6.5 Billion Emails Quarantined in 2021

The Zix | AppRiver team quarantined 6.5 billion emails in 2021, a volume which constituted a 12.5% increase over the previous year.
A Year of Email Attacks in Review
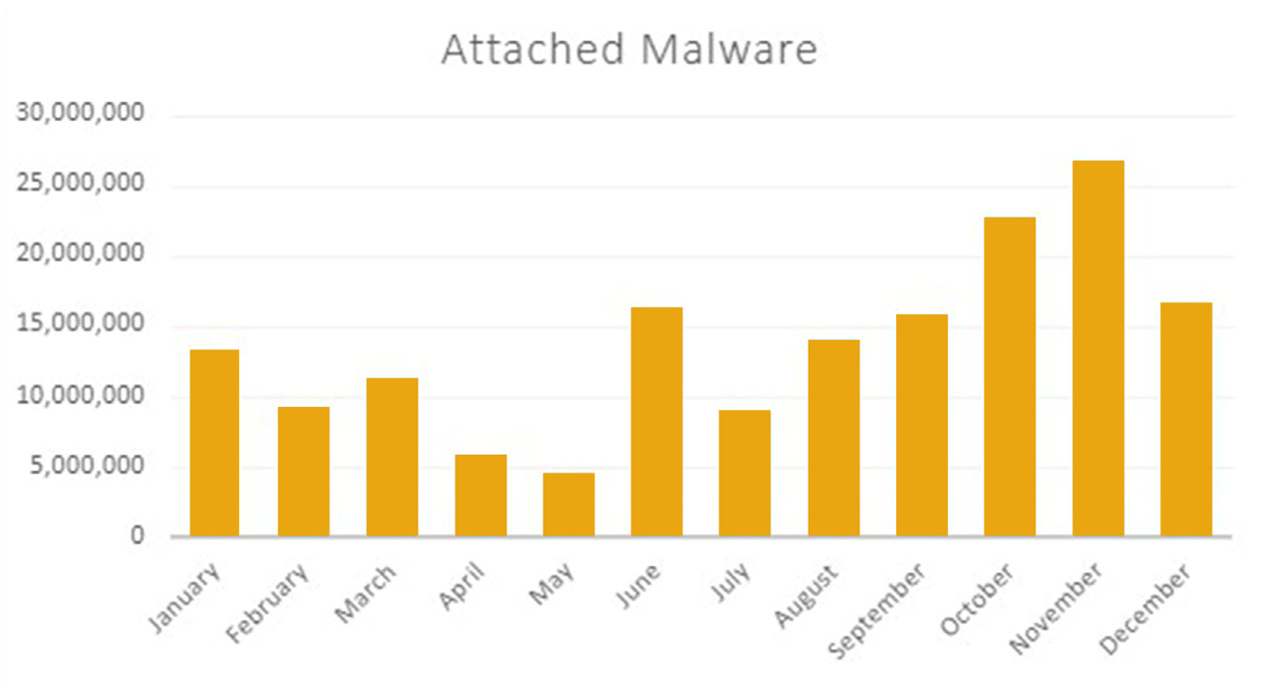
In its “Global Threat Report: Full Year 2021,” Zix | AppRiver revealed that emails with malware attachments decreased in volume to below five million during the first five months of the year. Those messages jumped up above 15 million the following month and ended at around the same level in December 2021. That was after the team detected over 25 million emails with attached malware samples in November.
Overall, the Zix | AppRiver team flagged 165 million email messages with malicious attachments through 2021.
