impersonate the shipping giant. They even included the text “Best Global shipping company” in their message. As noted by FleetMon, Maersk Line won this exact distinction for at least 20 consecutive years at the Asian Freight & Supply Chain Awards (AFSCA).
Even so, the attackers slipped up a few times in their email.
First, they used inconsistent capitalization with “Best Global shipping company,” “Original copy of Shipping Docs,” and even the subject line “Confirmation of shipping Invoice,BL & Parking List [sic].” These errors might have raised a recipient’s suspicions.
Second, they used spoofing techniques to trick the recipient into thinking the email came from “Maersk Global Shipping,” with the sending email address “noreply@maersklineshipping[dot]com.” But that’s not a legitimate Maersk Line email address. Official correspondence from the shipping giant uses the domain “@maersk.com.”
Finally, the attackers included a signature block attributing their email to Mark Rosario of MaerskLine China. There appears to be a Mark Rosario who does work at Maersk. But according to this individual’s LinkedIn profile, he’s been associated with the company’s operations in Pakistan for over 20 years, not China.
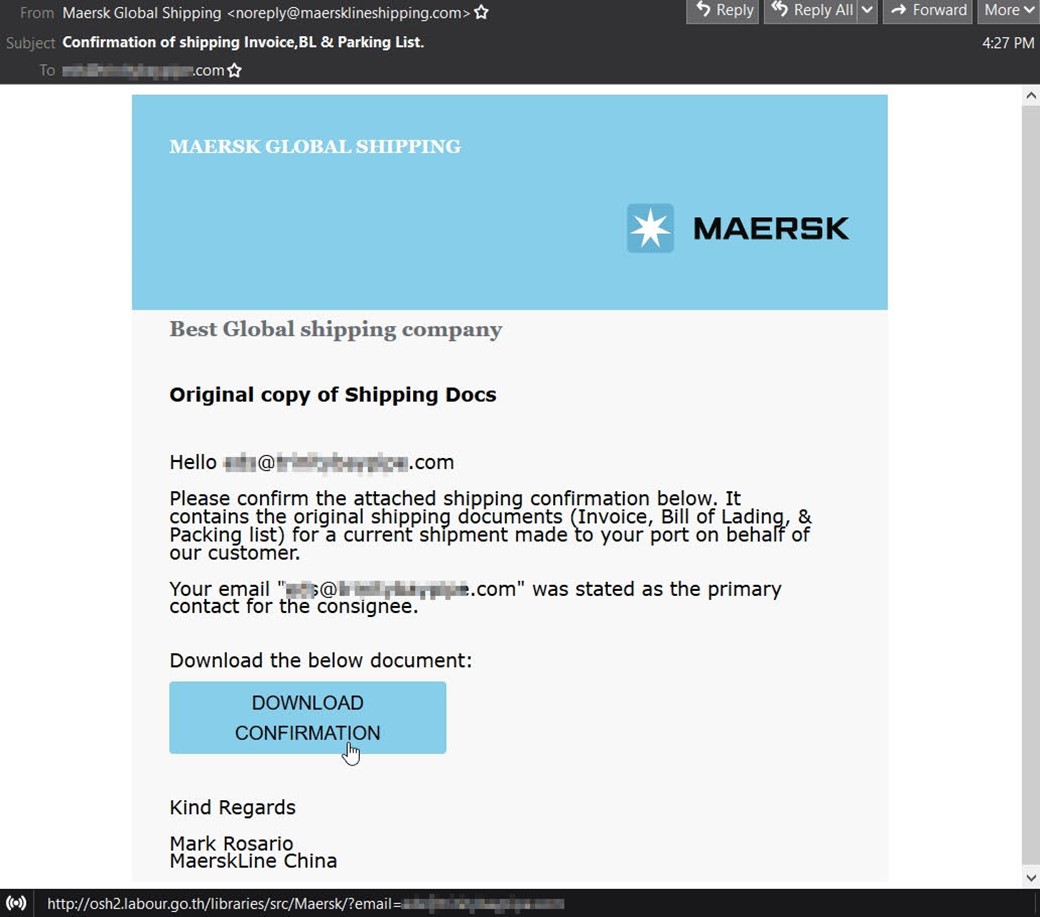
The email instructed the recipient to view some original documents including an invoice, bill of lading, and packing list by clicking on an embedded “Download Confirmation” button.
Troy Gill, manager of security research at Zix | AppRiver, explains what happened next.
