Fake Security Awareness Emails Lead to Theft of Cryptocurrency Owners’ QR Pairing Codes

Setting the Scene
The team at Zix | AppRiver detected this attack in the beginning of May—a period when many cryptocurrency markets were having a bit of a roller coaster ride.
Take bitcoin, for instance. According to CoinDesk, bitcoin’s value exceeded $58,000 on May 1. That was after a $15,000 plunge from over $63,000 in mid-April to about $48,000 by the end of the month. Bitcoin’s value continued to drop after May Day, reaching $31,000 on May 23.
It’s therefore not surprising that Zix | AppRiver spotted the attack when it did. It wasn’t a coincidence. It was just one of many crypto-themed operations to show up on the team’s radar.
“Over the past couple weeks, digital currency prices have dipped and ripped,” explained Troy Gill, manager of security research at AppRiver. “Likewise, threat actors have ‘let rip’ a variety of scams attempting to benefit from the crypto frenzy.”
Awareness Is the First Step…in This Attack
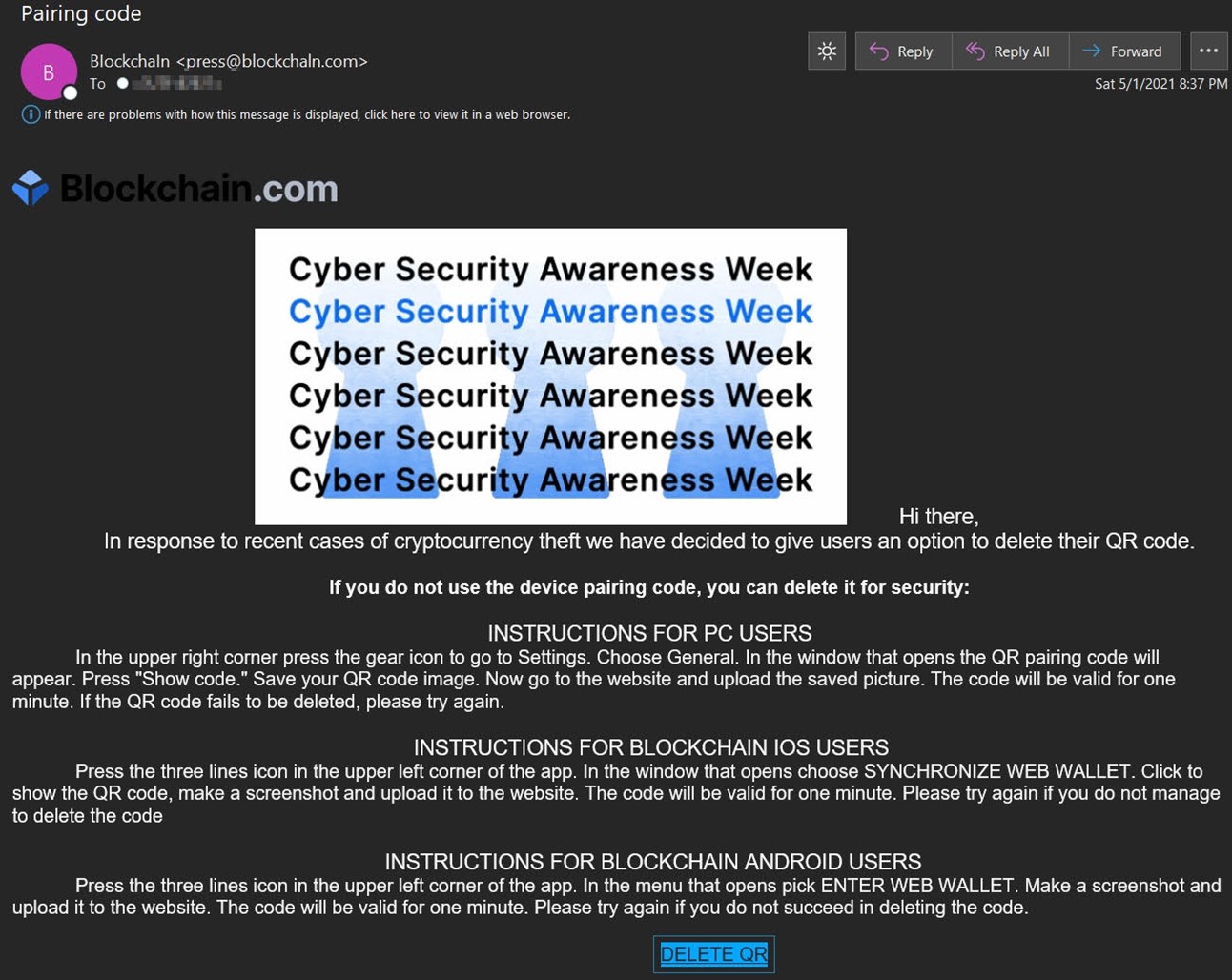
At face value, the email appeared to originate from crypto finance house Blockchain. It arrived with the subject line “Pairing code,” and it used the theme of a “Cyber Security Awareness Week” to inform users that they could delete their QR pairing codes.
