Attackers Using PPE Spam Campaigns to Distribute Lokibot, Other Malware

Digital attackers are using malspam campaigns to target organizations that are looking to purchase Personal Protective Equipment (PPE) with Lokibot and other malware.
A PPE Scam from Sandra’s Inbox
Zix | AppRiver spotted two campaigns leveraging the lure of PPE to distribute malicious payloads. In the first malspam operation, an attack email originated from the compromised mailbox of someone named Sandra. This email, which arrived with the subject line “Urgent Order // N95 Masks Test Coronavirus Kit Infrared Thermometer Protective Clothing,” asked the recipient to submit a price for a list of enclosed protective gear. For some reason, the message instructed the recipient to “please attach pictures to the quotation” as well as to name a desired delivery time.
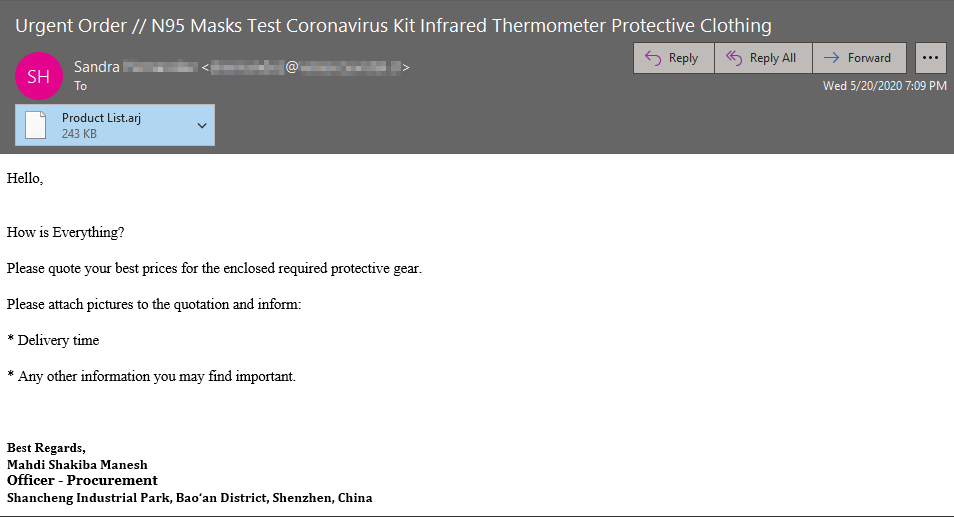
The screenshot above reveals that the malspam sample arrived with the signature of “Mahdi Shakiba Manesh,” an alleged procurement officer working in the Shancheng Industrial Park in the Bao’an District of Shenzhen, China. (A Google search failed to uncover any sign of a Mahdi Shakiba Manesh working in the Shancheng Industrial Park. However, it did show that one Nuoren Technology Co. was in the business of selling PPE in that location.)
Acknowledging all of these findings, it’s no surprise that the attached .ARJ file did not contain a product list. Its compressed files contained an executable named “Product List.exe” for the purpose of launching the operation’s malware payload.
A Face Mask Farce Delivering Lokibot
The second operation spotted by Zix | AppRiver also came from a compromised mailbox. One attack email intercepted by researchers urged recipients to consider purchasing PPE in light of the ongoing pandemic. It asked them to consider buying “the” face mask, whatever that is.
