Weak Digital Criminal OpSec Causes Double Whammy for Phishing Victims
Digital criminals made a blunder in their Operational Security (OpSec) that exposed their phishing victims’ stolen data even further.
Unraveling the Data Exposure Incident
As reported by Bleeping Computer, researchers at two security firms found that the attack email campaign had begun in August.
The operation began when a user received one of several phishing email templates. Each of those emails pretended to be a new Xerox scan notification.
To add a sense of legitimacy to their emails, the malicious actors incorporated the recipient’s first name or the name of the company into the message’s subject line.
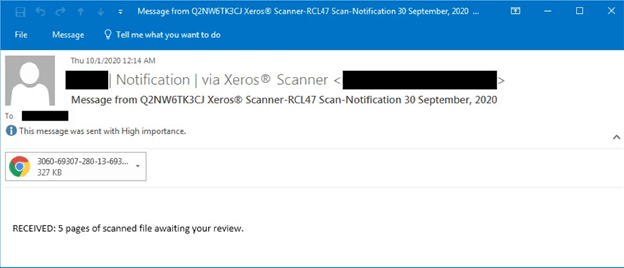
An example of the attack email. (Source: Bleeping Computer)
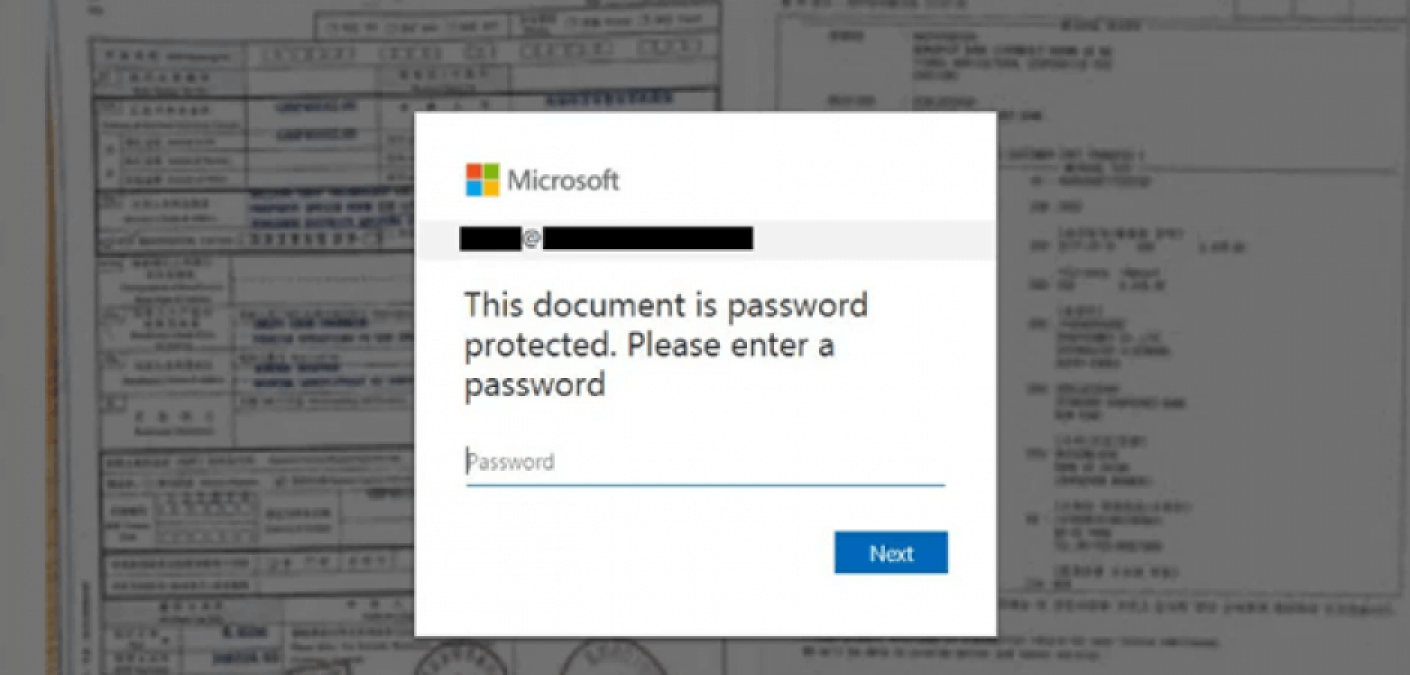
Once opened, the HTML attachment caused the default web browser to display a blurred image of what appeared to be a Xerox scan.