The email went on to provide detailed instructions of how users could delete their QR pairing codes with the PC, Android or iOS version of their wallet.
Per CryptoCurrency Facts, QR codes help cryptocurrency owners conveniently share their wallet addresses when they want to exchange digital funds. This often involves the recipient displaying the QR code of their wallet address and the sender scanning that QR code with a wallet app.
A Few Red Flags to Consider
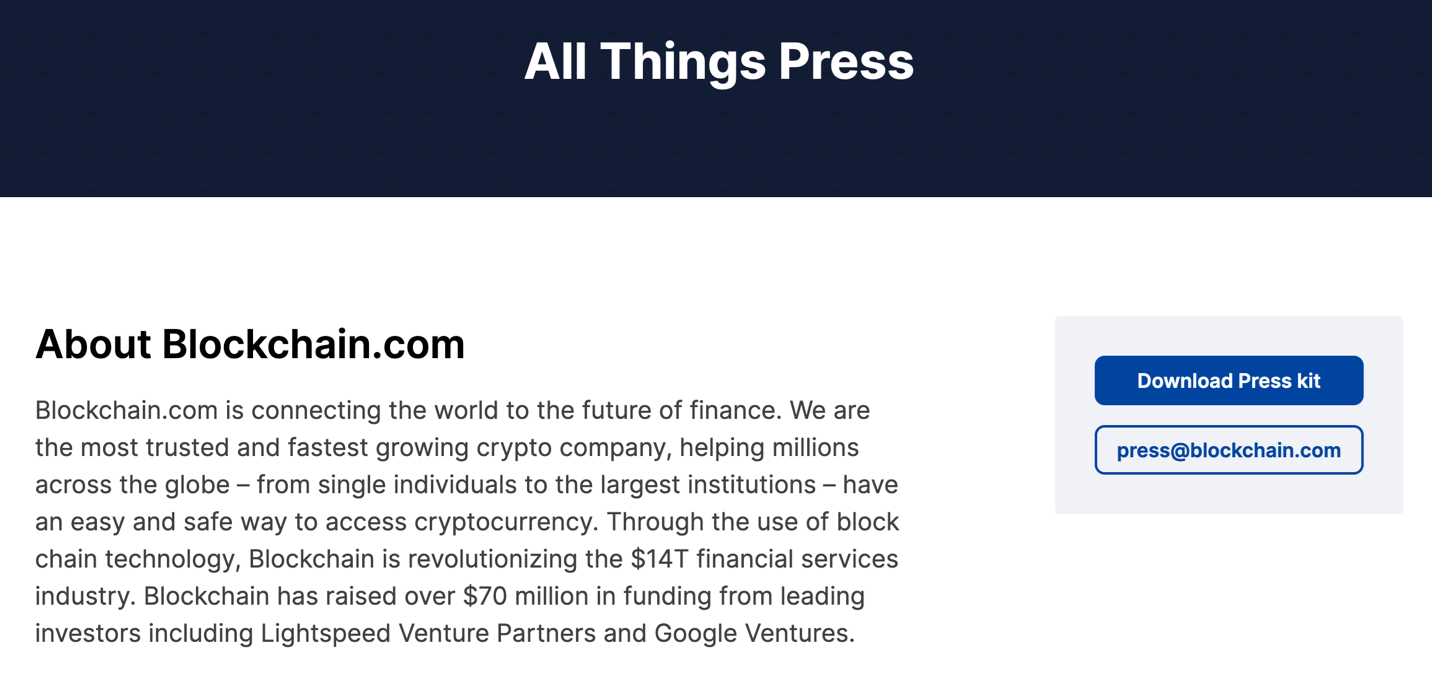
At first glance, the sender address for the attack email looked like it was “press@blockchain.com.” That’s a legitimate email address used by the crypto finance house to process media inquiries, as seen in the screenshot below.
