Samsung, Adobe and Oxford Abused in Office 365 Phishing Campaign

Security researchers discovered a new phishing campaign that abused Samsung, Adobe and Oxford services to steal victims Office 365 credentials.
Check Point Research observed that the campaign began when users at European companies or Asian/Middle Eastern entities received a “missed voice message” email.
Those responsible for the campaign leveraged spoofing techniques so that the attack emails appeared to originate from Voice Over Internet Protocol (VOIP). However, a closer look at the sender address revealed that the messages had originated from addresses belonging to different departments’ legitimate subdomains at the University of Oxford.
The security researchers at Check Point explained that the campaign had pulled off this spoofing tactic without having compromised any University of Oxford email accounts:
The email headers showed that the attackers found a way to abuse one of Oxford’s SMTP servers. The email originated from the NordVPN IP address 194.35.233.10 and then passed to the Oxford SMTP server and the Oxford Relay server…. Using legitimate Oxford SMTP servers allowed the attackers to pass the reputation check for the sender domain. In addition, there was no need to compromise actual email accounts to send phishing emails because they could generate as many email addresses as they wanted.
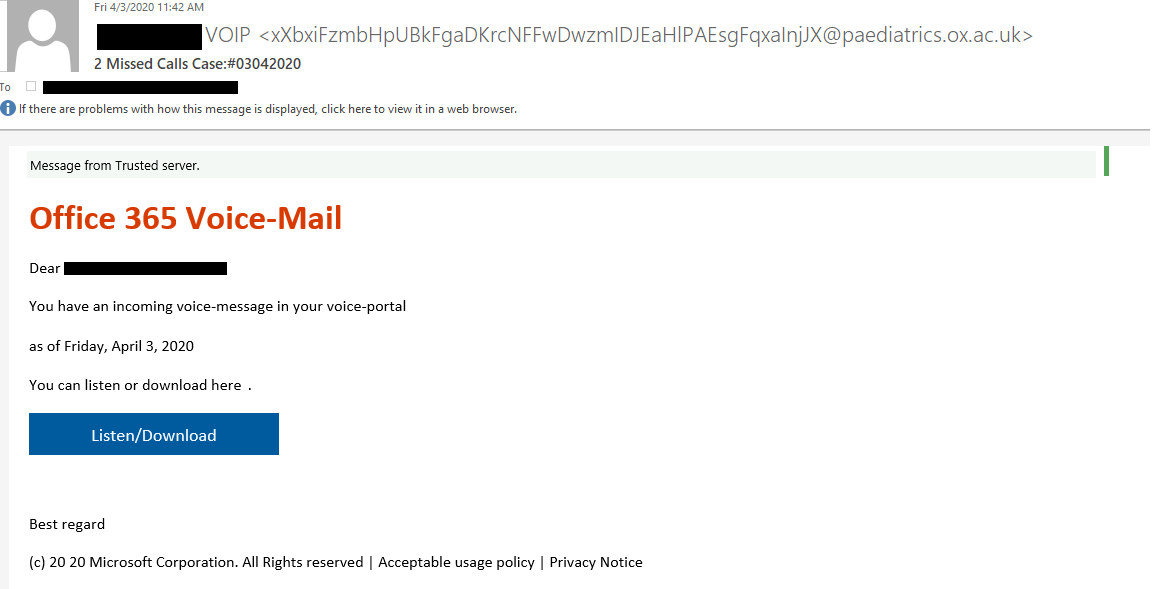
As seen in the above image, the attack emails attempted to trick recipients into clicking on a “Listen/Download” button. A link embedded in that button led the recipient to t.email1.samsung[.]ca, a subdomain for Samsung-Canada which hosted an Adobe Campaign server for redirecting users in email campaigns. This attack technique did not exploit a vulnerability, as neither Adobe nor Samsung were compromised. Instead, it merely exploited the fact that server was open to those outside of Samsung’s internal marketing efforts.
The redirection server identified above sent users to several WordPress sites that hosted malicious redirection code at the time of discovery, thereby furthering the likelihood that the campaign would go undetected by email security solutions. Those redirects ultimately led users to the final phishing kit hosted on yet another compromised WordPress website. Divided into multiple sections that were obfuscated using multi-byte XOR, the phishing page attempted to trick users into submitting their Office 365 credentials.