On top of that image sat a personalized dialog box informing the victim that the image was protected with a password. This resource then instructed the victim to submit their password in order to view the image.
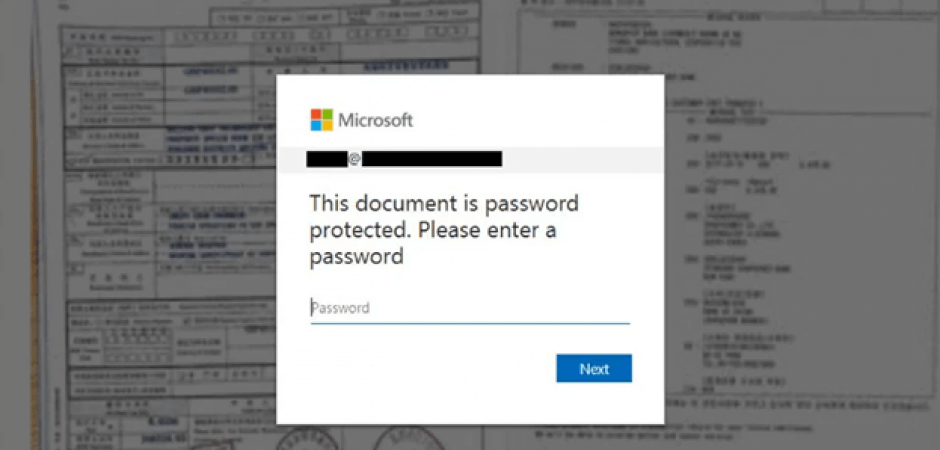
An example of the personalized phishing file. (Source: Bleeping Computer)
The campaign secretly ran JavaScript code to verify the victim’s input for simple passwords, transmit the information to a drop-zone server used by the attackers and ultimately redirect the victim to a legitimate Office 365 login page to minimize a victim’s level of suspicion.
Those responsible for the phishing attacks didn’t use just one drop-zone server. They didn’t even use servers of the same format. Indeed, they registered dozens of .XYZ phishing domains on individual servers and kept them running for two months. They also commonly leveraged compromised WordPress servers with an established reputation to host a malicious PHP page and process victims’ stolen data.
That didn’t stop the digital criminals from messing up when it came time to sending the information to their drop-zone servers, however. Indeed, the campaign saved the collected information in a publicly visible file that Google ended up indexing. This allowed anyone to view the email credentials compromised in the campaign with a simple Google Search. Viewers with malicious intent might have then used the information to conduct follow-up attacks, or they might have attempted to monetize the data on the dark web.
The researchers analyzed a subset of approximately 500 stolen email credentials and found that the campaign had mainly targeted organizations in the energy and construction sectors.
Putting this Phish into Perspective
The reality is that the attack discussed above isn’t an outlier. Zix | AppRiver detects attacks all the time in which malicious actors fail to secure their infrastructure and end up leaking their victims’ information online. Here is a partially redacted screenshot of one recent example where researchers at the security firm came across a file containing users’ email addresses, passwords, IP addresses, county names, cities and regional locations.
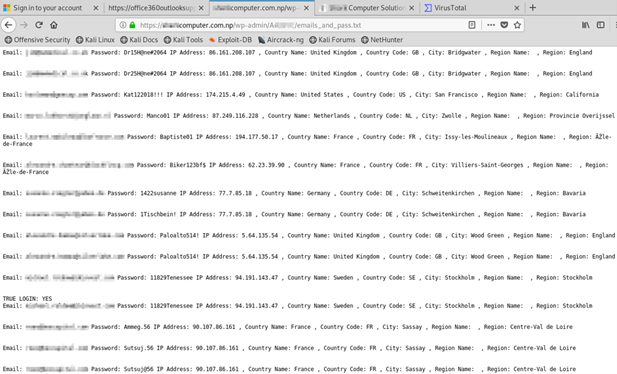
A screenshot of yet another phishing attack gone wrong. (Source: Zix | AppRiver)
This attack underscores how one successful phish can expose victims to numerous instances of data exposure and thereby create an opportunity for follow-up attacks. In acknowledgment of that threat, organizations need to work to prevent a phish from occurring in the first place. They can do this by investing in an email security solution that analyzes incoming messages for malware signatures, campaign patterns and other indicators pertaining to known threat behavior. That tool should perform this type of analysis in real time so that it allows legitimate business correspondence to reach its intended destination.
