Phishing Attacks in H1 2021 Stood out for Their Levels of Sophistication
Many of the phishing attempts flagged by Zix | AppRiver in the first half of 2021 distinguished themselves for their levels of sophistication.
An Evolving Threat Landscape
In its Mid-Year Threat Report 2021 , the Zix | AppRiver team revealed that some email attackers had tried out some new techniques for the purpose of customizing their campaigns.
One tactic grabbed the researchers’ attention in April when they spotted a “Let’s Encrypt Error Message” informing domain owners about a “conflict in SSL/TLS certificate algorithm.”
The attack email came with a personalized subject line that included the name of the recipient. Not only that, but it took the extra step of pulling real certificate data and the DNS A-record from the recipient’s domain, information which it then included in body of the email.
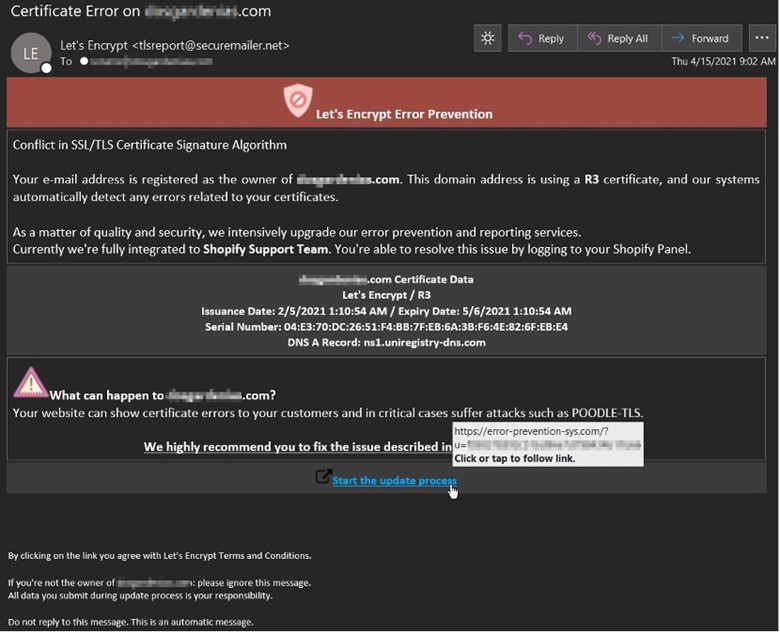
“It is not often we see an attack technique we would classify as a ‘first,’” said Troy Gill, manager of security researcher at AppRiver, as quoted in blog post. “That said, we predicted we would see attackers further personalizing and customizing their attacks this year, and this phishing attack fits the bill. We don’t recall ever seeing the cert info being leveraged like this.”
Other malicious actors focused on incorporating greater levels of obfuscation into their efforts.
Back in mid-February, for instance, the Zix | AppRiver team came across an email that attempted to lure recipients into opening a payment notice.
That attachment arrived as an .HTML attachment containing a Morse Code function, something for which many email security solutions lack detection rules.
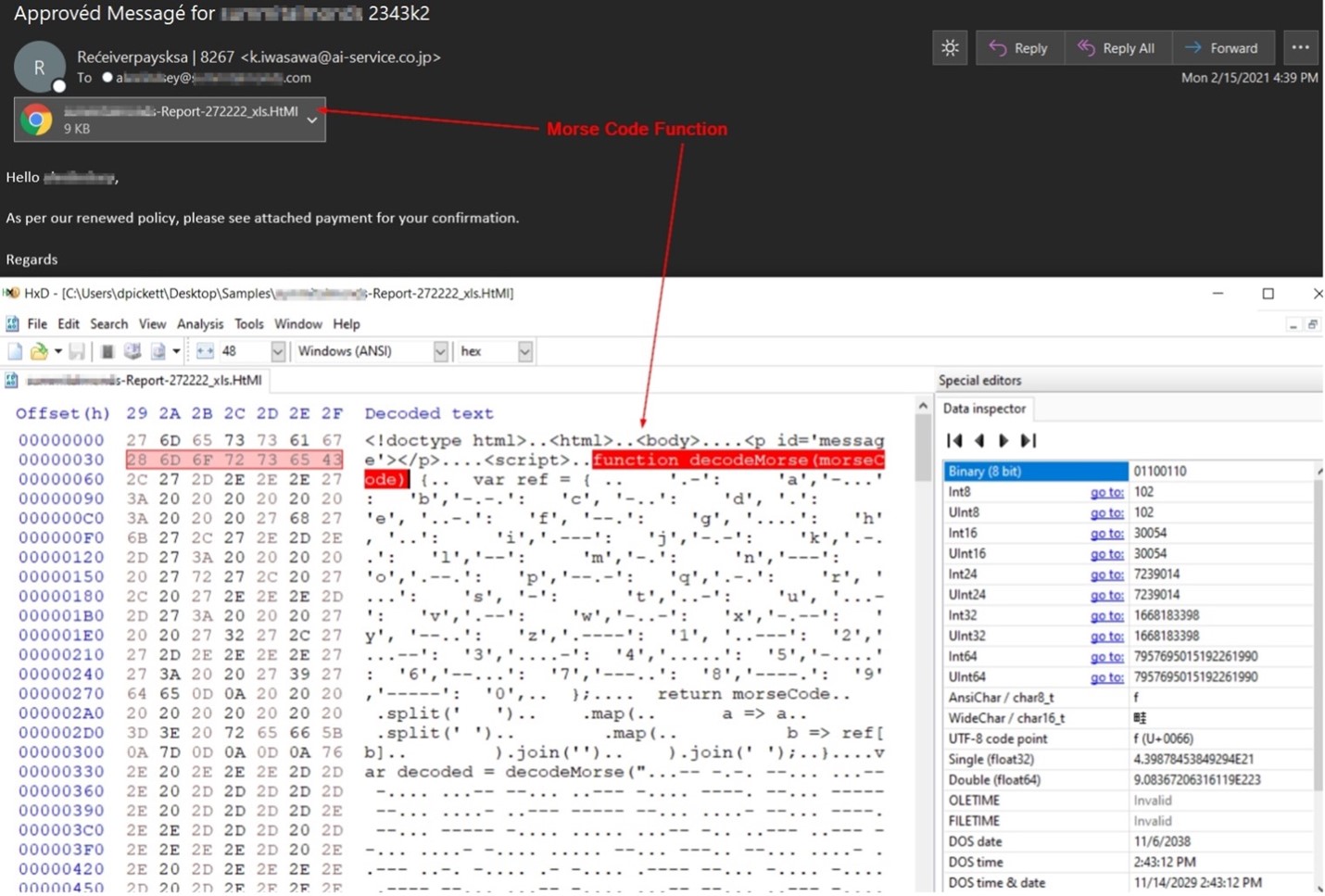
When opened, the operation displayed what appeared to be a blurred-out Excel file with a fake login screen customized for the recipient’s employer. The purpose of that disguise was to harvest a recipient’s account credentials and exfiltrate those details back to the attackers.
