BitRAT Distributed by Phishing Emails Disguised as RFQ Notices

Phishers are using Request For Quote (RFQ)-themed emails to infect users with BitRAT.
A 7zip Archive Awaits…
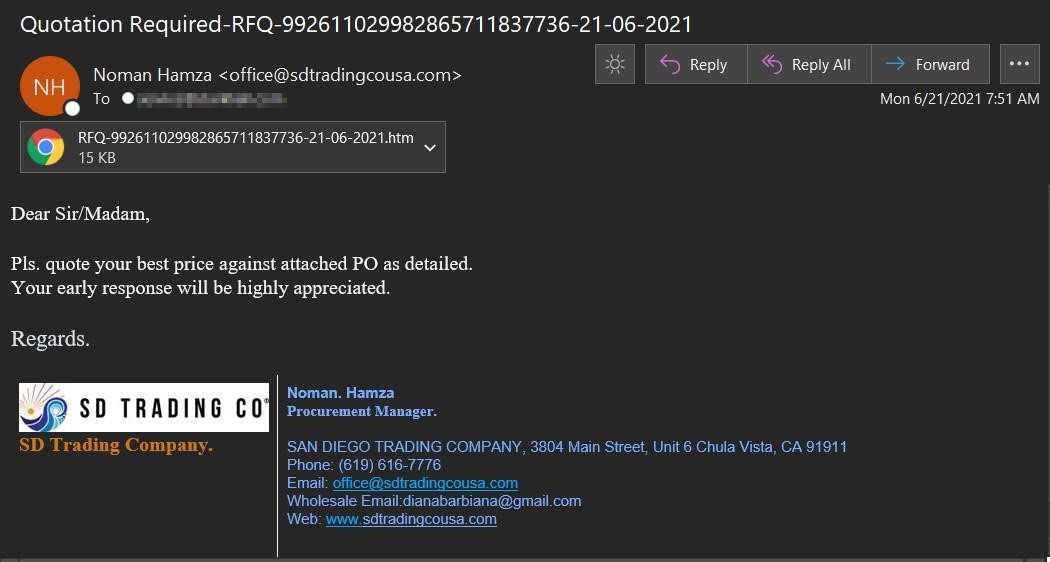
Near the end of June, the Zix | AppRiver team flagged an email that appeared to have originated from a California lifestyle brand company.
The attack email used branding stolen from the company to add a sense of legitimacy. It also used a signature block to create the impression that a procurement manager named Noman Hamza at the company had sent out the RFQ.
Searching “Noman Hamza” in association with the garment company uncovered no results.
Not only that, but the signature block got a few details of the spoofed company’s details wrong. For instance, it listed the company’s phone number as (619) 616-7776, but the organization’s actual phone number is (619) 616-7996.
The signature block also claimed that the message had originated from what appeared to be an official email address at the company.
This email address, which was the same as the sender address, yielded no search results. It’s therefore possible that the digital attackers used spoofing tactics to disguise their email’s origin.
Where the Attack Email Directs a Recipient
The body of the attack email asked the recipient to review an attached purchase order and respond with their best price.
Troy Gill, manager of security research at Zix | AppRiver, explained what happened if someone elected to open the fake RFQ.
“If the recipient opens the .HTM attachment, it opens locally in their default browser, showing a RFQ lure,” he said. “The lure contains a link to an external site hosting a 7zip archive along with a password to decrypt it.”
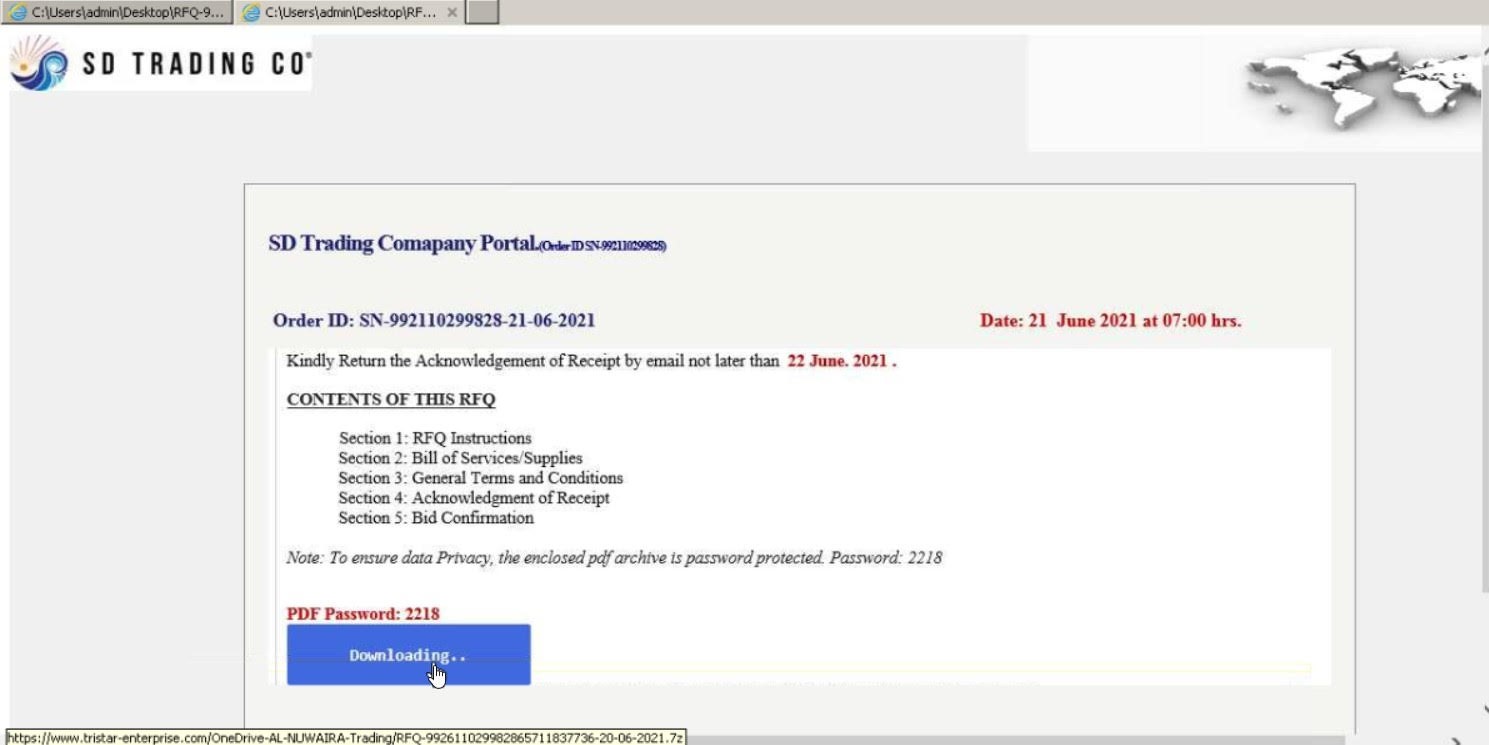
As is evident in the screenshot above, the RFQ lure used stolen branding consistent with the company spoofed in the campaign’s attack email.