Other Recent Office 365 Phishing Attacks
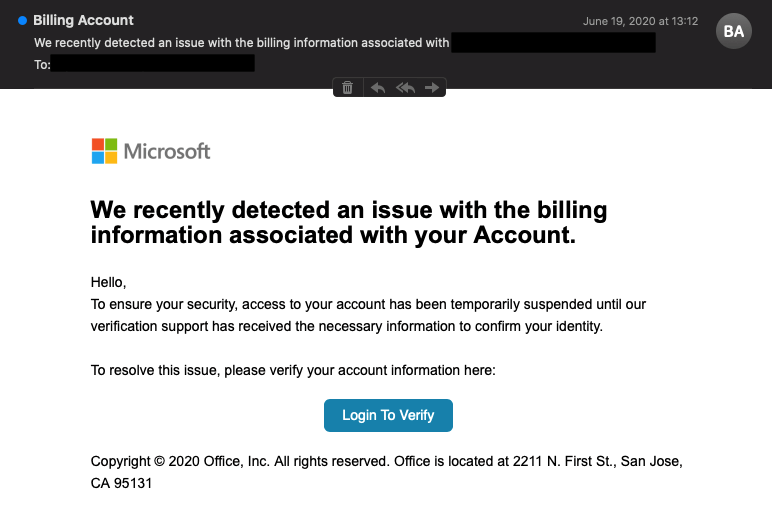
The campaign described above wasn’t the only recent operation through which malicious actors attempted to steal victims Office 365 credentials. In mid-June 2020, for instance, the Zix | AppRiver team came across a phishing email that pretended to come from Microsoft. In the message, the attackers claimed that the recipient needed to verify their billing information in order to access their account. The emails then instructed recipients to click on a “Login to Verify” button, which redirected them to a fake Outlook Web App (OWA) login page.
It was around that same time when Zix | AppRiver came across another phishing campaign whose attack emails appeared to come from the Outlook Web App but actually originated from what appeared to be a compromised email address based in Japan. Those attack emails warned users that they “are not receiving all [their] mails” and that they had seven pending emails in their inboxes. They then instructed users to click on a “View Here” button for the purpose of accessing those unread messages.
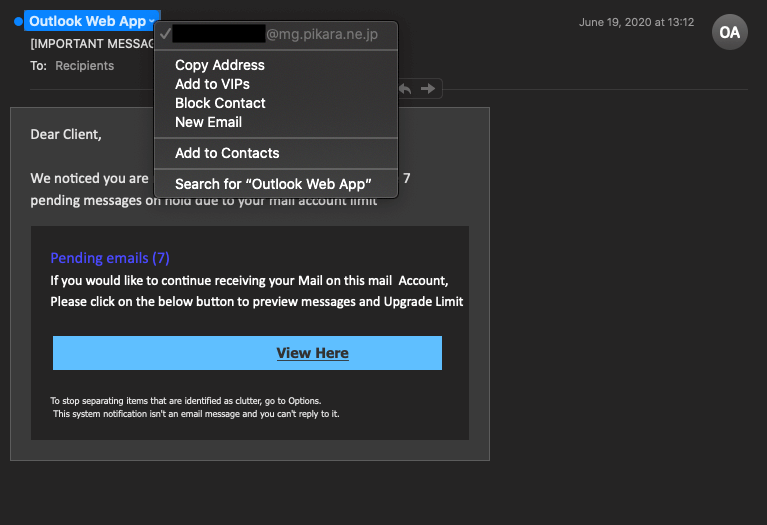
The poor grammar gave this email away as a fake. It’s therefore no surprise that the phishing email redirected the recipient to a fake OWA login site.
How to Defend Against an Office 365 Phishing Campaign
Organizations can defend themselves against phishing campaigns such as those described above by investing in their email security. They should specifically look to a solution that scans their incoming messages for indicators of known threat behaviors while allowing legitimate correspondence to make their way through.
Learn how Zix | AppRiver’s advanced threat protection capabilities can help.
