Emotet Actors Use Conversation Hijacking Attack to Deliver Qakbot

The malicious actors behind the Emotet malware family are now leveraging conversation hijacking attack techniques to deliver the Qakbot banking trojan.
Inside the Latest Emotet Malware Campaign
Troy Gill, manager of security research at Zix | AppRiver, explains that those behind Emotet are preying upon users with other malware:
"In addition to delivering their own malware, we have recently observed the Emotet operators’ assets being used to deliver other forms of malware such as Zeus Panda, IcedID, Trickbot and Qakbot. This indicates that they are continuing to monetize their delivery assets as a service to maximize their returns, which is something they have been up to for quite a while now."
The security research team at Zix | AppRiver came across one such campaign in early May. This particular operation relies upon what’s known as conversation hijacking attacks to prey upon users. As we detailed in an earlier blog, these attacks begin when malicious actors step up the phishing traffic confronting a targeted organization. Those attack emails attempt to entice recipients into clicking on a link embedded in a PDF document. When clicked, those URLs redirect recipients to a phishing landing page where they’re prompted to select an email provider of their choice and then submit their login details.
With these compromised credentials, malicious actors begin phase two of their attacks by authenticating themselves with their victims’ accounts. They abuse that access to sift through their victims’ email accounts and find conversations into which they can inject themselves. Usually, they look for conversations dealing with invoices or quotes of services so that they can infect their victims’ correspondents with banking malware.
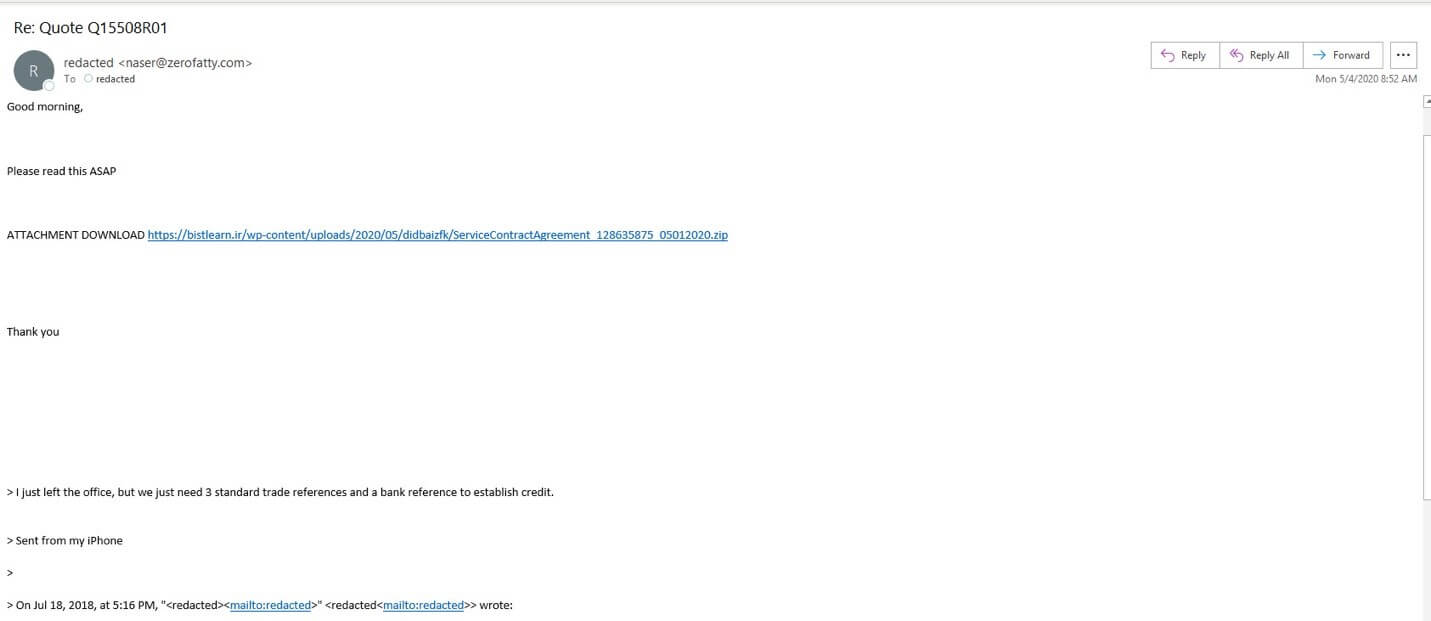
Which brings us back to this campaign. The operation occurs in phase two of a conversation hijacking attack, as the phishing email arrives within the context of an ongoing email thread concerning quotes for service. In response to a legitimate request for trade references and a bank reference, the attackers inject themselves into the thread and ask that the recipient read an attached document as soon as possible. The email leverages “Re: Quote Q15508R01” as its subject line, and it originates from the email address “naser@zerofatty[.]com.” (Zero Fatty is a health food restaurant located in Saudi Arabia.)
So, where does the embedded link lead the recipient?
It brings them to a .ZIP archive that masquerades as a service agreement—something which the recipient did not request in their business conversation. That .ZIP file contains a VBScript file that, when run, pulls down a sample of Qakbot as its malware payload.
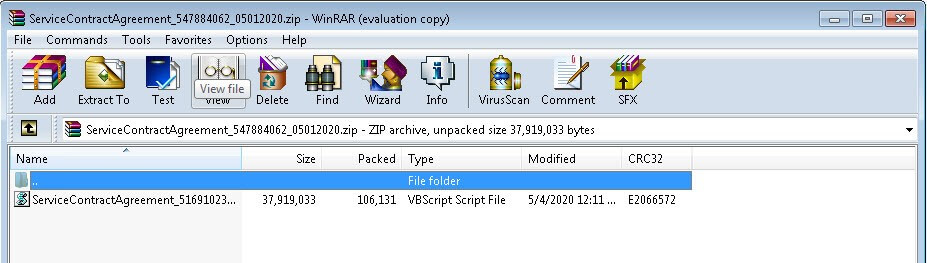
Qakbot is not a new payload of Emotet. In its Global Security Report – End of Year 2018, AppRiver disclosed Emotet’s penchant for distributing banking trojans such as Qakbot along with the AZORult remote access trojan (RAT) and ransomware families such as BitPaymer and Ryuk. Follow-up reports in the middle and end of 2019 confirmed this same behavior.
Defending Against Emotet Attack Campaigns
In light of the Emotet attack operation discussed above, organizations need to defend themselves against phishing campaigns and conversation hijacking techniques. One of the best ways they can do this is by strengthening their email security defenses. In particular, they should invest in a solution that’s capable of using machine learning, sandboxing and other security tools to analyzing incoming messages for URLs, malware signatures other indicators associated with known attack campaigns. This analysis should occur in real time so that the legitimate messages can find their way to their intended destinations without any disruptions.
Learn how Zix | AppRiver can help defend you against this and future email-based Emotet operations.
