Text of Kenosha Protests Article Used for Word Stuffing in TrickBot Attachment

Digital attackers used the text of an article covering the protests in Kenosha, Wisconsin for word stuffing in a TrickBot malware payload.
A Malicious Attachment with Timely Text
Zix | AppRiver spotted the attack campaign at the end of August 2020. Using the subject line “Invoice you asked,” the attack emails claimed to be sending over an invoice that the recipients had requested. Those emails arrived with an attachment called “Invoice895.doc.” When opened, this file delivered a sample of TrickBot.

This malware has gotten up to all kinds of trouble over the past few years. Malicious actors have incorporated it into email attacks that have spoofed data and analytics companies, well-known banks and non-ministerial departments of the UK Government. Those responsible for TrickBot have also partnered with other threat groups such as Emotet in an effort to target users with Ryuk ransomware, among other threats.
What made this particular attack stand out wasn’t its lure or a new malware partnership. It was what Zix | AppRiver found in the attachment itself. More precisely, it was text from a CNN article on the 2020 protests in Kenosha, Wisconsin.
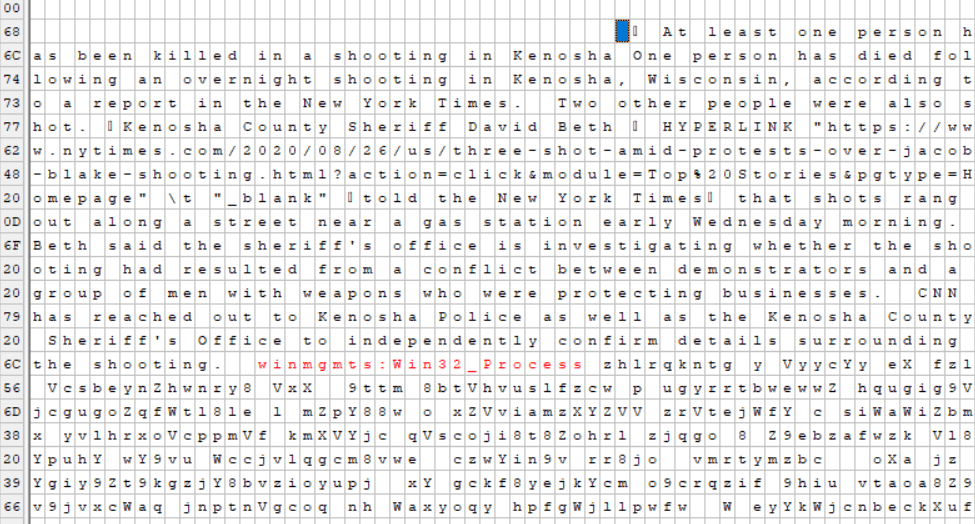
A close look by Zix | AppRiver revealed that those responsible for the campaign had inserted this text into their payload attachment using a technique known as “word stuffing.” The attackers figured that they could mislead email filters and (more likely) machine learning classifiers looking for malicious content. Because they came across legitimate text from a news article, the attackers reasoned, those tools would allow the attack to proceed unimpeded. The email didn’t fool Zix | AppRiver, however. Its solutions flagged the email as malicious.
Relevance: The Impetus behind Creating New Attacks
The campaign described above represents just the latest instance in which malicious actors have used the news for the purpose of creating their attacks. Plenty of other operations also stand out from recent years:
- In the aftermath of Hurricane Harvey in 2017, Zix | AppRiver detected several scam attempts that attempted to trick people into donating to fake charitable organizations. Some of those attempts also attempted to collect personal information from the recipient before moving forward with their ruse.
- Malicious actors got to work after Hurricane Dorian in late summer 2019. In one of the scams spotted by Zix | AppRiver, malicious actors said that they were a South Carolina family who lost their house, belongings and pets in the storm. They then asked that recipients send over payment via various methods including a Zelle account using a Georgia area code and a wire transfer to a Wells Fargo branch based in San Francisco. (The attack email itself had originated from Poland.)
- Following the outbreak of coronavirus 2019 (COVID-19) in the spring of 2020, Zix | AppRiver came across a phishing email that masqueraded as a notification from the U.S. Centers for Disease Control and Prevention (CDC). The email claimed that there were new cases of COVID-19 in the recipient’s area. It then instructed the recipient to visit a website where they could supposedly learn about those cases. In actuality, the website was a phishing landing page designed to steal the recipient’s Office 365 credentials.
- With most employees mandated to work from home after the COVID-19 outbreak, it was only a matter of time until Zix | AppRiver observed an attack email that claimed to come from from a recipient’s IT department. The email claimed that IT personnel were working to create a staff portal to help employees keep track of their assignments. If they complied with the email’s instructions and agreed to click on a supposed link to the “portal,” the recipient found themselves redirected to an OWA phishing page.
Strengthening Your Organization’s Email Security
All of the attacks discussed above highlight the need for organizations to strengthen their email security. They can do this by investing in an email solution that can analyze incoming email correspondence for known malware signatures and other indicators of threat behavior. This solution should work in real time while allowing legitimate messages to reach their destination.
Learn how Zix | AppRiver’s email threat protection tool can help keep your organization safe.
