Fraudsters Mark Start of Fall Season with COVID-19 Themed DHL Scam

Digital fraudsters marked the beginning of the fall season by sending out a coronavirus 2019 (COVID-19) themed DHL shipping ruse.
A COVID-19 Themed DHL Scam
Near the end of August, the Zix | AppRiver team came across a scam email that used global logistics company DHL as a lure.
The email claimed that a package had arrived for the recipient at a local DHL office. The mail dispatcher had attempted to find the recipient’s address, the email explained, but they were unsuccessful as the result of COVID-19 restrictions. In response, the dispatcher brought the package back to the local DHL branch.
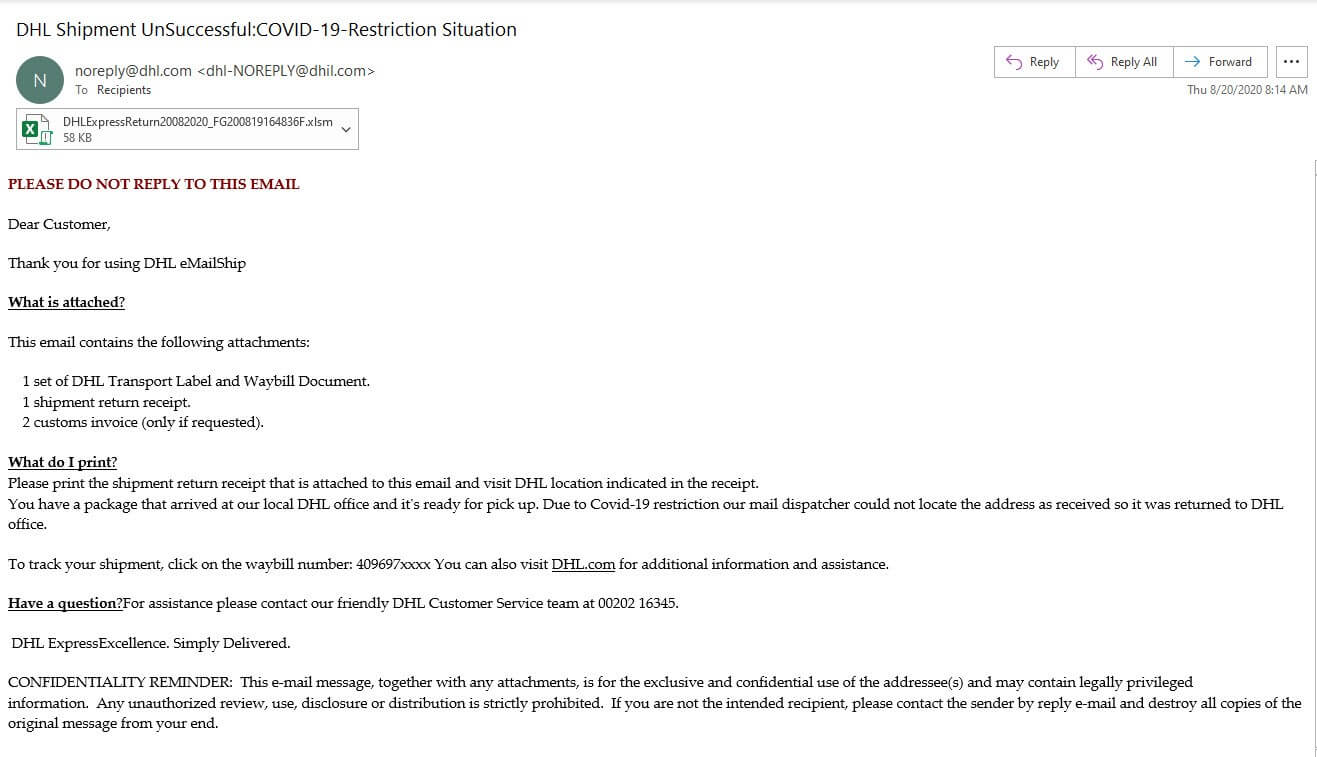
Those responsible for this campaign attempted to add legitimacy to their attack email by spoofing its sender address. The message claimed to have originated from “noreply@dhl[dot]com.” But a closer look revealed that the email had actually come from the suspicious lookalike address “dhl-NORELY@dhil[dot]com.” At the time of writing, a Google search found that “dhil[dot]com” was available for purchase.
The email didn’t stop there in its efforts to appear official, either. Near the end of its body content, it included DHL’s actual slogan “Excellence. Simply Delivered.” It also informed the recipient that they could call the DHL Customer Service team with any questions at “00202 16345.” A search online revealed that phone number belonged to a DHL hotline in Egypt.
Ultimately, the message sought to use these tricks to convince the recipient into opening an attached shipment return receipt and to bring it with them to the DHL branch indicated in the receipt. The attachment contained no such paperwork from DHL, however. Instead, it contained malicious macros that prompted the installation of an AZORult payload.
A Look Back at Other AZORult Campaigns and DHL Scams
This wasn’t the first time that the Zix | AppRiver team spotted AZORult in the wild. At the start of 2020, for instance, AppRiver Senior Cybersecurity Analyst David Pickett discovered a malware campaign that began with a simple attack email. That email arrived with a PowerPoint attachment containing a heavily obfuscated visual basic script. In turn, the script led to a PowerShell command that included a reference to Drake's "Keke Do You Love Me" lyrics.
In addition to previously stopping a number of AZORult campaigns, this also isn’t the only time that DHL-themed scam emails have been blocked by the Zix | AppRiver email threat platform. As an example, security researchers observed the Dridex malware gang impersonating DHL, UPS and FedEx in an attempt to deliver malicious .XLS files to users. The campaign used an OLE object within the document to distribute the trojan. Just a few months after that, security researchers at Zix | AppRiver came across a DHL-themed attack campaign similar to the AZORult operation discussed above. The email arrived with a .ZIP archive that when clicked dropped a payload for the AgentTesla remote access trojan.
Shoring Up Your Organization’s Defenses in Time for the Holidays
Unfortunately, malware campaigns and email attacks impersonating shipping companies will almost certainly grow more numerous (and more creative) as we approach the holidays. That’s why it’s important for organizations to strengthen their email security posture now. They can do this by investing in a solution that’s capable of analyzing incoming messages for IP addresses, malware signatures and other indicators of known threat behavior. This analysis should occur in real time so that legitimate pieces of correspondence can reach their intended destination.
