First-of-Its-Kind Attack Technique Scraped Certificate Data for Certificate Errors Phish
Malicious actors leveraged a new technique for a certificate errors phishing campaign in which they scraped real certificate data and included it in their attack email.
Inside the Fake Certificate Error
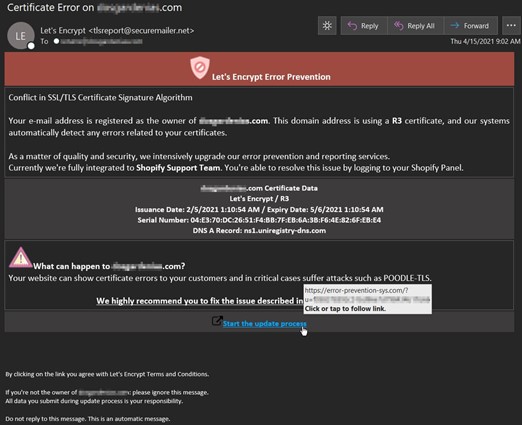
In the middle of April, the Zix | AppRiver team detected an email that masqueraded as a “Let’s Encrypt Error Prevention” message.
The email arrived with a personalized subject line that included the name of a domain owned by the recipient. It then informed the recipient that Let’s Encrypt had automatically detected an issue with their R3 digital certificate, noting that there was specifically a “conflict in SSL/TLS certificate signature algorithm.”
To add a sense of legitimacy to its claim, the attack email pulled real certificate data and the DNS A-record to tailor the phishing message to the recipient’s domain.
Troy Gill, manager of security research at AppRiver, explained that this social engineering tactic isn’t something he sees every day.
“It is not often we see an attack technique we would classify as a ‘first,’” he explained. “That said, we predicted we would see attackers further personalizing and customizing their attacks this year, and this phishing attack fits the bill. We don’t recall ever seeing the cert info being leveraged like this.”
From there, the attack email warned the recipient that their website could “suffer attacks such as POODLE-TLS” (more information on the POODLE attack here) unless they clicked on a hyperlink reading “Start the update process.”
The recipient’s compliance initiated the final stage of the phishing attack—stealing the recipient’s login information for their domain.
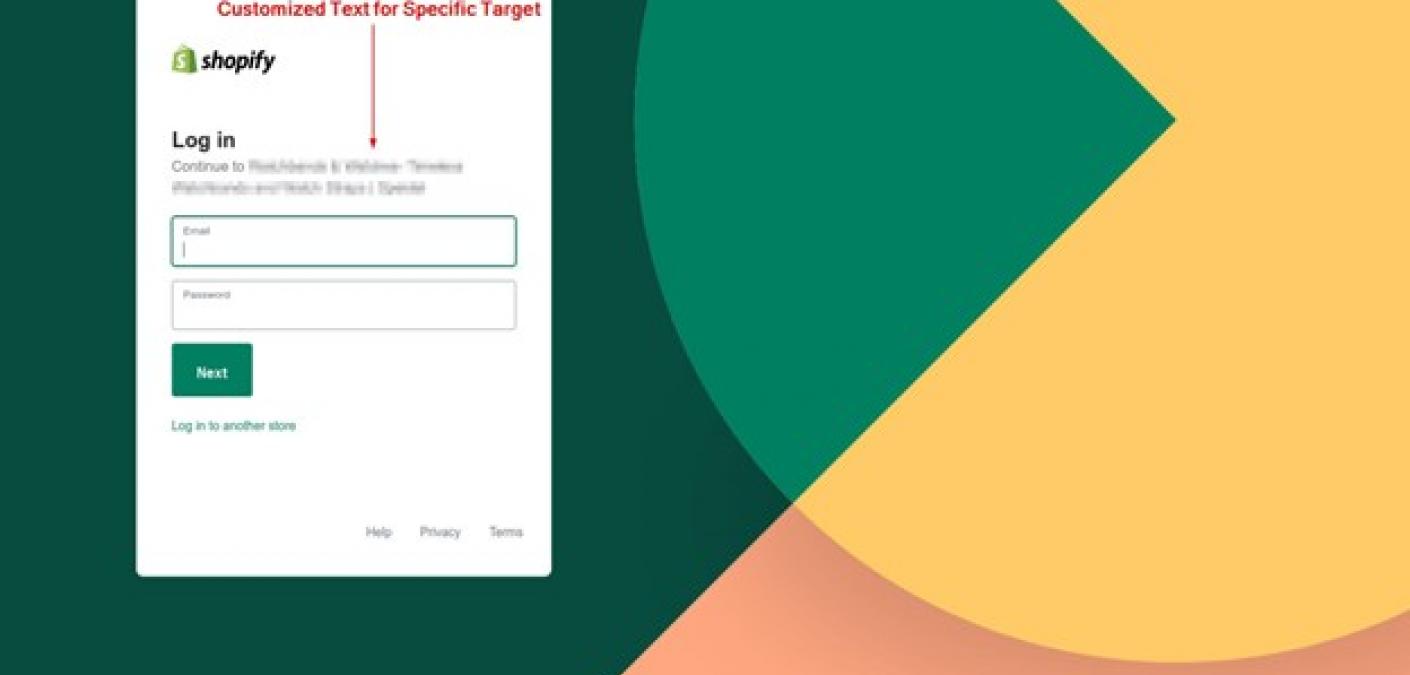
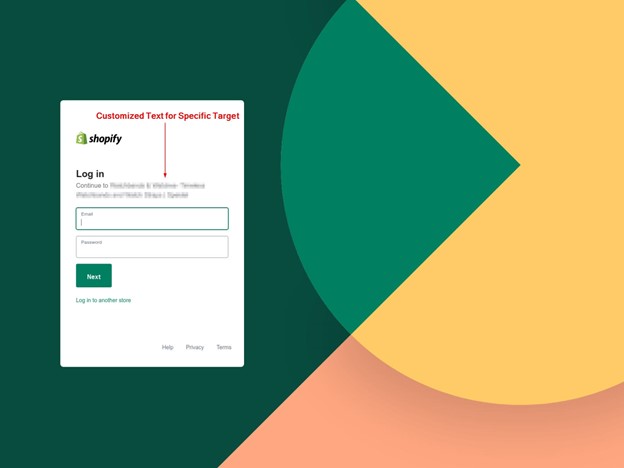
“The payload URL led to a credential harvesting site located at https://error-prevention-sys[dot]com/?u= (some generated code),” noted Gill. “It’s customized for the recipient’s specific web platform admin page. While testing, we observed the generic WordPress admin login page and Shopify login pages (depending on the target).”