Anyone who entered in the password and downloaded the 7zip archive didn’t end up with a purchase order. Instead, they ended up with a BitRAT infection.
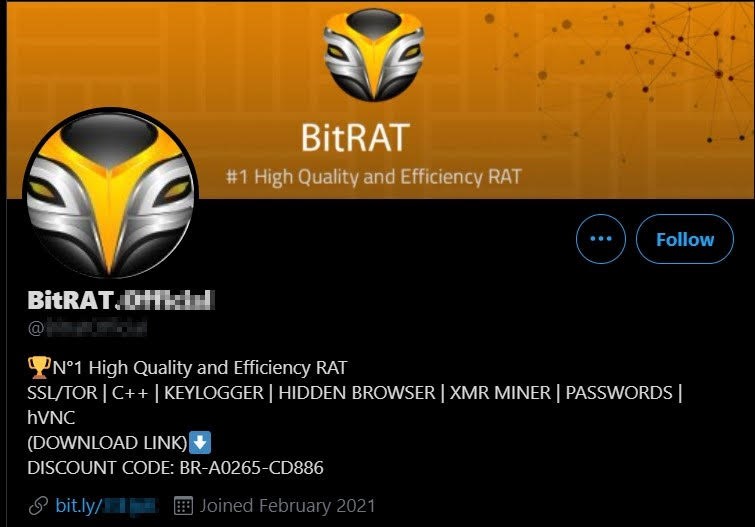
This remote access trojan arrived with the ability to mine Monero on infected devices. To launch their own campaign, all an attacker needed to do was to buy into BitRAT’s Malware-as-a-Service (MaaS) scheme at $89 for six months of use or $199 for a lifetime license.
Attackers could have also saved themselves some money by finding a discount code for the malware on BitRAT’s official Twitter profile.
Gill analyzed the malware and found that it relied on another digital threat for its code.
“While BitRAT has been around for years, it appears the developers of this latest version heavily utilized code from the WebMonitor RAT (RevCode) while adding extra functionality for more nefarious purposes in BitRAT,” he explained.
Back in April 2019, KrebsonSecurity wrote that a Swedish company called RevCode framed WebMonitor RAT as legitimate software “that helps firms and personal users handle the security of owned devices.”
But that didn’t prevent antivirus companies from detecting the program as malware. Security researchers found that program could dump a remote machine’s temporary memory, steal passwords from different email programs, make off with the machine’s Wi-Fi details, and gain access to the webcam—functions that only undermine “the security of owned devices.”
Defending Against an Email-Borne BitRAT Campaign
The malware operation discussed above highlights the need for organizations to defend themselves against email attacks. One of the ways they can do this is by investing in an email security solution that’s capable of scanning incoming messages for campaign patterns, malware signatures, and other threat indicators. It should perform this analysis in real time so that legitimate business correspondence can reach its intended destination.
Augment your defenses with the email threat detection tools from Zix | AppRiver.
