Phishing Attack Packs Executable File with Bingo Game to Distribute AgentTesla

A phishing campaign packed an executable file together with a bingo game to distribute AgentTesla as its final malware payload.
Malware Was Its Name-O!
In the middle of July, the Zix | AppRiver team came across an attack email disguised as a Request for Payment.
The email appeared to come from an email address associated with AVIC Jonhon OptronicTechnology Co., Ltd.
Affiliated with the Aviation Industry Corporation of China, Ltd., Jonhon produces electronic connectors for use in high-end manufacturing fields including defense, commercial aerospace, telecommunication, healthcare, rail transit, and petroleum.
A Google search revealed no matches with the username included in the attack email’s sender address. It’s therefore possible that whoever sent out this phish leveraged spoofing techniques to disguise their email address.
As shown in the screenshot below, the attack email was far from verbose. It simply requested that the recipient clear an overdue payment by opening an attached document.

Here’s where the attack email really gave itself away as suspicious. Unlike legitimate Requests for Payment, its attachment did not come in the form of a PDF document or an Excel spreadsheet. It arrived as a .XZ file bearing the name “June SOA.exe.xz.”
A relatively uncommon file extension, .XZ functions much like .ZIP in that they store files that have been compressed. This makes storing and sharing large numbers of files easier than interacting with them on an individual basis.
A Packed Malware Payload
Given the file name of the attachment, it’s not surprising that the .XZ archive contained an executable file containing malware. This campaign’s executable was different than other operations’ files, however, as it came packed with a bingo game.
A screenshot of the executable file reveals functions associated with retrieving a bingo board, starting a new game, and prompting a player to enter their name, for instance. It also included some mention of a “Bingo_Engine.”
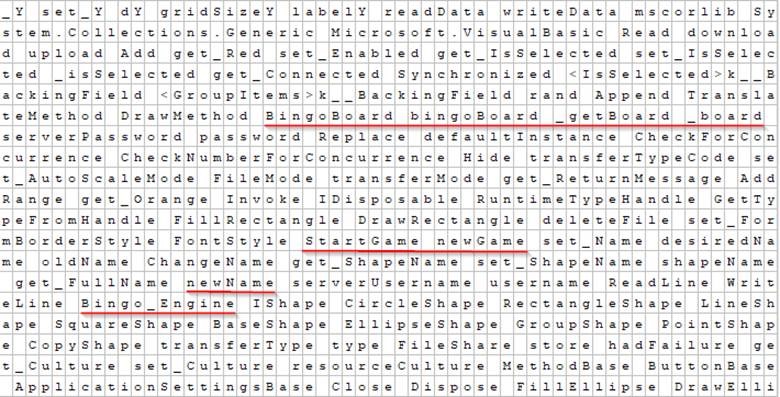
Those elements helped the campaign to infect the recipient with AgentTesla without making too much noise. This remote access trojan has made headlines in the past through its ease of deployment, its price point advertised on digital crime forums, and its ongoing updates.
Not the First Packed Executable File
The campaign described above wasn’t the first time the Zix | AppRiver team spotted an executable file that came packed with something else to evade detection.
Back in April 2021, for instance, researchers at the security firm spotted an attack email that asked the recipient to confirm some payment instructions. Opening the attachment revealed an executable file that included references to “TRexUI,” Google Chrome’s offline dinosaur game. This tactic helped that attack email evade detection so that it could distribute Snake, a threat which can steal a victim’s sensitive information and logging their keystrokes.
Defending Against Evasive Email Attacks
The attack examples involving Snake and AgentTesla highlight how malicious actors are constantly innovating new techniques that help them to conceal their malicious activity and to improve the success rate of their email campaigns. They also underscore the fact that organizations can’t defend themselves against such attack attempts using traditional email security software. They need a sophisticated solution that analyzes incoming email messages for malware signatures, IP addresses, campaign patterns, and other threat indicators. This tool should perform its analysis in real time so that there’s no delay in legitimate business correspondence reaching its intended destination.
Gain visibility over email-borne executable files using Zix | AppRiver.