But there’s something amiss with the sender email address. A closer look reveals that the sender domain was one character off from the legitimate Blockchain domain. This made the actual sender domain “blockchaln[dot]com.”
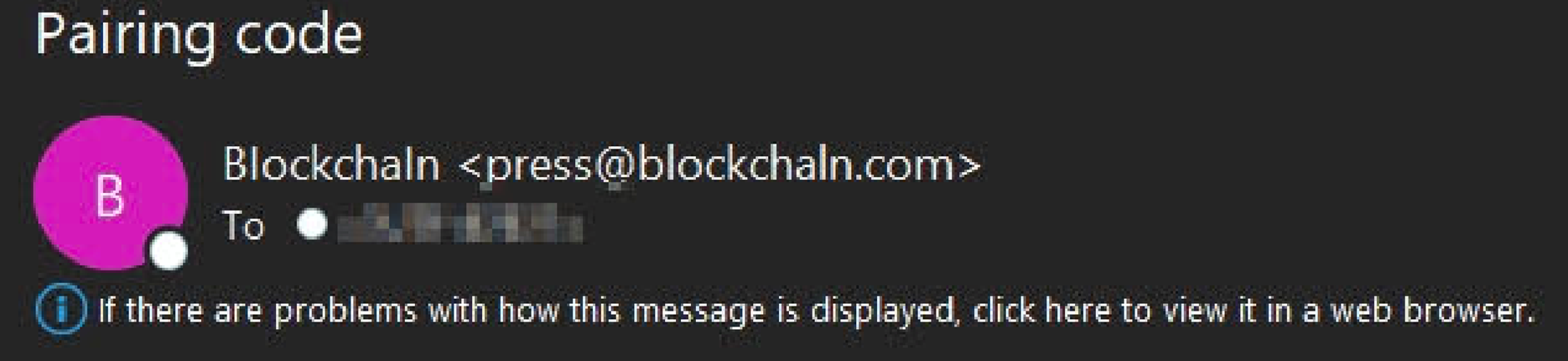
The trick discussed above is an example of typosquatting. This technique allows malicious actors to prey upon unsuspecting users by registering domains that closely resemble legitimate websites like blockchain.com. It’s a tactic that’s appeared in many digital attacks in recent years including an attempt to target victims of the 2017 Equifax data breach.
Not surprisingly, malicious actors have used “blockchaln” in other attacks targeting cryptocurrency owners. Users took to Reddit to warn of a SMS phishing campaign involving this suspicious domain back in December 2014, for example.
The sender domain wasn’t the only issue in this attack. So too was the promotion of a “Cyber Security Awareness Week.” Indeed, there’s no record of Blockchain.com sponsoring this type of education campaign in April or May of 2021. (The crypto finance house did host a “Crypto Security Awareness Week” a couple of months earlier in February, however. It also held some events for National Cyber Security Awareness Month in October)
The End Goal of this Email Attack
Notwithstanding the helpful “advice” already provided in the body of their message, the attackers included an embedded “DELETE QR” button in their email. It’s this feature that ultimately advanced the attack to its crypto-slurping end.