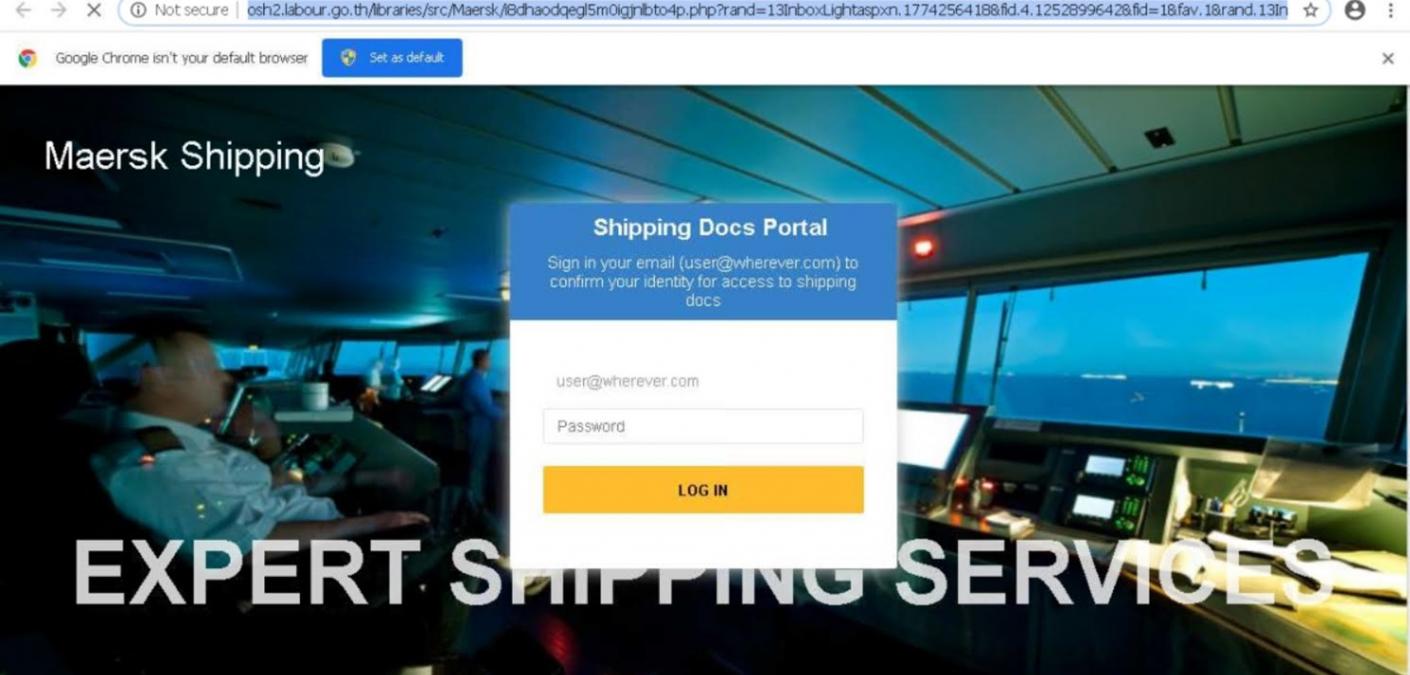
“If the user complies, they are directed to a very convincing phishing page located on labour.go[.]th,” he said. “The page cycles through different realistic-looking Maersk backgrounds with a sign-in screen overlayed to steal the users email credentials.”
