Firefox Send Service Being Used to Distribute Banking Trojan
We have been closely monitoring Conversation Hijacking Attacks (CHA) ever since we uncovered the activity back in late 2017. Operated by threat actors actively distributing the Gozi/Ursnif banking trojan the group has been relentless in their efforts to distribute malware through this method and have clearly found some good success with it.
If you are unfamiliar with CHA’s they are quite simple. The attackers send out thousands of phishing attacks with the intent of harvesting users' email credentials. Once they have collected credentials they use a bot to log into the (otherwise) legitimate email accounts and send out malware by ‘replying’ to ongoing conversations, thus the term Conversation Hijacking Attack.
The most common method of infection in these botnet-generated CHA’s has been the inclusion of a malicious word document. These are sometimes encrypted and sometimes not. Throughout the past few years, this group has consistently looked for new and improved ways to raise their efficacy. This past week saw another shift in their attack methods that we found quite interesting.
Attacks Shifted This Week
These malicious actors are now using the Firefox Send service private file sharing service to deliver the payload in the body of the emails. This allows for free file sharing by encrypting the file and providing a custom URL where the file can be retrieved. These URLS are formatted as (https://send.firefox.com/download/*). Abusing the service is a natural evolution given the historical affinity this group has displayed for using encrypted payloads in an attempt to circumvent security solutions.
The URL embedded in these emails leads to an encrypted archive (ZIP) that contains a malicious VBS file. Of course, to open the archive you must use a password which is conveniently located in the body of the message. This is an attempt to circumvent security controls as the URLs base domain the is well known and trusted firefox.com. As a bonus, the encryption of the file being delivered aids the attackers by preventing SOME security solutions automated detection from seeing inside the archive and thus understanding the true nature (malware) of the file being shared. Our customers can rest assured they are protected from this threat.
Example below:
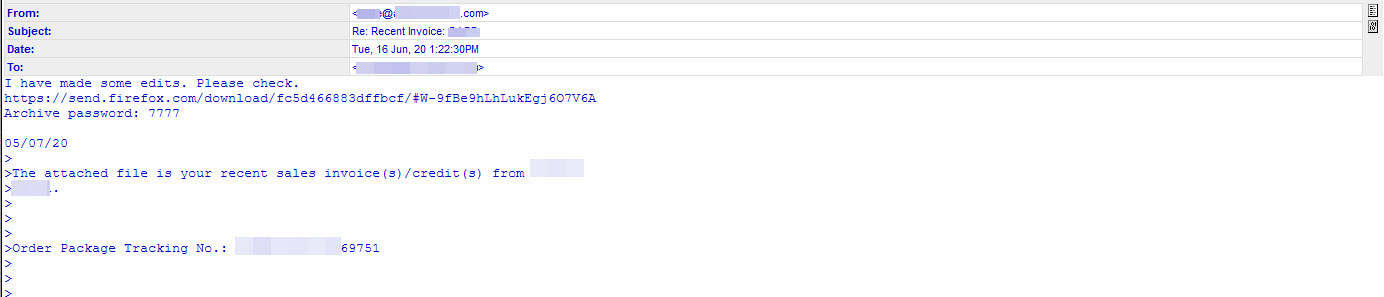
Attackers love to abuse legitimate services and Firefox Send is just one more they have in their bag of tricks. However, we have observed that these links remain active now, even 48 hours after their distribution. In recent months, as attackers look to lend credibility to their attacks, we have also seen a rise in abuse of other services as well including Evernote, Gitbook storage.googleapis.com, onedrive.live.com, appspot, sharepoint.com and FireBaseApp just to name a few.
