Blog
 Fake Moneycorp Confirmation Email Used to Distribute AveMaria Infostealer
Fake Moneycorp Confirmation Email Used to Distribute AveMaria Infostealer
Digital attackers used a fake confirmation email from foreign exchange and international service Moneycorp to infect recipients with the AveMaria infostealer.
Read more Why the Colonial Pipeline Attack Was Such a Big Deal
Why the Colonial Pipeline Attack Was Such a Big Deal
Two months after the Colonial Pipeline attack we’re still discovering what the full legacy of the ransomware attack may look like. Here is what we know so far.
Read more Fake Complaint Letter from American Spirts Company Leads to JSSLoader
Fake Complaint Letter from American Spirts Company Leads to JSSLoader
Read about how digital attackers used a fake letter of complaint from an American-owned spirits company to target recipients with JSSLoader malware.
Read more Fix your sales-service handoff to enhance the customer experience
Fix your sales-service handoff to enhance the customer experience
Today’s MSPs use automation to streamline services in a number of ways, but there are valuable parts of the sales cycle where a human element is needed instead.
Read more Biden Executive Order Takes Aims at Software Supply Chain, Federal Cybersecurity
Biden Executive Order Takes Aims at Software Supply Chain, Federal Cybersecurity
Biden Administration responds to recent cybersecurity attacks requiring federal agencies adopt zero-trust architecture and uphold security best practices such as encryption and MFA.
Read more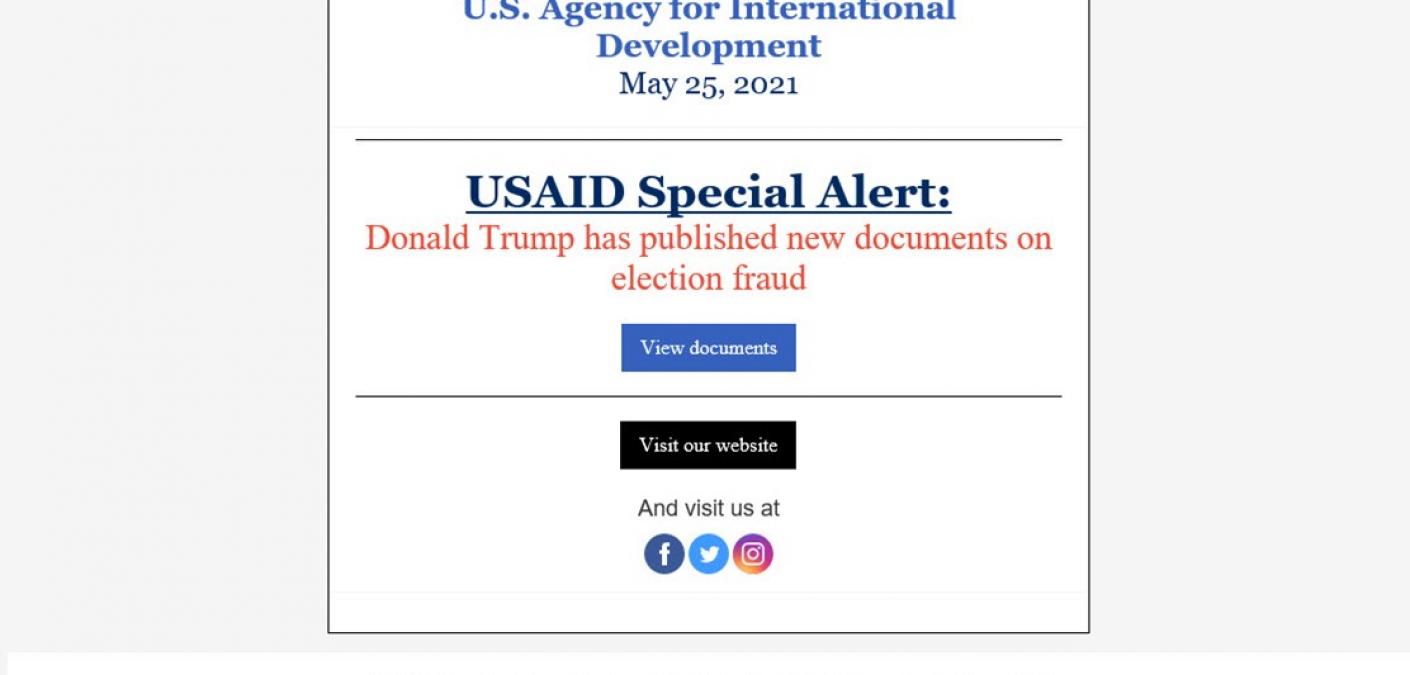 The SolarWinds Threat Actor Returns with a New Phishing Campaign
The SolarWinds Threat Actor Returns with a New Phishing Campaign
The threat actor responsible for the SolarWinds supply chain attack is making headlines once again with a new email phishing operation.