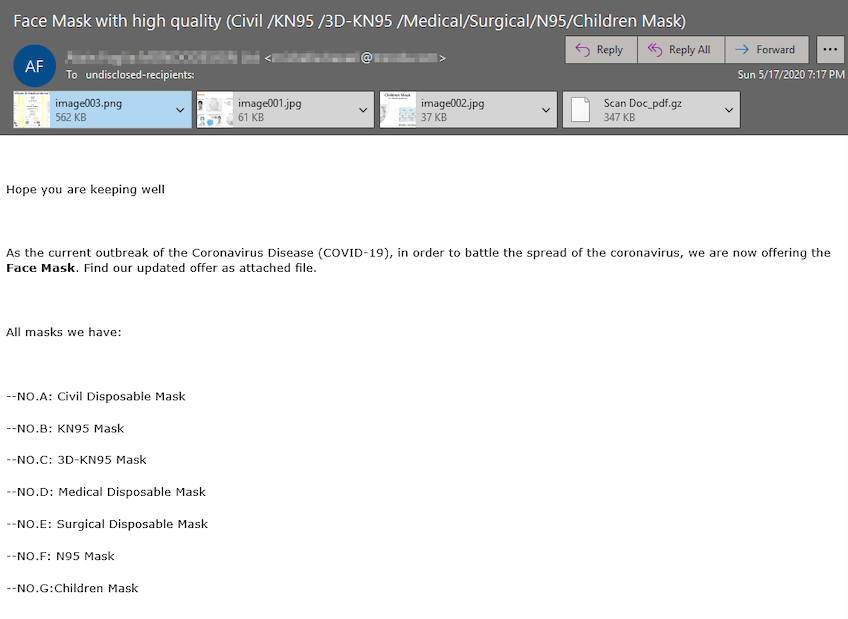
"As the current outbreak of the Coronavirus Disease (COVID-19), in order to battle the spread of the coronavirus, we are now offering the Face Mask. Find our updated offer as attached file."
Despite its wording, the scam email advertised seven different types of masks for sale. Among them were N95 masks, KN95 masks, 3D-KN95 masks and three different types of disposable masks (“civil,” “medical” and “surgical”) that more or less looked exactly the same in one of the campaign’s attached image file. The message also informed the recipient that they could purchase masks designed to be worn by children.
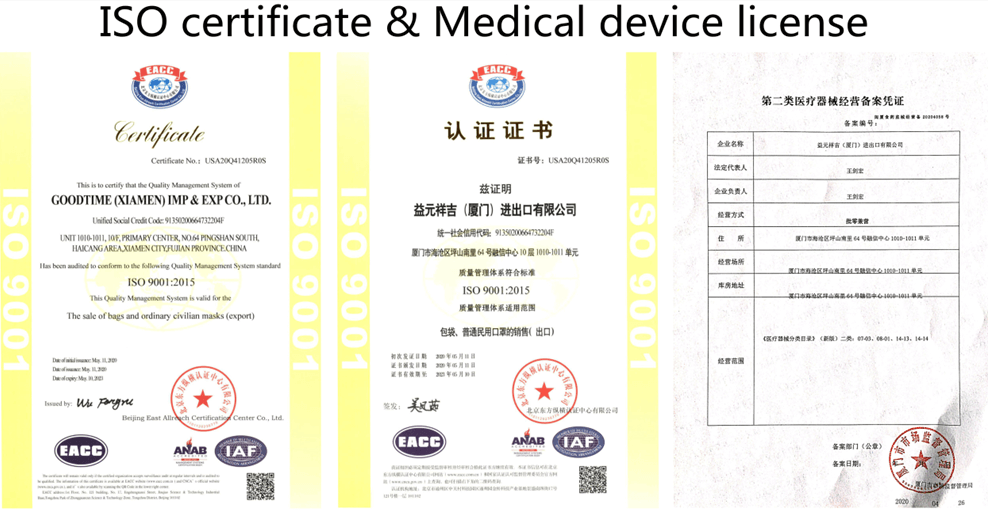
To add a sense of legitimacy to its claims, the email arrived with what appeared to be an ISO 9001:2015 quality management certification as well as a medical devices license for a company called Goodtime (Xiamen) Imp & Exp Co., Ltd.
The attack email instructed the recipient to open what appeared to be a PDF document named “Scan Doc_pdf.gz.” In actuality, the attachment was a gzip file containing “Build_output.exe.” This executable began the Lokibot infection chain.
Defending Against PPE Email Scams
Organizations can protect themselves against email scams claiming to sell personal protective equipment (PPE) by strengthening their email security defenses. First, they should try to ban .ARJ and .GZ attachments outright, as filetypes are almost always malicious. Second, they should consider investing in a solution that’s designed to analyze an incoming email message for malware signatures, URLs and IP addresses for indicators of known attack campaigns. This solution should perform this type of analysis in real-time, all while allowing legitimate pieces of correspondence to reach their intended destinations.
