Zix Blocks Major Form & Survey Abuse Attacks Targeting Microsoft 365 Users

Over the past 24 hours alone, Zix/AppRiver advanced email threat protection filters have stopped over 88,000 messages attempting to abuse legitimate forms and survey services. The total count of blocked attacks jumps to an astonishing 590,000 messages over the course of the past week. These numbers provide a glimpse into just how pervasive living off the land attacks have recently become.
In July of 2019, we detailed how attackers were abusing Microsoft Office Excel & Forms Online Surveys to host credential harvesting sites on the service without the need for an external phishing site. These malicious schemes were on Microsoft's radar too, as they added increased automation for phishing detection to their roadmap in this same time period. Since then, attackers have rapidly warmed up to the idea of launching more Living Off the Land (LOtL) attacks by abusing a variety of legitimate form and survey providers.
Top Abused Providers & Metrics
Metrics derived from our advanced email protection filters for these LOtL attacks indicate they have increased over time. Currently, the highest volume of blocked messages abusing the legitimate providers in order from greatest to least volume are:
- Google Forms
- Microsoft Forms
- SurveyGizmo Surveys
- HubSpot Forms
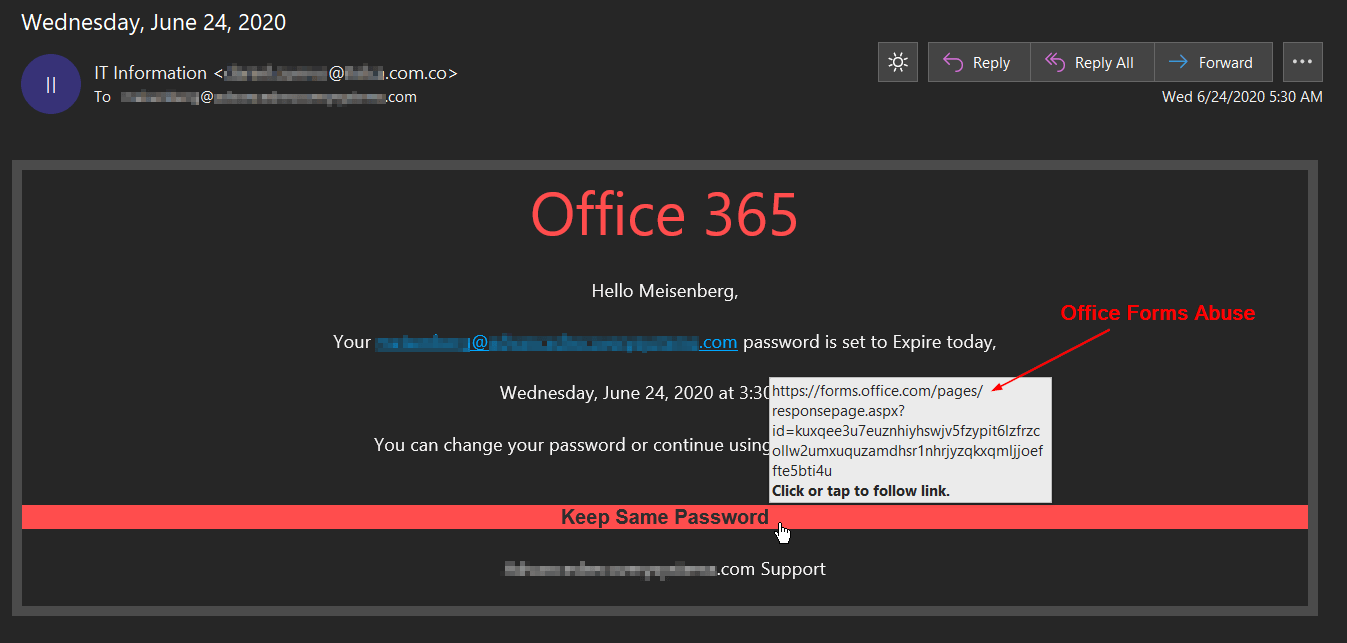
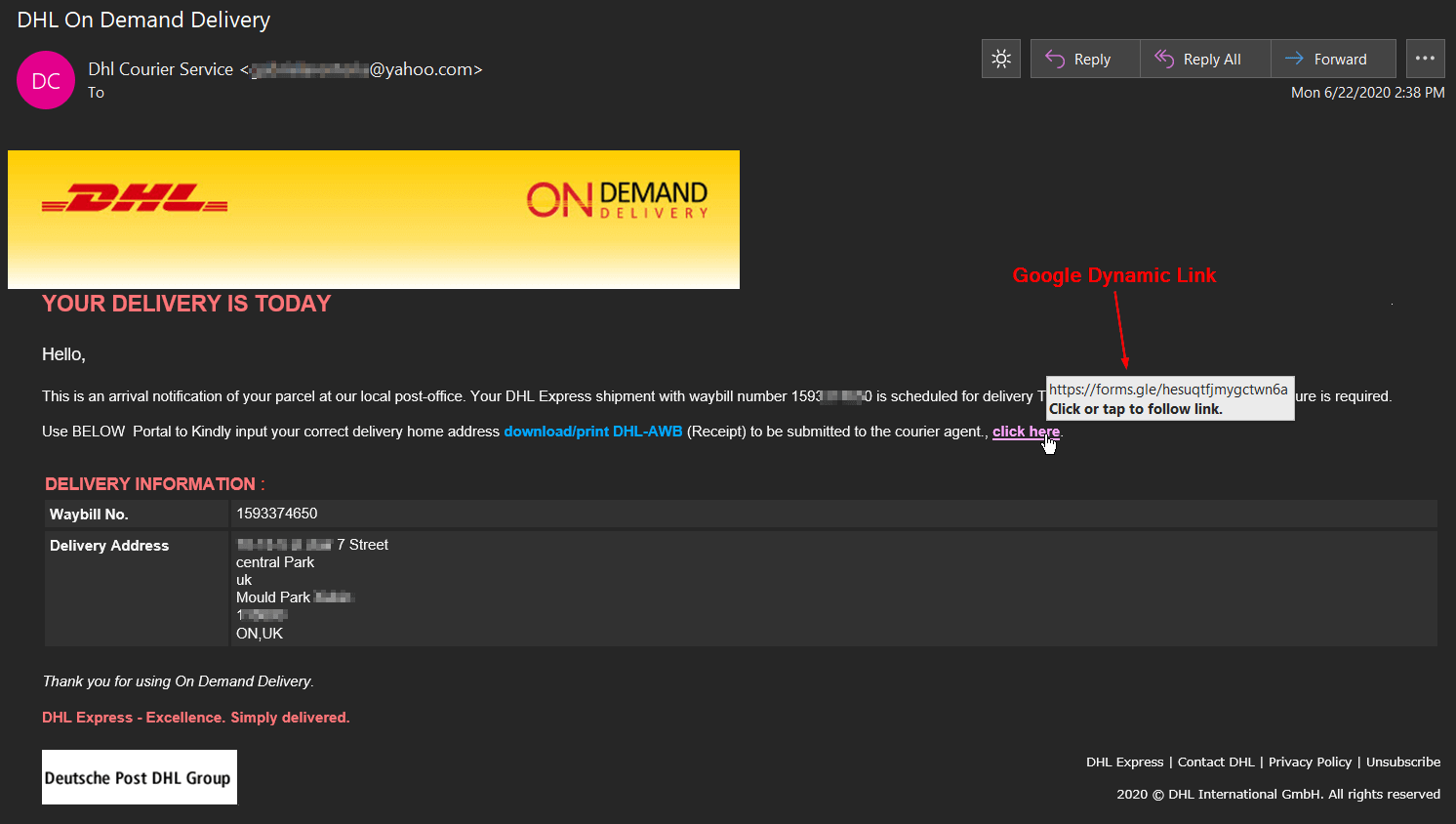
A Growing Trend to Intermediary Redirect/Jump Pages
While not a new tactic, there has been a growing trend by these attackers over the past months to utilize an intermediary redirect/jump page before the credential harvesting page. These threat actors still rely upon the legitimate provider for the initial link, but then attempt to either automatically redirect or trick the user into manually clicking onward to the page designed to solicit and steal user credentials.
This tactic is used for a variety of reasons:
- The most obvious - these links are for legitimate services, this helps to defeat user awareness training when looking for suspicious links.
- Certain providers are becoming more effective at identifying this type of abuse on their site and removing the page faster.
- Allows the attacker to autonomously switch phishing links in their email campaigns once the intermediary site is discovered and removed by the service. This allows the attacker to save time and resources from having to set up a new credential harvesting site. They can direct a bot to identify when the site is removed. Once removed, they automatically change the link in the sending scripts for continuity in the phishing campaigns to ensure continuity of the attack with little to no downtime.
Not already a Zix email threat protection customer? Learn how Zix’s advanced threat protection solutions can help keep your organizations safe against living off the land attacks.
