Threat Actor Continues CPA Attacks with Email Containing Driver’s License Images

A threat actor began using a new email containing what appears to be images of a legitimate driver’s license image in its ongoing efforts to target Certified Public Accountant (CPA) firms.
This attack comes from the same threat actor who impersonated a doctor and registered a hospital-related domain in one of their previous tax-related attacks.
Inside This Newest Attack Attempt
In the beginning of March 2021, the Zix | AppRiver team detected a malicious email sent out by the threat actor.
The email arrived with “Request for Tax Service” as its subject line, and it appeared to come from someone named “Jennifer” who was looking to work with the receiving CPA firm.
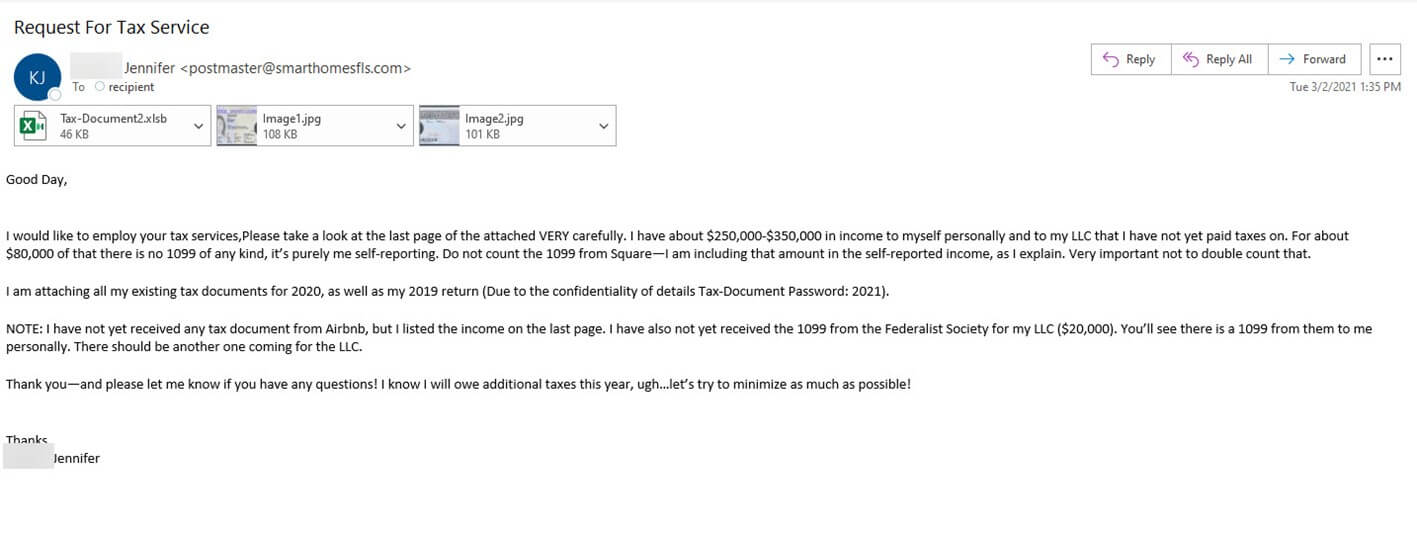
Screenshot of the attack email. (Source: Zix | AppRiver)
Within the message itself, “Jennifer” informed the CPA firm that she had yet to file taxes on $250,000-$350,000 paid to her personally as well as to her LLC.
Those responsible for crafting this email then broke down this figure and mentioned several recognizable sources of income in order to make their email sound convincing to the recipient.
As an example, they said that “Jennifer” had not received a 1099 tax form for $80,000 of the reported income, but they clarified that they were counting the 1099 tax form from American mobile payment company Square in their self-reported income.
They went on to say that they had not received a tax document from Airbnb and that they were waiting on a 1099 of $20,000 for their LLC from the Federalist Society.
All of this built up to the threat actors’ request that the CPA firm open the sender’s “existing tax documents for 2020, as well as [their] 2019 return.” They even provided a password in the text of their email for unlocking an .XLS file, something which users who are concerned about the “confidentiality of details” for an attached document should never do.
A Look at the Attached Documents
Ultimately, “Jennifer” did not send along what she promised. The threat actor only sent along a .XLS document and not anything resembling a 2019 tax return. That Excel document, named “Tax-Document2.xlsb,” followed the threat actor’s usual pattern of delivering a remote access trojan for the purpose of covertly stealing sensitive personal and financial data.
What’s curious is that the threat actor decided to send along images of a driver’s license despite not mentioning it in the email. Even more curious is that those images appeared to be of a real driver’s license issued to someone named “Jennifer” in the State of Virginia—complete with a signature on both the front and back sides.
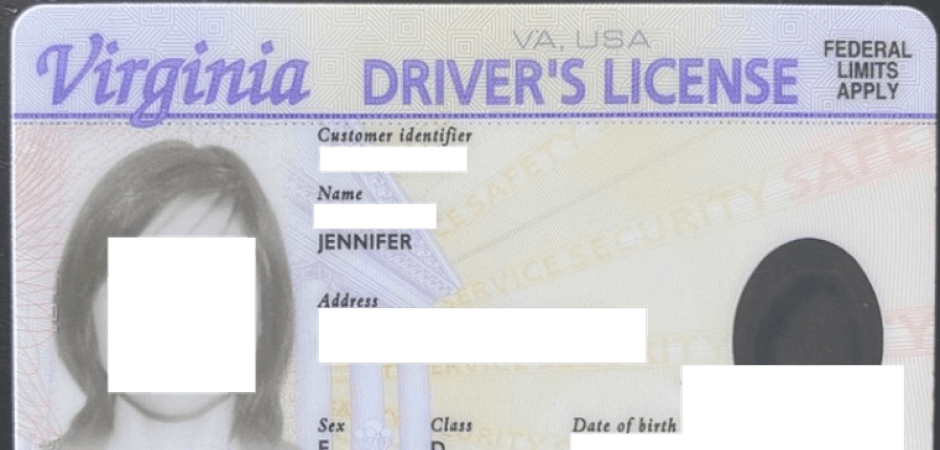
Screenshot of the front of “Jennifer’s” driver’s license. (Source: Zix | AppRiver)

Screenshot of the back of “Jennifer’s” driver’s license. (Source: Zix | AppRiver)
It’s unclear from this attack how the threat actors came into possession of the driver’s license.
That being said, the threat actors could have stolen the license if it was exposed in a data breach and published online. They then might have sent along the license as proof of identity in order to trick the CPA firm into opening the .XLS document. Depending on the data stored in that file, that might have been enough to trick the firm into filing a fraudulent tax return for “Jennifer.”
Defending Against Tax-Related Email Scams
The scam discussed above highlights the need for organizations to defend themselves and their employees against email attacks this tax season. One of the ways they can do that is by investing in a security solution that analyzes incoming email messages for indicators of malicious activity while allowing legitimate correspondence to reach its intended destination.
Learn how the email threat protection solutions of Zix | AppRiver can do just that.