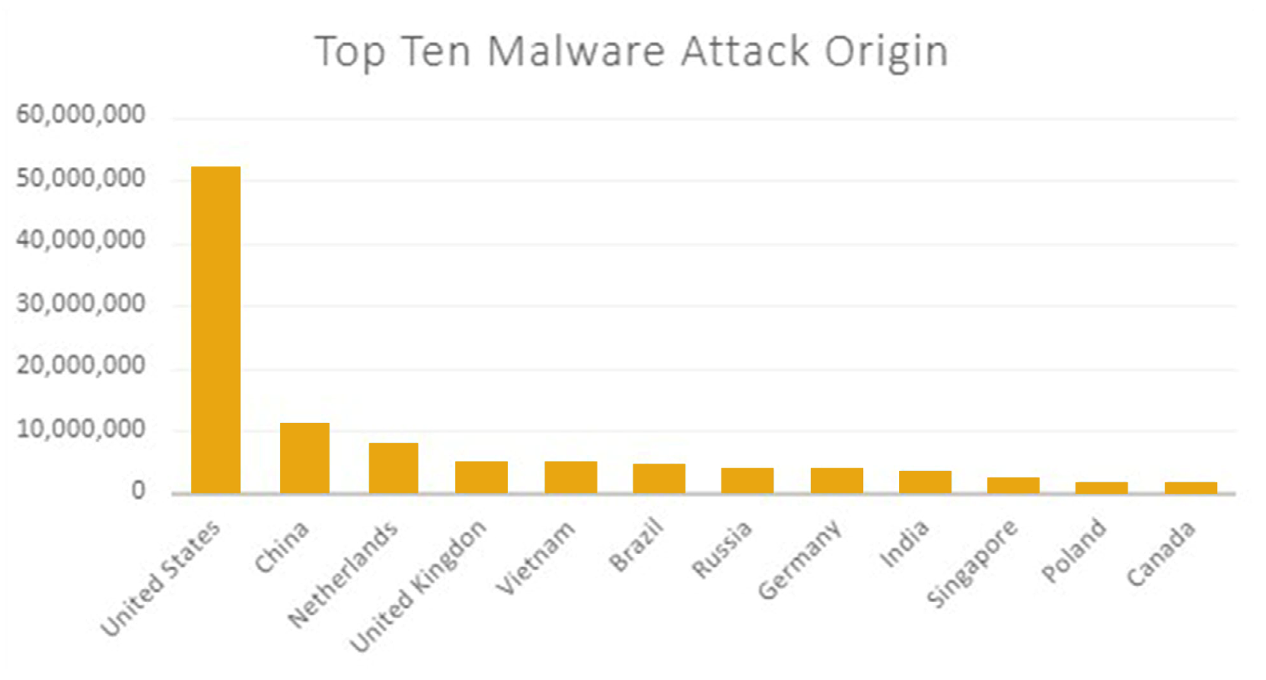
When it examined the origins of these and other malware attacks, the Zix | AppRiver team observed that many of the email campaigns had originated from the United States. China came in with the second highest number of attacks at just over 10 million. This attack volume marked a growth rate of 240% for the country when compared with 2020.
Zix | AppRiver also examined the most common attachment file types used by email attackers in 2021. Excel worksheets were the most common. Even so, malicious HTM/HTML attachments increased throughout the entire year.
Sources of Inspiration for Their Attacks
The Zix | AppRiver team witnessed malicious actors seize on various events as inspiration for their attacks in 2021. Let’s examine a couple of these below.
The Kaseya Supply Chain Attack
Following the software supply chain attack involving Kaseya in July 2021, Zix | AppRiver detected a malicious email that claimed to be offering a patch for the affected software product. The attack email instructed the recipient to open an attached executable file for the purpose of resolving a Kaseya weakness. Once executed, the file loaded Cobalt Strike, commercially available pentesting software which malicious actors can weaponize as an attack tool.
Global Shipping Issues
Several months later, the researchers at Zix | AppRiver detected an attack campaign that claimed to originate from Maersk Line. The message used stolen branding to trick the recipient into thinking that the email had originated from the shipping company. From there, the email instructed the recipient to view some documents including an invoice, a bill of lading, and a packing list by clicking on a “Download Confirmation” button. If the user complied, the campaign redirected them to a phishing page designed to steal their email account credentials.
Email Attack Predictions for the Year Ahead
Looking forward to 2022, the Zix | AppRiver team has several predictions for where email attacks will go. First, they noted that there will be greater coordination between threat groups. The researchers witnessed such collusion following Emotet’s takedown in 2021. Trickbot’s operators stepped up and began distributing Emotet later in the year. This activity helped malicious email traffic involving Emotet to increase beginning in mid-November.
Second, the Zix | AppRiver team anticipates that attackers will make more attempts to target software supply chain attacks like Kaseya. Doing so will help malicious actors to broaden their impact to dozens if not hundreds or even thousands of companies with a single compromise.
Finally, researchers at the security firm wrote that digital criminals are going to continue turning to spear-phishing attacks in 2020. Such activity will support attackers as they devise new customization tactics—all for the purpose of focusing even further on their targets.
Email Defense for 2022
The predictions discussed above highlight the need for organizations to invest in their email threat protection over the following year. They need to prioritize building more specificity into their email defenses. Towards that end, they could consider investing in an email security solution that’s capable of scanning incoming messages at multiple levels for the purpose of blocking email attacks while allowing legitimate correspondence to reach their destination.