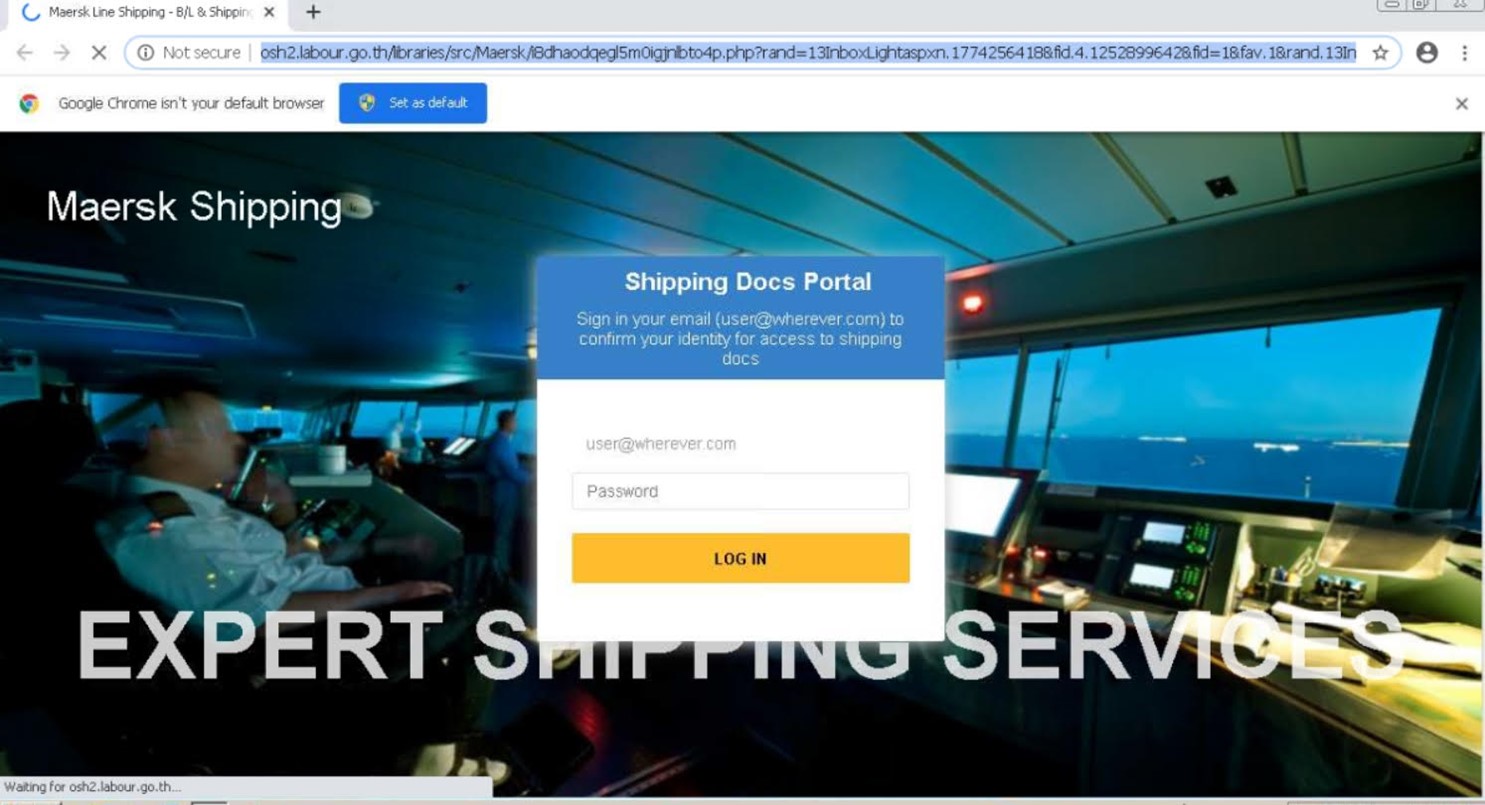
“Per whois DNS data, the domain itself appears to be a Thai government page managed by the Labour Protection and Welfare Department. We were also able to find that it has a history of over 3 years of being abused for phishing attacks, mostly Adobe themed in the past,” he added.
Putting This Attack into Context
The attack described above arrived amid ongoing global supply chain challenges caused by the pandemic. In June 2021, for instance, The White House explained that some industries had shrunk or closed in response to the events of 2020. Some businesses struggled to hire quickly enough as they tried to reopen, while others didn’t have enough inventory to immediately resume their previous levels of business activity.
These events help to explain why 36% of small businesses reported delays with domestic suppliers, according to a U.S. Census Small Business Pulse survey cited by The White House. It also helps to put other events such as abrupt price increases, shortages, and digital attack campaigns impersonating shipping companies into perspective.
“With so many shipping delays and supply shortages around the world, threat actors are eager to spoof logistics and supply chain companies hoping for an easy compromise,” Gill clarified.
Attacks such as the one discussed above didn’t begin with the pandemic, however. Back in May 2019, for example, Maersk published an article warning of a phishing scam where fraudsters used genuine Maersk employee names and positions when contacting customers to trick them into clicking on a link, downloading an attachment, and/or authenticating their information.
Such activity highlights the need for organizations to invest in employee security awareness training and invest in an email security solution capable of spotting new attack attempts.
