Zoom users in attackers’ crosshairs
The global health crisis that we are all facing has presented incredible challenges for people and for organizations. And it has accelerated a move to the cloud dramatically. As we all rise to the occasion to meet this challenge also be mindful of the opportunities that this crisis has afforded cybercriminals.
Enabling a secure, remote workforce is critical as attackers will attempt to exploit every new possibility that presents itself. We have already seen a bevy of email-based attacks looking to capitalize on this crisis and there will be many more to come.
As a result of the global social distancing measures put in place, businesses have rushed to tools such as Zoom to keep their workforce productive and engaged. In fact, it was recently reported that the Zoom service was seeing an average of 200 million daily users in March, up from 10 million daily users as recently as December.
They are not the only ones.
Cybercriminals are also looking to Zoom – but for criminal reasons. During the past month cybercriminals have been observed registering thousands of new domain names including the word “zoom” which they intend to use to deliver phishing and malware attacks.
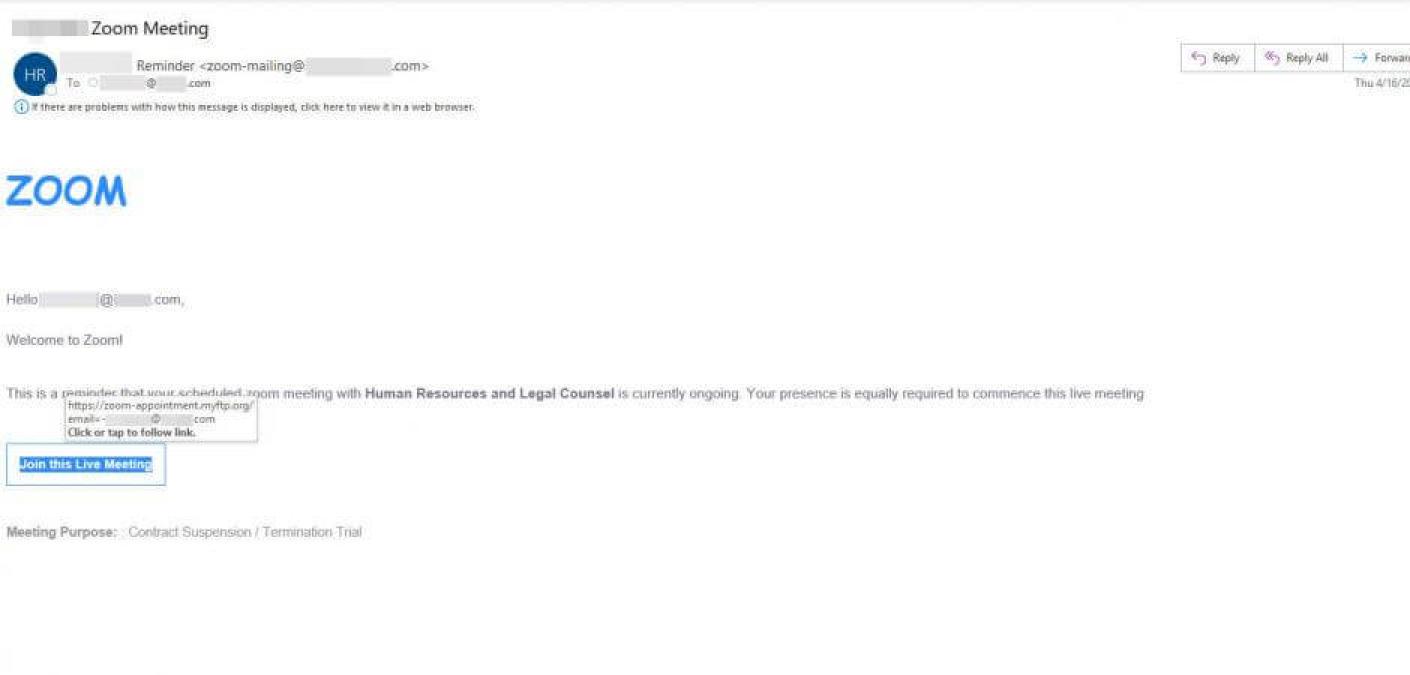
Many of these attacks are crafted well enough to fool even seasoned Zoom users but we wanted to pluck one from the quarantine and examine it a little closer so that everyone knows what to be on guard against. The email itself was posing as a notification that a scheduled Zoom meeting with Human Resources and Legal Counsel already has begun.
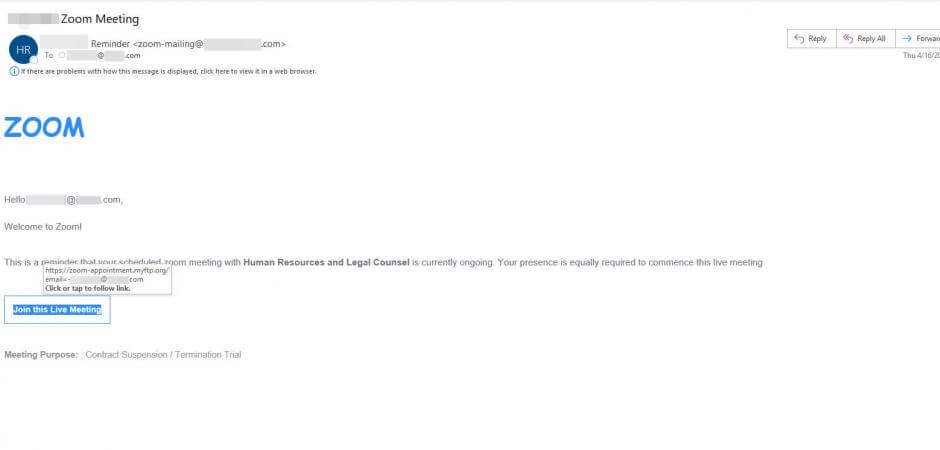
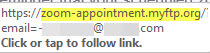
This theme does a good job in creating the urgency that attackers often aim for. The savvy Zoom veteran might notice the difference in the Zoom logo font in the body of the message. When hovering over the link to inspect closer, as everyone should be doing before they click on ANY link, you should notice that the domain in the email link does not lead to zoom.us, which should be a huge red flag to everyone.
Clicking on the link leads to a well-designed phishing page designed to harvest email credentials.