Putting This Attack and the Sender Email Address into Context
Those responsible for this attack used spoofing techniques to make it appear as though it had originated from Let’s Encrypt. In reality, it had come from tlsreport@securemailer[dot]net.
A Google search for “securemailer[dot]net” came up with an automated email management service operated by an organization called “The Sigma Two Group.”
At the time of writing, this website contained a dialog box that claimed to help visitors check the availability of a domain name of their choosing.
![A screenshot of the securemailer[dot]net.](/sites/default/files/2021-05/securemailer_scrapecert.png)
As shown in the image above, the website coincidentally lacked HTTPS protection.
This author tried numerous searches of claimed and unclaimed website names using the dialog box. Each search yielded the same result: an error message reading “not found.”
![A screenshot of the “not found” result yielded by securemailer[dot]net.](/sites/default/files/2021-05/notfound_scrapecert.png)
Since Zix | AppRiver first spotted this scam, users shared on the Let’s Encrypt community pages that they had received similar versions of the ruse. It’s possible that whoever launched this attack gathered all of these domain owners’ information using whois data or information that was publicly available on the targeted websites themselves.
How to Defend Against This Scam
The attack described above highlights the need for organizations to defend themselves against malicious actors and their constantly evolving phishing techniques. One of the ways they can do this is by investing in an email security solution that can scan incoming email messages for malware signatures, suspicious IP addresses, campaign patterns and other threat indicators. This solution should perform this analysis in real time in order to allow legitimate business correspondence to reach their intended destination.
Overcome phishers’ new tricks using the email threat protection tools from Zix | AppRiver.
