Attackers Exploiting Auto-Forwarding Rules to Conduct BEC Scams

Digital attackers are exploiting auto-forwarding rules to improve the success rate of their Business Email Compromise (BEC) scams.
A Warning from the FBI
On November 25, the FBI warned readers that digital criminals were setting up auto-forwarding rules on compromised email accounts.
Malicious actors made the choice to set up those rules solely on the web-based client of the affected email account. They did so with the assumption that administrators had failed to synchronize the web-based clients and the desktop clients of the organization’s email accounts, thereby potentially creating a lack of visibility.
The FBI expanded upon this threat in its alert:
While IT personnel traditionally implement auto-alerts through security monitoring appliances to alert when rule updates appear on their networks, such alerts can miss updates on remote workstations using web-based email. If businesses do not configure their network to routinely sync their employees’ web-based emails to the internal network, an intrusion may be left unidentified until the computer sends an update to the security appliance set up to monitor changes within the email application. This leaves the employee and all connected networks vulnerable to cyber criminals.
For how long is uncertain. The FBI explained that malicious actors could maintain access to a compromised email account even after a financial institution or law enforcement agency warned the affected organization of an attempted BEC scam. They could do this if the victim organization conducted a system audit that didn’t investigate both applications.
Some Context on Auto-Forwarding Rules in BEC Scams
This isn’t the first time that malicious actors have used auto-forwarding rules. Back in 2018, for instance, Zix | AppRiver discussed some BEC scams that it had helped to remediate.
In one of those attacks, affected users initially reported that they were not receiving any messages to their account. A support team lead at Zix | AppRiver subsequently investigated and found that attackers had infiltrated their email accounts and then created a series of mail rules to carry out their malicious activity. Those specifications forwarded all messages to accounts under their control, and they also deleted messages in order to conceal the attackers’ activity.
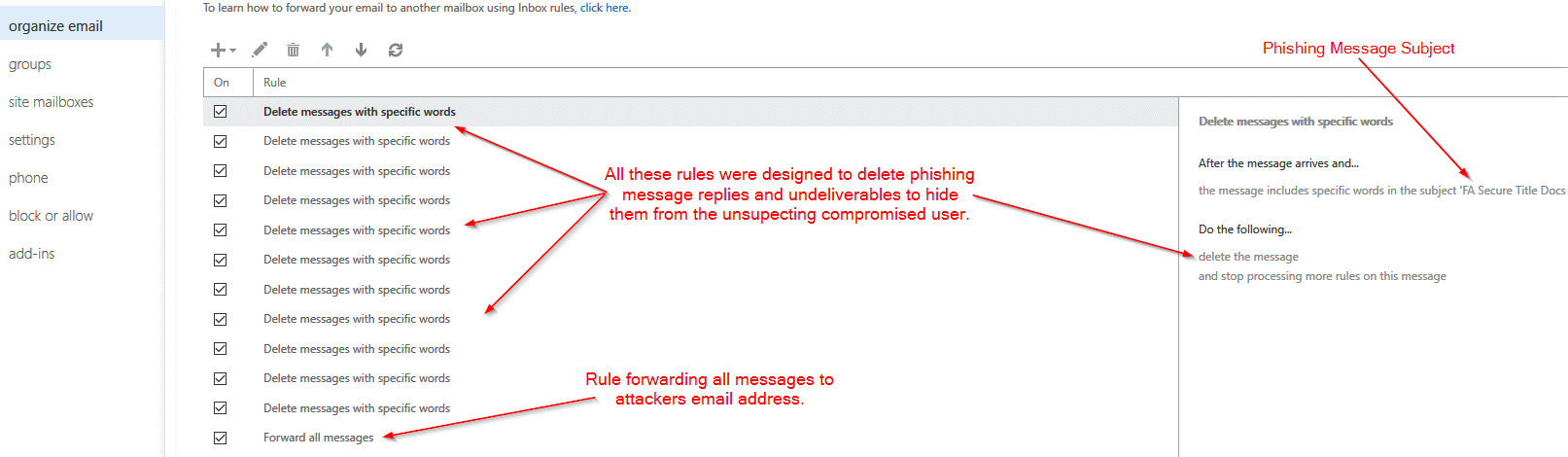
“We see evidence of this all the time,” explained Troy Gill, manager of security research at Zix | AppRiver. “This activity is often observed in the form of BEC attacks targeting our customers. These typically utilize email threads that have been captured by threat actors, often via the use of forwarding rules. Through this activity the threat actors are able to learn details of business relationships, often financial and exploit those relationships via the use of the forwarded emails.”
At that point, the attackers replied to the most promising emails while impersonating the owner of the compromised email account. They then used this disguise to supply “updated” billing details for financial accounts under their control and trick the other party into making a fraudulent wire transfer. All without leaving much of a trace of their deception—that is, aside from the auto-forwarding rules.
Defending Against BEC Scams
Gill recognizes the importance of defending against sophisticated BEC techniques such as those discussed above:
This is not new and has been a hotbed of activity for years. So much so that we developed our own tool which looks for evidence of this sort of activity along with verification of other security settings best practices. Running these routinely is highly recommended to help detect and mitigate this sort of activity.
Interested in receiving a complimentary security audit report of your organizations Office 365 workplace environment? Sign up using this form provided by Zix | AppRiver.
