Phishers Misusing Feedburner Links to Redirect Users to Phishing Pages
Email attackers are leveraging Feedburner links to redirect recipients to phishing pages.
A Fake Tax Refund Phish
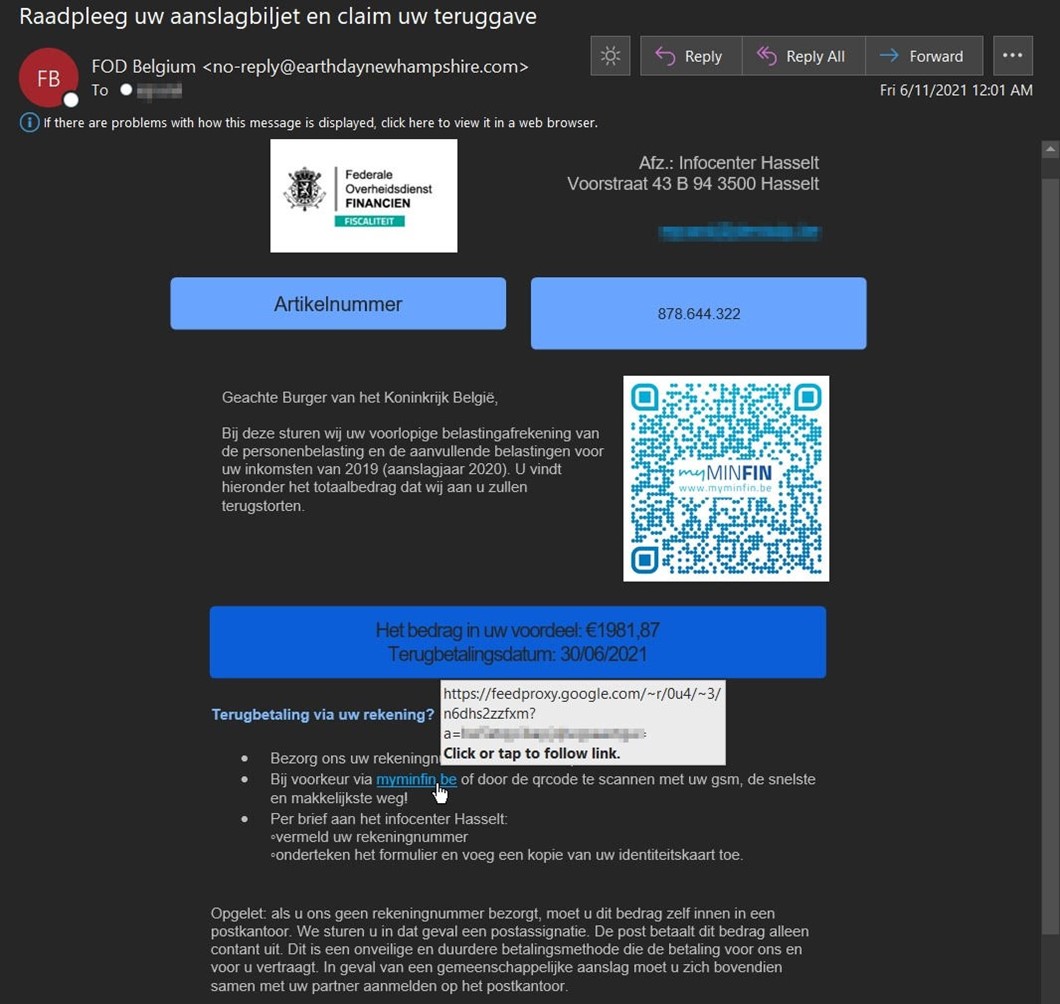
In the beginning of June, the Zix | AppRiver team flagged an email that appeared to come from the Federal Public Service of Finance (FPS Finance) in Belgium.
The sender(s) used stolen branding and spoofing techniques to make their message appear legitimate. That makes sense seeing how they sent their email from “no-reply@earthdaynewhampshire[dot]com,” an email address which at face value has nothing to do with the Belgium government or federal taxation.
Written in Dutch, the email informed the recipient that the FPS Finance had sent over a provisional 2020 tax statement for their business income and for additional taxes that year.
It went on to note that the recipient was entitled to a refund of €1,981.87. All they had to do was log into their account with My Minfin, an application created by the FPS Finance which helps Belgium citizens manage their tax files online, or scan what appeared to be a My Minfin QR code using their mobile phones.
In support of this ruse, the attack email arrived with a hyperlinked “myminfin.be.” But it didn’t direct the user to the legitimate application. Instead, it redirected them to a FeedBurner link.
Launched in 2004 and acquired by Google in 2007, FeedBurner is a service that helps bloggers, podcasters, and others to track who’s subscribing to their blog via RSS. It does this by taking a blog’s RSS feed, giving it a new address, tracking subscribers, and providing analytics.