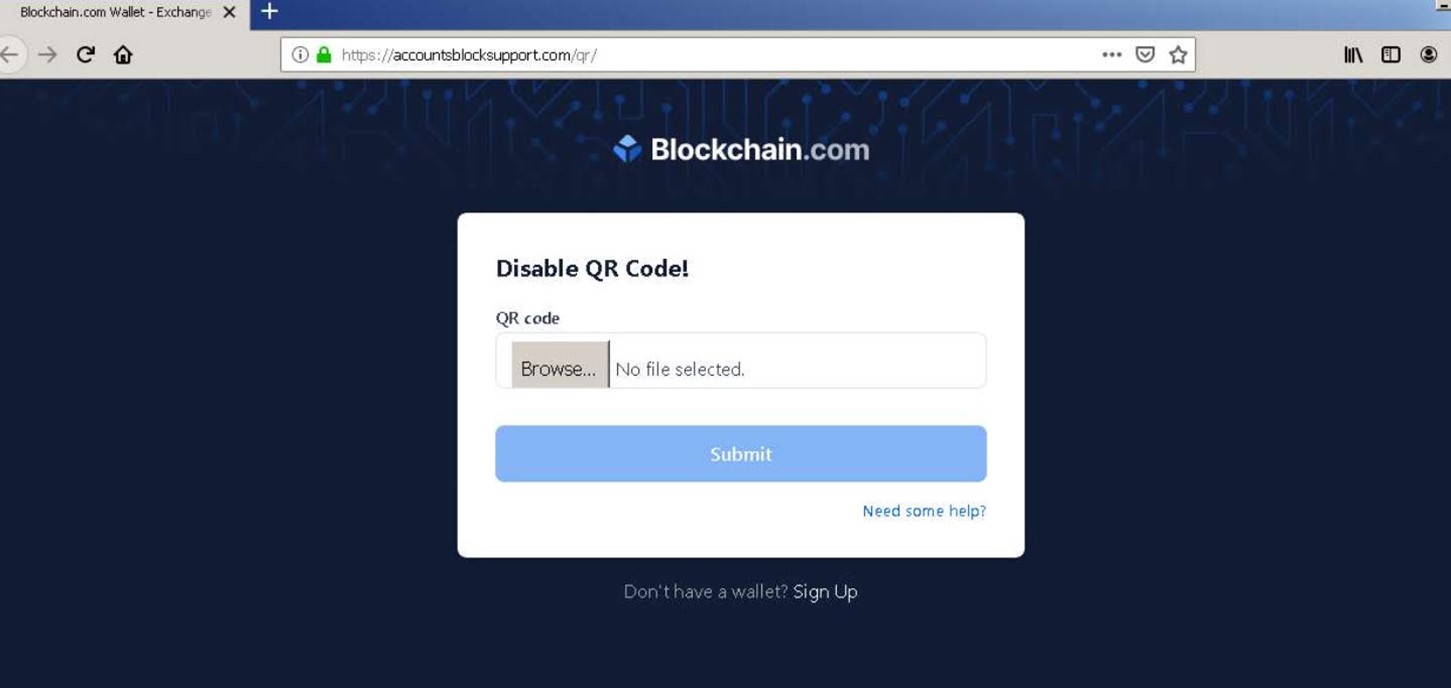
“If the recipient clicks on the “Delete QR” option, they would be sent to a site that asks the user to upload their QR code,” noted Gill. “Doing so would grant the attacker full access to the associated wallet and the funds contained within.”
Clearly, cryptocurrency owners need to protect themselves against the attack email described above and others like it. They can do so by investing in an email threat protection solution. This tool should scan incoming email messages for suspicious indicators in real time, all while allowing legitimate correspondence to reach their intended destination.