It was around that same time when even more obfuscation drew the attention of Zix | AppRiver. This time, attackers informed a recipient that a billing issue had resulted in the cancellation of their Spotify subscription.
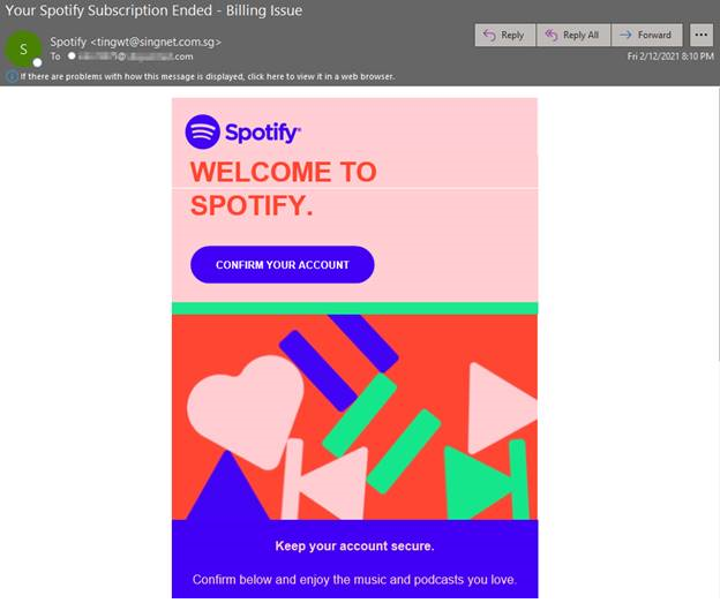
The attack email prompted the recipient to resolve the issue by clicking on an embedded “Confirm Your Account” button. In the event they complied, the operation brought the user to a CAPTCHA security challenge, an intermediate step that helped to shield the attack from traditional email security solutions.
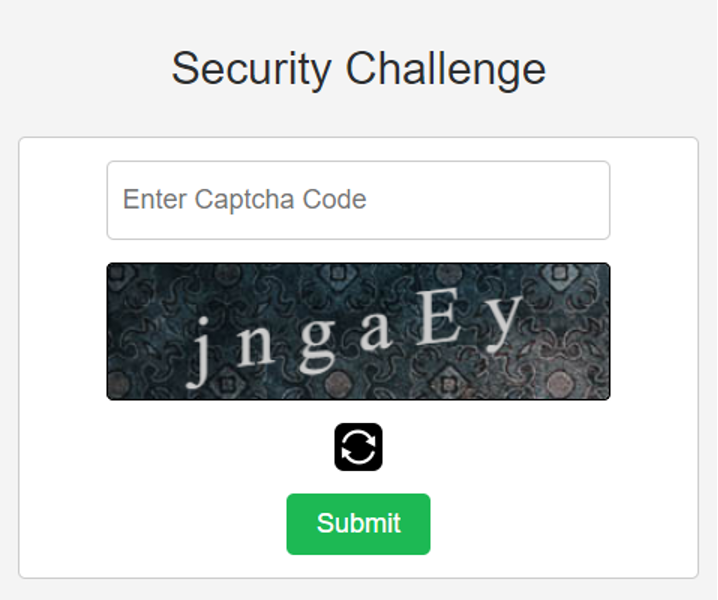
Upon completing the CAPTCHA challenge, the recipient found themselves redirected to a convincing Spotify credential harvesting page.
Defending Against Email Attack Customization and Obfuscation
To help organizations defend themselves against the techniques discussed above, Zix | AppRiver decided to include several changes in version 6 of its Microsoft 365 Security Audit tool. One of the most important changes is the fact that reports within the Secure Audit tool are now more actionable and digestible. Users can customize and configure reports based on the domain and tenant as well as run them directly from Zix’s Secure Cloud platform. These options ensure that they won’t have to sift through irrelevant data to protect their customers against increasingly sophisticated email attackers.
Version 6 also comes with several other changes. Those include greater visibility and control over enabling multi-factor authentication (MFA) within the tool as well as the ability to receive real-time email-based alerts for remediating malicious tactics such as those discussed above.