Read more 3 Lessons A Healthcare IT Director Wishes He Knew (Before He Got Hacked)
3 Lessons A Healthcare IT Director Wishes He Knew (Before He Got Hacked)
When hackers found their way into a healthcare organization's network, the IT director had to do ransomware damage control. Read what he learned in this blog.
Read more Fake Security Awareness Emails Lead to Theft of Cryptocurrency Owners’ QR Pairing Codes
Fake Security Awareness Emails Lead to Theft of Cryptocurrency Owners’ QR Pairing Codes
Digital attackers are using security awareness as a theme in their attack emails to steal cryptocurrency owners’ QR pairing codes.
Read more How to Harness Your Employees to Collect Valuable Customer Data
How to Harness Your Employees to Collect Valuable Customer Data
Collecting MSP customer info is important for retention and account opportunity. Learn how to fix PSA data practices and harness your employees to record it.
Read more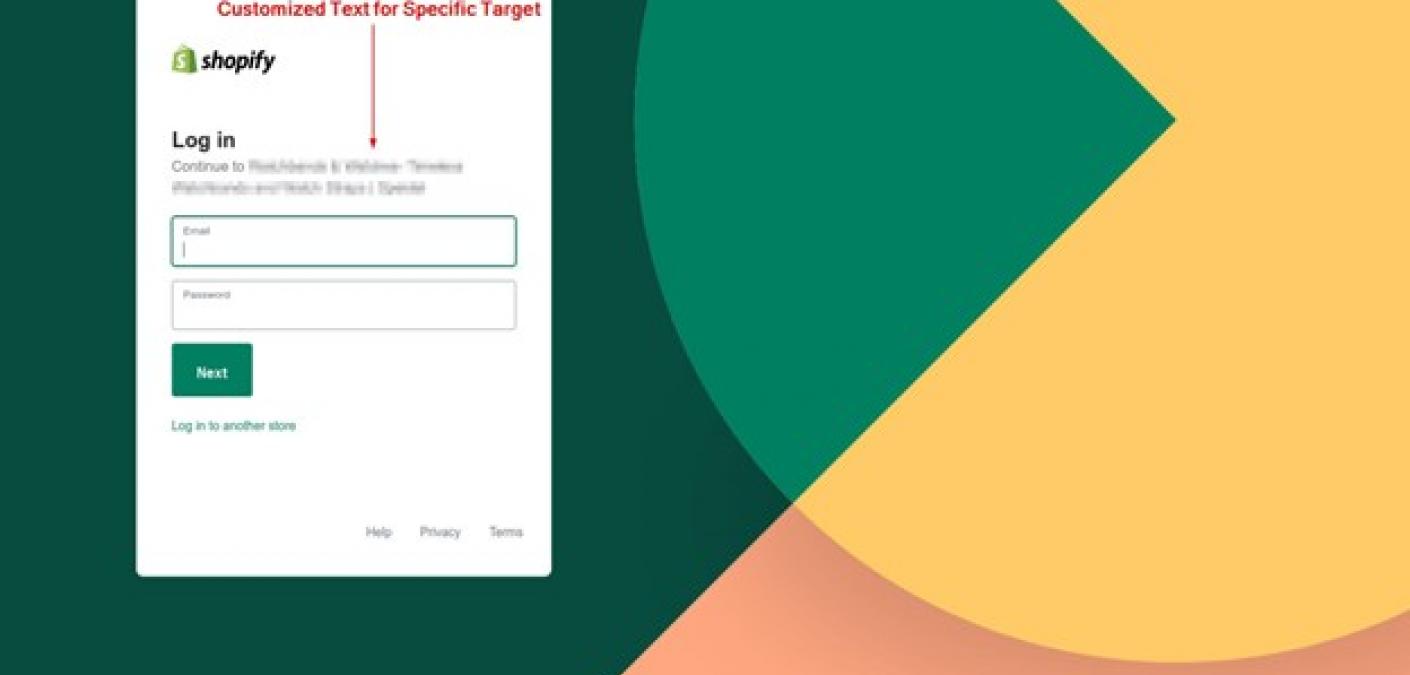 First-of-Its-Kind Attack Technique Scraped Certificate Data for Certificate Errors Phish
First-of-Its-Kind Attack Technique Scraped Certificate Data for Certificate Errors Phish
Malicious actors leveraged a new technique for a certificate errors phishing campaign in which they scraped real certificate data and included it in their attack email.
Read more Colonial Pipeline Disrupted by Now-Defunct DarkSide Operation
Colonial Pipeline Disrupted by Now-Defunct DarkSide Operation
The Colonial Pipeline Company fell victim to DarkSide, a ransomware operation which closed shop after its attack made international headlines and attracted the attention of the FBI.
Read more Email and Communications Archiving: Best Practices 101
Email and Communications Archiving: Best Practices 101
Co-Author: Madison Arcemont
Read more



