Fraudsters Used Compromised SharePoint Links to Deliver Phishing Payloads

Digital fraudsters used compromised SharePoint links to deliver phishing payloads and thereby steal victims’ sensitive information.
At the end of July, Zix | AppRiver came across a phishing email in which digital fraudsters disguised themselves as Anthem Blue Cross Blue Shield. The attackers adopted that mask insofar as they included branding for Anthem’s HealthKeepers Plus health insurance plan. They also listed “Anthem Blue Cross Blue Shield” in the message’s signature field.
The attack email suffered from a discrepancy in reference to its sender information, however. Rather than listing “Anthem,” the sender field indicated that the message had arrived from “Microsoft Online.” A closer examination of that claim revealed that those responsible for sending the email address had used spoofing techniques to impersonate the Redmond-based tech giant. In reality, the email had originated from a compromised email account.
Ultimately, they used these disagreeing covers to inform the recipient that Anthem had encountered an issue when it had allegedly attempted to process a claim submitted by the recipient on July 21. They then instructed the recipient to sign into their account by clicking on a “View your message” URL and follow a series of instructions.

As seen in the image above, the “View your message” link did not direct recipients to a login portal for Anthem. Instead, it redirected them to a phishing site that was hosted on an otherwise legitimate SharePoint website at the time of discovery. This website prompted the user to submit their Microsoft account credentials along with their mother’s maiden name and their Social Security Number.
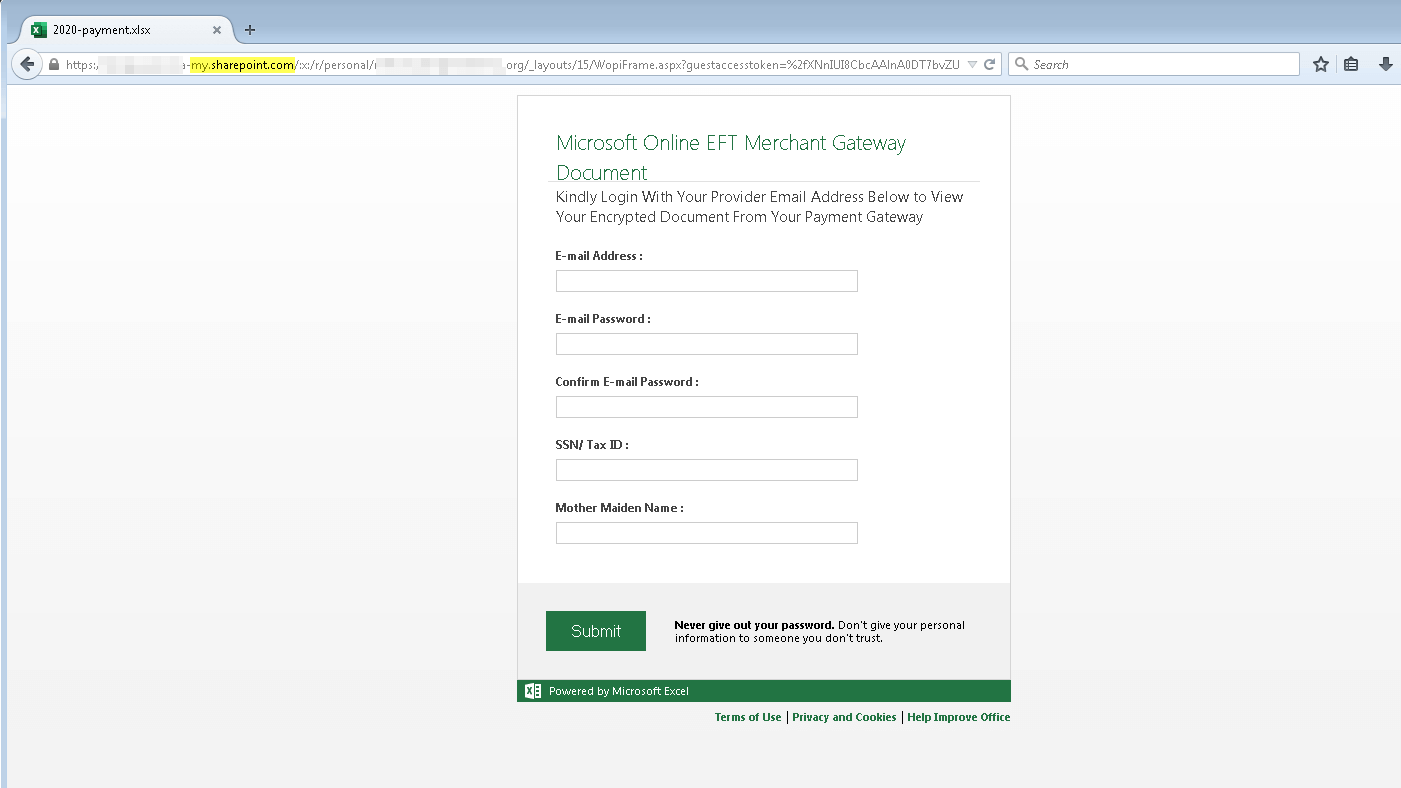
Ultimately, a malicious actor could have abused those details to authenticate themselves on their victim’s Microsoft account as well as to perpetuate identity fraud elsewhere.
Living off the Land with SharePoint
This wasn’t the first time that malicious actors incorporated SharePoint into a phishing campaign. Troy Gill, manager of security research at AppRiver, made this point clear:
SharePoint has been a consistent favorite of attackers for some time now. Attacks using SharePoint as a lure to gather credentials are a daily occurrence. We also see O365 used as a lure hitting our filters every day…. Wherever trusted brands can be used to facilitate trust, attackers will do so.
Malicious actors’ ongoing abuse of SharePoint constitutes a Living off the Land (LotL) attack in that they use legitimate services to distribute malware of phishing pages. As noted in AppRiver’s 2019 Global Security Report, nefarious individuals oftentimes take their efforts one step further by abusing SharePoint, Dropbox and other targeted platforms from previously compromised accounts. Doing so allows attackers to evade detection by email filters and to raise fewer red flags among their potential victims.
Living of the Land attacks aren’t a rare occurrence, either. In an AppRiver blog, senior cybersecurity analyst David Pickett explained that he and his fellow AppRiver researchers had stopped 88,000 messages abusing legitimate services over the course of a single day. This number broadened out to approximately 590,000 messages within the span of a week.
How to Defend Against a Phishing Email Abusing SharePoint
The prevalence of LotL techniques highlights the need for organizations to defend themselves against phishing emails that abuse SharePoint or other legitimate platforms. One of the ways they can do this is by investing in their email security. They should specifically look for a solution that can scan incoming messages for malware signatures, campaign patterns and other indicators of threat behavior while allowing legitimate correspondence to reach their destination.
Learn how Zix | AppRiver’s email threat protection can keep your organization safe.