The link in this attack contained a phishing page designed to steal a visitor’s sensitive personal and financial data.
A Shift in Tactics
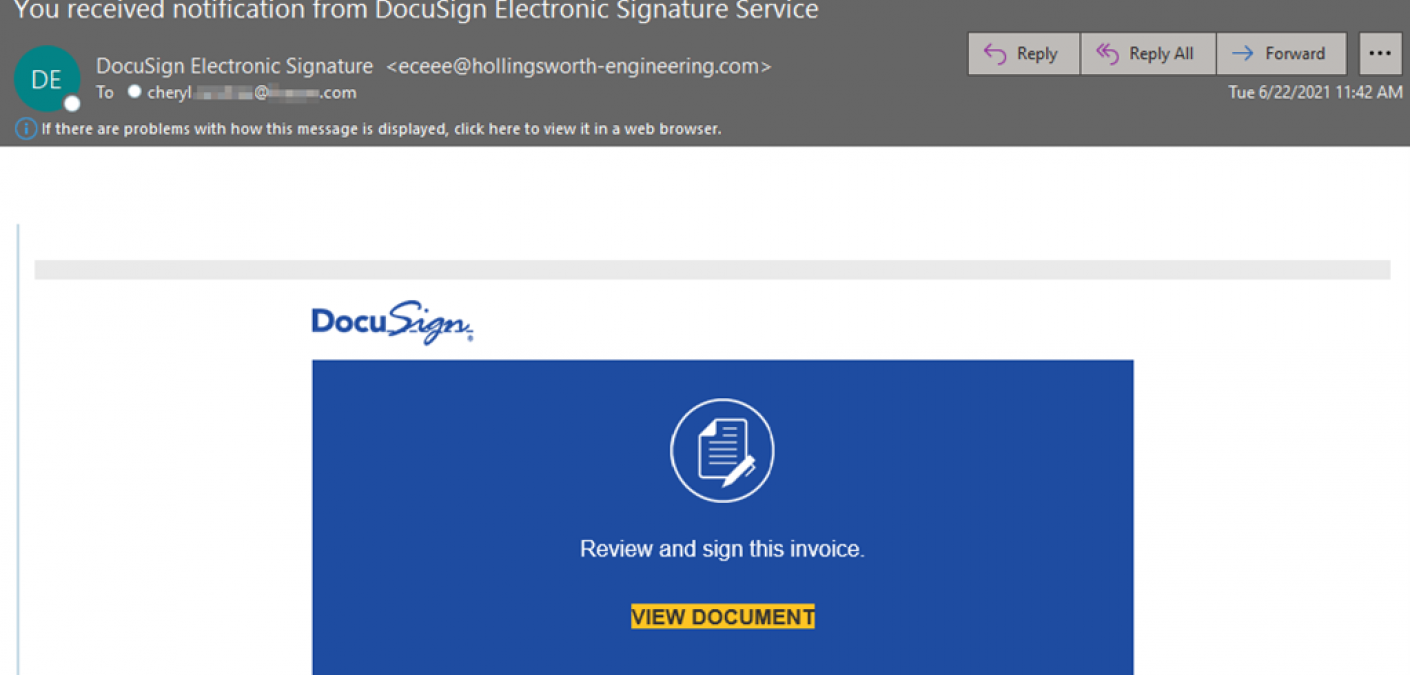
Several weeks later, Zix | AppRiver observed the FeedBurner attacks take on a DocuSign theme.
The researchers came across one such email that arrived with the subject line “You received notification from DocuSign Electronic Signature Service.”
As with the email discussed above, this message used stolen branding and spoofing techniques, only this time, the sender address traced back to the name of a precision engineering company.
The actual body of the email didn’t say much. Its purpose was to trick the recipient into clicking an embedded “View Document” button that similarly redirected them to a phishing landing page.
Putting These Attacks into Context
Misusing FeedBurner constitutes a Living Off the Land (LOtL) tactic in that digital attackers are using Google’s legitimate service to conceal their malicious activity. This helps them to evade detection and to get their attack emails past native email security tools.
Over the past few years, email attacks involving FeedBurner have not made too much noise. But the same can’t be said about campaigns involving some of Google’s other services.
Take Google Docs as an example. Back in the beginning of December 2020, for example, the Zix | AppRiver team discovered a phishing campaign that sent out attack emails from several universities’ .EDU servers. The emails instructed recipients to update their passwords by clicking on an “UPGRADE link.” Doing so redirected them to a file hosted via Google Docs.
Acknowledging these trends, organizations need to take steps to protect themselves against email attacks involving LOtL techniques. One of the ways they can do this is by investing in an email security solution that scans incoming messages for campaign patterns and other threat indicators. This solution should perform its analysis in real time so that legitimate correspondence can reach its intended destination.
Defend against LOtL tactics using email threat protection from Zix | AppRiver.
